-
Content Count
10647 -
Joined
... -
Last visited
... -
Days Won
1780
Posts posted by Staff
-
-
@VinXI
Hello!
The screenshot has cut out the option which does exist but has not been documented in the guide. We're glad to know that you have found it.
As @overbuilt985 pointed out, it does not work all the times when you use WireGuard and you turn off and on the network and under other sleep conditions. While WireGuard becomes more refined, we are confident that this problem will be mitigated. Development team is also informed. If you switch to OpenVPN at the moment you will have a much more accurate network control.
Kind regards
-
On 8/6/2023 at 4:59 PM, VinXI said:That is odd that in the recent version the option of "VPN reconnection" is not there.
Hello!
Please note that automatic re-connection is an option that's available from Eddie Android edition 1 throughout Eddie Android edition 3.0. Which version are you running? Check Settings > VPN > VPN reconnection and make sure you enable Always on VPN and Block connections without VPN to prevent any possible leak during re-connections (please read the instructions if needed).
Kind regards
-
Hello!
Paper of Tunnelcrack attack: https://www.usenix.org/system/files/usenixsecurity23-xue.pdf
First quick reply, we might add information in the future. The Tunnelcrack can be finalized with two different attacks: LocalNet and ServerIP, provided that:- the victim connects to a network fully controlled by the attacker (for Localnet attack)
- the victim DNS queries are poisoned and the attacker has all the features of an "on path" attacker (for ServerIP attack)
LocalNet attack
If you are in a WiFi unencrypted or not trusted (even if encrypted) network, or you are in an untrusted network in general (including Ethernet) prevent LocalNet attack by not allowing communications within the local network. This is default option in Eddie's Network Lock (please make sure that Allow LAN is not checked in Preferences > Network Lock settings window), while the AirVPN Suite for Linux allows this traffic by default so do not use it in untrusted network until we implement the option to block local network. Eddie Android edition forbids local traffic by default but you can enable this option in the Settings. Make sure you do NOT enable it when the device is connected to an untrusted network.
ServerIP attack
ServerIP attack requires DNS poisoning/spoofing, so Eddie Desktop Edition and Bluetit/Goldcrest are immune. It's mainly up to the local system to use reliable DNS (consider DNS over TLS or DNS over HTTPS) and protect the queries, but for additional safety use profiles with only IP addresses, and not host names, if you run directly OpenVPN, WireGuard, Hummingbird, or any other software needing profiles. Our CG will generate profiles with country domain names, so avoid country selection but prefer single server selection, or secure your DNS queries. When you select specific servers, the CG will insert IP addresses for the servers and not names. Eddie Android edition and the AirVPN Suite resolve domain names if you order a connection to a country, so avoid this type of connection. It is planned that next release will no more use country domain names.
Once inside the VPN, ServerIP attack variation with "route hijack" (described in an old paper) fails in AirVPN (even if you query the VPN DNS) because the DNS server address matches the VPN gateway address.
TL;DR
The Tunnelcrack attack can be easily defeated by not allowing communications with the local network when you are in an untrusted network and by using secure DNS or direct IP addresses to point to VPN servers when you start the VPN connection. All of the above can be easily obtained with our service or it is already implemented by default.
Kind regardsAir4141841 reacted to this -
-
Hello!
Activate Network Lock before you start a connection by clicking the big button on the main (overview) window: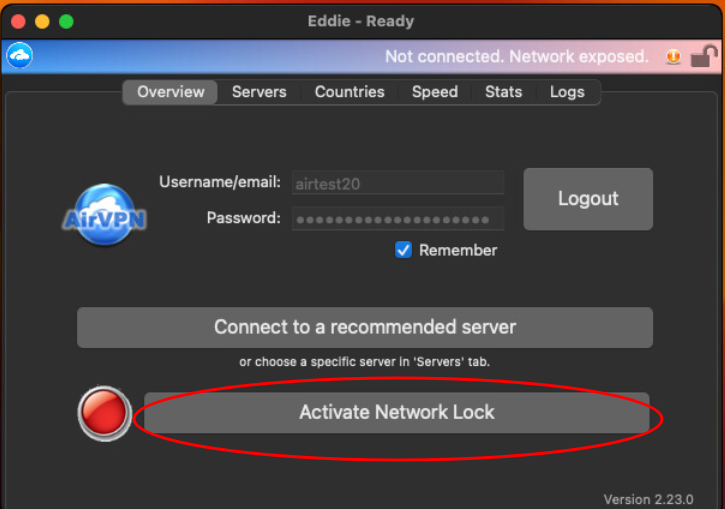
Or tell Eddie to activate Network Lock as soon as Eddie itself starts with the following option in "Preferences" > "General":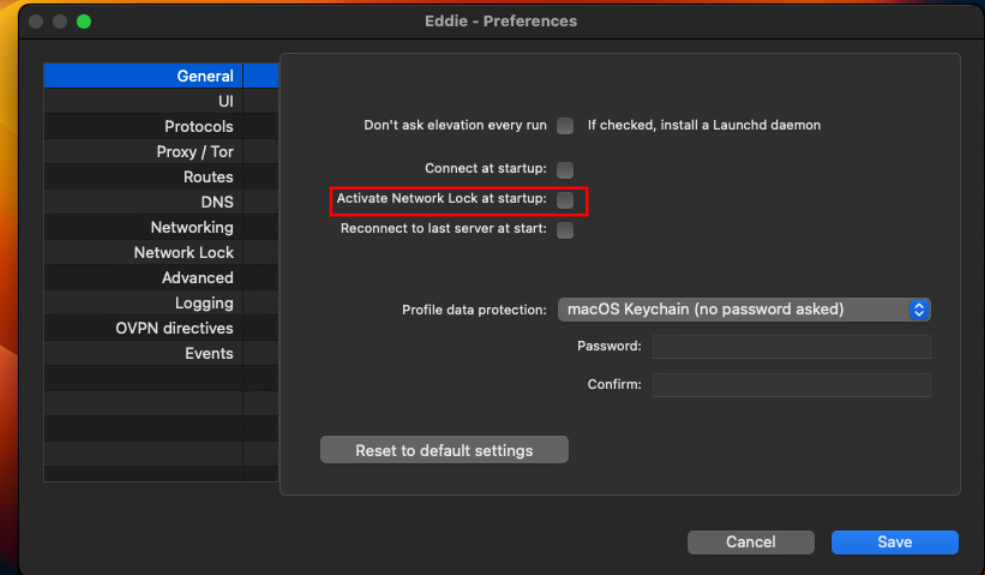
NOTE: starting from Eddie 2.23.0 (and NOT in any previous version), by default Network Lock is enabled during a connection and disabled at the disconnection, if it is not explicitly activated. This behavior is set by the "Ensure in session" item in "Preferences" > "Network Lock" window (enabled by default). If Network Lock is explicitly activated then it remains active as long as Eddie runs, and is de-activated as soon as Eddie is properly shut down or Network Lock is explicitly disabled from the main window.
Kind regards
-
Hello!
Please delete all Eddie's local data (not only the cache, all data) from the app settings menu of your FireStick. You will then need to re-enter your AirVPN credentials at the next run. Alternatively uninstall and re-install Eddie. Starting from Eddie 3.0 the Master Password is disabled by default and opt-in.
Kind regards
-
Hello!
Your proxy is not responding, or maybe it is refusing connections. Check the settings in the "Preferences" > "Proxy / Tor" window. Don't use an additional proxy unless it is absolutely necessary (for example if you are behind a proxy). We infer that you configured a connection over some proxy, without credentials, from the entry which we can sneak on the screenshot you posted. For a more complete analysis please post the whole system report. Please see here to do so: https://airvpn.org/forums/topic/50663-youve-been-asked-for-a-support-filesystem-report-–-heres-what-to-do/
Kind regards
-
New record! 1.02 Gbit/s on Haedus (2.04 Gbit/s on server's side for a single client).
Kind regards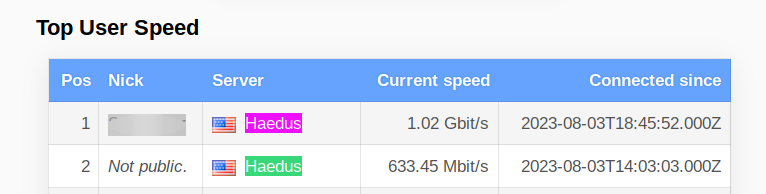
go558a83nk and ScanFarer reacted to this -
Hello!
The Windscribe interface is causing a critical error to OpenVPN. To solve the problem please see here: https://airvpn.org/forums/topic/53451-after-airvpn-changed-a-device-it-was-unable-to-connect-normally/?do=findComment&comment=194389
Kind regards
-
1 hour ago, Nidus11857 said:I switched to openvpn connect and yeah it worked on its own
Hello!
Yes, because you generated profiles for openvpn-connect with the new keys you have created. Each time you change keys, you need the new profiles, obviously (as the previous ones contain the old keys...). With Eddie Desktop edition, to update the keys just follow the simple procedure specified the instructions, which is necessary each time you renew your keys or create new keys. In general, read the documentation.
Kind regards
-
4 minutes ago, flat4 said:The answer is yes, I don't remember where the post is but everything runs in ram
Hello!
To clarify, this message comes handy: https://airvpn.org/forums/topic/56149-why-hard-disks/?do=findComment&comment=221245
Kind regards
-
On 7/21/2023 at 10:24 PM, SkyFyx said:Hi,
In settings i've checked "Don't ask elevation every run".
But i don't know how to create service, or rather what to put in the service to make it work.
And is it possible to tell the qbittorrent service to start up after Eddie-UI?
If so, could someone please help me?
Thanks !
Hello!
When you check "Don't ask elevation every run", Eddie creates a systemd unit (you don't need to create it manually) and therefore after you reboot the system, even if you run Eddie from your DE, no password should be asked, except the keying password, or the Master Password if you enabled it. Might it be that you were prompted for that password? If you reproduce the issue, can we see a screenshot showing this password prompt?
Kind regards
-
Hello!
You have just renewed you client key and created a new one. Please follow the instructions to fix this error:
Pay attention to the last paragraph in bold.Quote. 2023.08.03 16:32:21 - OpenVPN > AUTH: Received control message: AUTH_FAILED
W 2023.08.03 16:32:21 - Authorization failed. Look at the client area to discover the reason.
1 hour ago, Nidus11857 said:Please look into this i just bought this vpn and i did for 6 months at that pls dont make me regret this
Before jumping to conclusions or panicking always read the documentation first, consult the FAQ and if necessary write to the support team (open a ticket).
Kind regards
-
Hello!
It looks like you need the list of entry-IP addresses 3, therefore you must resolve europe3.all.vpn.airdns.org.
europe.all.vpn.airdns.org is updated as usual, anyway. It resolves into all the entry-IP addresses 1 of servers in Europe.
europe3.vpn.airdns.org resolves into the single entry-IP address 3 of the unique server in Europe with the "best" rating.
Please see https://airvpn.org/faq/servers_ip/
Kind regardsshaunography reacted to this -
30 minutes ago, BKK20 said:Thanks! Do I need a new config file after that?
Hello!
Yes, a new configuration file is strictly necessary, for the key is different for each device.
If you run Eddie you need to select the key you prefer from the combo box just under the login credential fields.
If you run Bluetit+Goldcrest you can select a specific key with the air-key Goldcrest option (or airkey in Bluetit run control file).
Kind regards
-
@go558a83nk
Hello!
Yes, the lack of entry-IP addresses 2, 3 and 4 on server domain names persists since 2010 and probably does not make sense anymore now. We'll think about it.
Kind regards
-
11 hours ago, BKK20 said:Hello, but I have only one device and one key and I can't use the same DDNS. That's the reason I ask.
Hello!
Understood. You need to generate another key.
Kind regards
-
3 hours ago, go558a83nk said:been this way for years that some Air servers didn't resolve with that domain pattern but that's the one I always try to use so I forget the "proper" way. apparently it's superba.airservers.org
Hello!
Correct. The old <servername>.airvpn.org for the entry-IP address 1 has been maintained for backward compatibility for some years only on old servers for a smoother transition. New server domain names (for all servers) follow the current documentation for example https://airvpn.org/faq/servers_ip/
Kind regards
-
1 hour ago, ss11 said:You posted on a topic that is more than 10 years old and now it might become confusing - we have servers in Japan that work quite well (things have changed since 10 years ago obviously).
Correct,
Japan's data protection legal framework revisions in 2015 and 2022 were a very remarkable improvement. We do not see any legal problem in Japan now.
1 hour ago, ss11 said:For Russia I am not sure if it fulfills AirVPN's requirements.
You need to apply for a license and you can use only equipment approved and pre-configured by the federal security service. All devices must be connected to the FSIS, comply to the list of censored services, and can be seized by Roskomnadzor, investigative agencies, and the Federal Security Service without a court order (if the devices disconnect from the FSIS or for other reasons: without a court order they can just seize without notifying a reason and inaudita altera parte of course). Running servers without notifying Russian regime would be a fallacious option as it would probably expose to unnecessary risks Russian citizens connecting to them.
Quoteare you planing to offer a server in Hungary? Would be very much appreciated.
We're sorry, no plans for Hungary right now. Anyway we discuss regularly, on a monthly basis at least, infrastructure status and expansion options, so things may change in the future.
Kind regards
-
Hello!
Problem solved, except for Lacaille. We'll be waiting for datacenter support.
Kind regards
-
Hello!
We're very glad to inform you that a new 1 Gbit/s full duplex servers located in Chicago, Illinois, is available: Superba.
The AirVPN client will show automatically the new server; if you use any other OpenVPN or WireGuard client you can generate all the files to access them through our configuration/certificates/key generator (menu "Client Area"->"Config generator").
The server accepts connections on ports 53, 80, 443, 1194, 2018 UDP and TCP for OpenVPN and ports 1637 and 47107 UDP for WireGuard.
Superba supports OpenVPN over SSL and OpenVPN over SSH, TLS 1.3, OpenVPN tls-crypt and WireGuard.
Full IPv6 support is included as well.
As usual no traffic limits, no logs, no discrimination on protocols and hardened security against various attacks with separate entry and exit-IP addresses.
You can check the status as usual in our real time servers monitor:
https://airvpn.org/servers/Superba/
Do not hesitate to contact us for any information or issue.
Kind regards and datalove
AirVPN Team -
1 hour ago, flyinginsectapplepie said:The error may be self-explicative, but I can't know it's being looked into if no one says so. I will be following this thread. Thank you.
Hello!
Thank YOU for the report and for your tests. Yes, the problem has been forwarded to the attention of the devs because of your report.
1 hour ago, flyinginsectapplepie said:This was very useful advice. I was aware of multiplexers, but didn't know it could be used for this, that you can detach from a session and leave it running. You might want to mention this in your documentation.
Glad to hear it.
QuoteThe way eddie-cli works isn't practical, it should run as a service, like all other VPN clients, but running it inside tmux makes it much more usable.
If you prefer a different architecture, specifically a client-server one, you can consider Bluetit and Goldcrest, components of the AirVPN Suite. Bluetit is a real daemon which you can configure via run control file and drive through Goldcrest (the client) and signals.
Unfortunately the Suite does not support WireGuard at the moment. However, if you don't need WireGuard, the Suite can replace Eddie CLI while the problems you reported are investigated. Those AirVPN Linux users who don't need a GUI and WireGuard are advised to use Bluetit and Goldcrest in order to have AirVPN infrastructure integration, higher comfort and a better security model provided by the specific client-server architecture.
You can find a thorough user's manual here: https://airvpn.org/suite/readme/
The download page is here: https://airvpn.org/linux/suite/
If you prefer to build the Suite from the source code: https://gitlab.com/AirVPN/AirVPN-Suite (build scripts and instructions are included)
Those who want to design their own client to operate Bluetit can consult the developer's reference manual which can be downloaded here in PDF: https://gitlab.com/AirVPN/AirVPN-Suite/-/blob/master/docs/Bluetit-Developers-Reference-Manual.pdf
Kind regards
-
3 hours ago, autone said:@Staff are you able to share some information regarding this issue? would really appreciate it. because right now I'm unable to use airvpn.
Hello!
We are aware of the issue and we should be able to resolve the situation in 24 hours or so. Thank you for your patience. Other 6 servers in Singapore are open, we're sorry to hear that you have bad peering with them. Japan also offers a large bandwidth availability, you might test it as well.
Kind regards
-
Hello!
We're glad to inform you that upgrade of server Haedus in New York City is complete. The server is now connected to a 10 Gbit/s full duplex port and line. The upgrade includes a new board with a more powerful CPU. IPv4 addresses and IPv6 block remain the same.
This improvement completes the infrastructure upgrade in New York City for the summer answering to the increased bandwidth demand in the area.
Kind regards and datalove
AirVPN Staff





gluetun port forwarding issue
in Troubleshooting and Problems
Posted ...
Hello!
Yes, various users found the problem in their configuration, you may check whether their solutions are applicable for your case too:
https://airvpn.org/forums/topic/56370-portforwarding-not-working-gluetun-and-desktop-app/?tab=comments#comment-223375
https://airvpn.org/forums/topic/56288-proper-way-to-set-up-airvpn-wireguard-with-portforwarding-in-a-docker-with-gluetun-on-nas/?tab=comments#comment-222853
Also consider to contact Gluetun community as Gluetun supports AirVPN.
Kind regards