-
Content Count
10636 -
Joined
... -
Last visited
... -
Days Won
1778
Posts posted by Staff
-
-
Hello!
Thank you for the suggestion. Flexible and useful filters are implemented in Eddie Android edition and the AirVPN Suite, but not in Eddie Desktop edition. Surely a recommendation which we will forward to Eddie Desktop developer, thanks. In the meantime you can consider to "white list" countries to make a first rough selection, and then white list servers inside those countries. Each list can be sorted by country or server name. Not exactly what you need but it's something comfortable anyway.
Kind regards
-
2 hours ago, nexsteppe said:Putting the general safety of any Google service aside, is there any compelling reason why they rolled their own variation of IPsec for Google One rather than build on OpenVPN?
I doubt anyone was seriously considering WireGuard when they first rolled this out for Fi users back in 2019, so I get that much.
But why IPsec? Particularly for mobile devices?
It's difficult to know the whole story because Google is a major participant of the PRISM programs. NSA CIA and other analysts can anytime access all Google relevant database without court orders, so some technical solution might be picked to make life easier to let NSA, CIA analysts access Google based db and keep data consistency and veracity for each person regardless of Google VPN usage.
Kind regards
-
11 hours ago, rx_man123 said:Then why do keys still need to be re-generated?
"Our clients can renew their keys whenever they want, forcing a new, random IP address reassignment"
Hello!
Because only in this way you change VPN IP address, as already explained.
Kind regards
-
1 hour ago, SeUbHS said:
Worked a treat, thanks! Just curious: why do I need to bypass connecting to the bootstrap servers? Is t-mobile blocking the connection to them specifically in addition to blocking UDP traffic or something?
Hello!
We're very glad to hear that the suggestion by support team worked.
We don't know for sure, and we can imagine three potential, alternative explanations:
1) All the bootstrap servers IP addresses have become known and they are blocked. Unlikely explanation: if you have tested our "secret" bootstrap servers, we think that T-Mobile can not know them.
2) The specific connection used by Eddie (HTTP) is blocked when the underlying payload is encrypted. Eddie encrypts data to the bootstrap servers and then sends them over plain HTTP: in the past it was a good method to bypass certain blocks. Of course data coming back are encrypted by the servers.
3) Direct access via HTTP(S) to IP addresses (in place of domain names) is blocked (not uncommon in various filter methods). To cross-check you may enter a name as secret bootstrap server (for example airvpn.org) in Eddie's Android edition settings.
Kind regards -
Hello!
The paper re-launches the anti-censorship abilities of OpenVPN over SSH which we proposed 13 years ago! It had a filter rate of 0.32, the third best outcome in the world, very remarkable and putting AirVPN in the top 3 worldwide best filtering escaping VPN. As usual we anyway recommend Tor with private obfs bridges to reach filter rates next to 0. We have invested a lot on Tor and the solution is free for everyone. In Iran and Russia Tor obfs and private bridges are instrumental against blocks.
Kind regards
go558a83nk and Lee47 reacted to this -
Hello!
From the support team in reply to a ticket mentioning this problem with T-Mobile:QuoteHello and thank you for your choice!
We confirm that we receive reports of all sorts of troubles from T-Mobile customers. Please try a connection with Eddie Android edition but with a profile, so that the bootstrap servers are bypassed. Make sure you generate a profile (in our Configuration Generator) for OpenVPN, protocol TCP, port 443, entry-IP address three. Then, import the profile in Eddie Android edition, and perform the connection through that profile (if in doubt, re-check the instructions to connect via OpenVPN profile, chapter 5 here: https://airvpn.org/android/eddie/
We're looking forward to hearing from you.
Kind regards
AirVPN Support Team
Kind regards
-
Hello!
We have noticed only now that this thread contains ads for Azire. Please, at least do not link their promotional messages and press releases! Links now have been removed. The whole forum is meant to report first hand experiences from other VPNs freely but it's not meant to advertise them. Momentarily locking to re-consider the whole forum.
Kind regards
-
On 7/7/2023 at 4:18 AM, Flx said:@StaffAny update(s) on this Road to 2.6?
Hello!
If you read https://airvpn.org/road_to_openvpn26/ you will notice that the beta testing phase will end when DCO is stable. Current reported status is:** NOTE ** ovpn-dco is currently under heavy development, therefore neither its userspace API nor the code itself is considered stable and may change radically over time.
Under the condition of code 1) not stable and 2) subjected to radical changes it is not possible to consider the beta testing phase over.
Kind regards
-
@russellr50
Hello!
That's fine and intended, the Network Lock activation button must disappear during a connection for good reasons. Please verify that the button is visible while Eddie is NOT "connected" as expected in 2.21.8 and report at your convenience. For the readers: the bug detected in this thread is different and affects 2.23.
Kind regards
-
1 hour ago, russellr50 said:Ver. 2.21.8, which is what the site directed me to download. My OS is Win 10. I realize this particular thread relates to the Mac OS, but you directed me to this thread from a support request I'd sent because my issue was similar.
Hello!
Thank you. We could not manage to reproduce this issue in 2.21.8. It's puzzling because 2.21.8 was released more than a year ago and this problem was never reported by anyone. Can you send us a screenshot showing the main window without the "Activate Network Lock" button?
Kind regards
-
1 hour ago, russellr50 said:I installed Eddie for the first time yesterday and there was no "activate network lock" option.
Hello!
Which Eddie version exactly, please? Can you also specify your OS name and version?
Kind regards
-
Hello!
We have used a lot of resources in the last decade to support Tor and Tor Project, and our main recommendation is always the same: rely on Tor first and foremost, using Tor bridges with various Pluggable Transports when necessary (for example from Iran they are now the only remaining resource to bypass blocks). Tor bridges are available even in Android (easy configuration with Tor Browser or Orbot).
Regardless of any "super-obfuscating-protocol" we may propose, any regime can collect our IP addresses and block them all. Thanks to volunteers, the every day addition of new Tor bridges with new IP addresses, as well as the addition of private unlisted Tor bridges, makes the regime lackeys "job" much more difficult. The flexibility of the addition of nodes and IP addresses worldwide in this case beats any possible commitment of a single, small private company. See also:
https://tb-manual.torproject.org/circumvention/
Kind regards
-
@OpenSourcerer
Hello!
Thanks a lot. It seems a bug indeed @Clodo - feel free to report it on the Eddie 2.23 testing thread, where we try to gather all the detected bugs.
@britishstyle
Can you see the "Activate Network Lock" button on Eddie's main window?
Kind regards
OpenSourcerer reacted to this -
11 hours ago, 48oift]h[ow94]8q2w3l said:Did anyone solve this yet? I have the exact same setup issue with Nginx and Gluetun. Works fine locally but can't get it to work remotely
Hello!
Yes, various users found the problem in their configuration, you may check whether their solutions are applicable for your case too:
https://airvpn.org/forums/topic/56370-portforwarding-not-working-gluetun-and-desktop-app/?tab=comments#comment-223375
https://airvpn.org/forums/topic/56288-proper-way-to-set-up-airvpn-wireguard-with-portforwarding-in-a-docker-with-gluetun-on-nas/?tab=comments#comment-222853
Also consider to contact Gluetun community as Gluetun supports AirVPN.
Kind regards
-
@VinXI
Hello!
The screenshot has cut out the option which does exist but has not been documented in the guide. We're glad to know that you have found it.
As @overbuilt985 pointed out, it does not work all the times when you use WireGuard and you turn off and on the network and under other sleep conditions. While WireGuard becomes more refined, we are confident that this problem will be mitigated. Development team is also informed. If you switch to OpenVPN at the moment you will have a much more accurate network control.
Kind regards
-
On 8/6/2023 at 4:59 PM, VinXI said:That is odd that in the recent version the option of "VPN reconnection" is not there.
Hello!
Please note that automatic re-connection is an option that's available from Eddie Android edition 1 throughout Eddie Android edition 3.0. Which version are you running? Check Settings > VPN > VPN reconnection and make sure you enable Always on VPN and Block connections without VPN to prevent any possible leak during re-connections (please read the instructions if needed).
Kind regards
-
Hello!
Paper of Tunnelcrack attack: https://www.usenix.org/system/files/usenixsecurity23-xue.pdf
First quick reply, we might add information in the future. The Tunnelcrack can be finalized with two different attacks: LocalNet and ServerIP, provided that:- the victim connects to a network fully controlled by the attacker (for Localnet attack)
- the victim DNS queries are poisoned and the attacker has all the features of an "on path" attacker (for ServerIP attack)
LocalNet attack
If you are in a WiFi unencrypted or not trusted (even if encrypted) network, or you are in an untrusted network in general (including Ethernet) prevent LocalNet attack by not allowing communications within the local network. This is default option in Eddie's Network Lock (please make sure that Allow LAN is not checked in Preferences > Network Lock settings window), while the AirVPN Suite for Linux allows this traffic by default so do not use it in untrusted network until we implement the option to block local network. Eddie Android edition forbids local traffic by default but you can enable this option in the Settings. Make sure you do NOT enable it when the device is connected to an untrusted network.
ServerIP attack
ServerIP attack requires DNS poisoning/spoofing, so Eddie Desktop Edition and Bluetit/Goldcrest are immune. It's mainly up to the local system to use reliable DNS (consider DNS over TLS or DNS over HTTPS) and protect the queries, but for additional safety use profiles with only IP addresses, and not host names, if you run directly OpenVPN, WireGuard, Hummingbird, or any other software needing profiles. Our CG will generate profiles with country domain names, so avoid country selection but prefer single server selection, or secure your DNS queries. When you select specific servers, the CG will insert IP addresses for the servers and not names. Eddie Android edition and the AirVPN Suite resolve domain names if you order a connection to a country, so avoid this type of connection. It is planned that next release will no more use country domain names.
Once inside the VPN, ServerIP attack variation with "route hijack" (described in an old paper) fails in AirVPN (even if you query the VPN DNS) because the DNS server address matches the VPN gateway address.
TL;DR
The Tunnelcrack attack can be easily defeated by not allowing communications with the local network when you are in an untrusted network and by using secure DNS or direct IP addresses to point to VPN servers when you start the VPN connection. All of the above can be easily obtained with our service or it is already implemented by default.
Kind regardsAir4141841 reacted to this -
-
Hello!
Activate Network Lock before you start a connection by clicking the big button on the main (overview) window: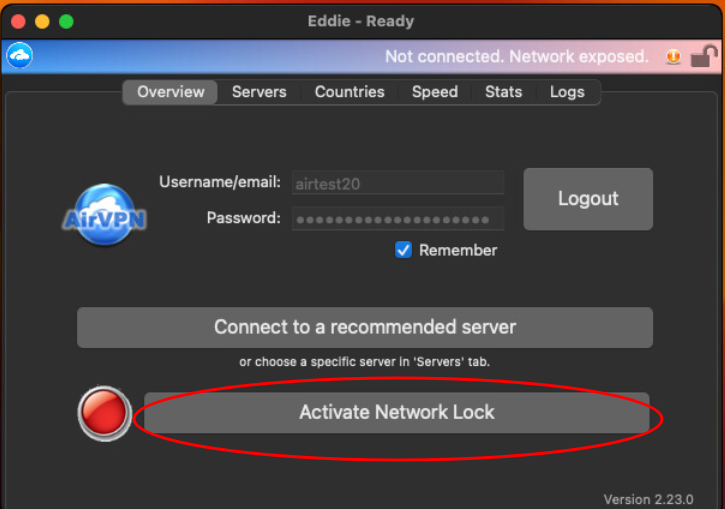
Or tell Eddie to activate Network Lock as soon as Eddie itself starts with the following option in "Preferences" > "General":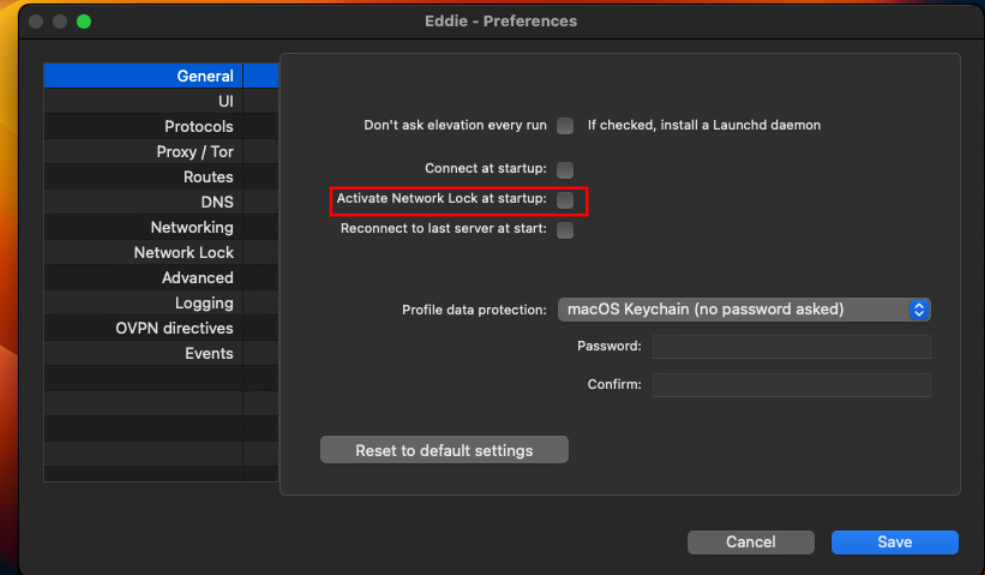
NOTE: starting from Eddie 2.23.0 (and NOT in any previous version), by default Network Lock is enabled during a connection and disabled at the disconnection, if it is not explicitly activated. This behavior is set by the "Ensure in session" item in "Preferences" > "Network Lock" window (enabled by default). If Network Lock is explicitly activated then it remains active as long as Eddie runs, and is de-activated as soon as Eddie is properly shut down or Network Lock is explicitly disabled from the main window.
Kind regards
-
Hello!
Please delete all Eddie's local data (not only the cache, all data) from the app settings menu of your FireStick. You will then need to re-enter your AirVPN credentials at the next run. Alternatively uninstall and re-install Eddie. Starting from Eddie 3.0 the Master Password is disabled by default and opt-in.
Kind regards
-
Hello!
Your proxy is not responding, or maybe it is refusing connections. Check the settings in the "Preferences" > "Proxy / Tor" window. Don't use an additional proxy unless it is absolutely necessary (for example if you are behind a proxy). We infer that you configured a connection over some proxy, without credentials, from the entry which we can sneak on the screenshot you posted. For a more complete analysis please post the whole system report. Please see here to do so: https://airvpn.org/forums/topic/50663-youve-been-asked-for-a-support-filesystem-report-–-heres-what-to-do/
Kind regards
-
New record! 1.02 Gbit/s on Haedus (2.04 Gbit/s on server's side for a single client).
Kind regards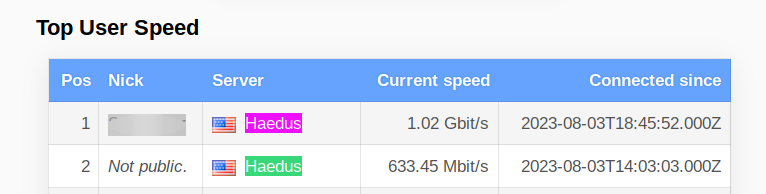
ScanFarer and go558a83nk reacted to this -
Hello!
The Windscribe interface is causing a critical error to OpenVPN. To solve the problem please see here: https://airvpn.org/forums/topic/53451-after-airvpn-changed-a-device-it-was-unable-to-connect-normally/?do=findComment&comment=194389
Kind regards
-
1 hour ago, Nidus11857 said:I switched to openvpn connect and yeah it worked on its own
Hello!
Yes, because you generated profiles for openvpn-connect with the new keys you have created. Each time you change keys, you need the new profiles, obviously (as the previous ones contain the old keys...). With Eddie Desktop edition, to update the keys just follow the simple procedure specified the instructions, which is necessary each time you renew your keys or create new keys. In general, read the documentation.
Kind regards



Google VPN
in Other VPN competitors or features
Posted ...
Hello!
We did not want to imply that. IPsec is widespread and remains a protocol suite of paramount importance. Together with some tunneling protocol such as L2TP it also provides a variety of VPN solutions both in a host-to-host transport mode and in a network tunneling mode. Under many aspects, IPsec offers a variety of solutions which OpenVPN does not offer (WireGuard can not even be mentioned as it is too rudimentary). AirVPN does not need them, but they are very important for so many companies.
Unfortunately, even nowadays, legitimate suspicions that IPsec was targeted by the Bullrun program suggest a very cautious approach to IPsec. AirVPN discarded IPsec in 2010 for legitimate suspicions which became more and more substantiated after Snowden's "revelations" (AirVPN predicting the risks of IPsec three years in advance was a mixture of careful inside considerations and luck/ability to select the correct rumors among the background noise in 2009 and 2010). See for example https://en.wikipedia.org/wiki/IPsec#Alleged_NSA_interference
Kind regards