
go558a83nk
-
Content Count
2096 -
Joined
... -
Last visited
... -
Days Won
37
Posts posted by go558a83nk
-
-
It's not that difficult to see. Go to https://airvpn.org/issues/ and look for all the servers that were out for an upgrade.
-
Hi
As a self confessed newbie and not technologiacally inclined, can someone answer this.
I have been recommended Air vpn.
I`m planning on going to Spain in a week but for a reason I want to appear to be in England.
When I choose the server/country I guess that I need to choose England/UK and NOT Spain.
Apologies for being a dumb ass. LOL
Yes
-
Any chance you could post some screen shots of your pfsense stunned options?
I am struggling with this as well.
Many thanks
I don't use stunnel but had originally set it up just to say I could.
Now my first question to you is why do you want stunnel? If you're needing SSL tunnel for something you might get what you want just using the new tls-crypt option.
-
They shouldn't. Check ipleak.net - I bet you have a DNS problem. If you're still using Sky for DNS resolution they'd forward you to that splash page.
-
I'd get prepared to use the new tls-crypt that AirVPN offers. If that doens't work fall back to the SSL.
-
I pulled up www.yelp.com just fine in my browser connected to one of the Dallas servers.
-
Hello
I have a very strange problem with my Windows 10 laptop. I try to make a VPN chain. My host OS is a freshly and clean installed Windows 10 Professional without any third party antivirus or firewall installed. I set up an Ubuntu virtual machine in vmware workstation player with NAT network setting.
I can successfully connect to the first VPN server on my host OS and start up the virtual machine. When I go to ipleak.net (in the Ubuntu guest OS) i can see the ip address from the first VPN server, so far so good. But when I try to fire up the eddie client in the Ubuntu guest OS and make the second VPN connection it's always stuck on checking route and it fails to connect.
After that, I tried to disable the VPN connection on my host OS. I can now make a VPN connection inside the Ubuntu guest OS without any errors.
So, a VPN connection is possible on the host and guest OS, but chaining doesn't work.
I tried exactly the same on my friends Windows 10 host machine and it worked right away. Why it doesn't on my Windows 10 Laptop?
It sounds like you're connecting just fine but the method used to confirm the tunnel is working is failing. There used to be an option to disable checking the route but I think it may be re-named now. I don't use the app so I'm not sure. If that option is disabled then it'll stay connected and the tunnel is probably working.
-
From what I've seen there's no link between referrer URL and the AirVPN username of the account to which it's referring. You can post your referral link on your web site but people still have no idea what your AirVPN username is. Am I wrong?
-
You need to create a port forward with local port of 32400. External can be whatever AirVPN assigns you and you then put that external port like you know how to do already.
Thanks for the reply, I never needed to do that before which is odd.
I assume you just mean forward it in the router yeah?
are you running VPN on the router? If not then you don't touch your router. You should turn off UPnP on your router as well.
no, I mean when you make the port forward on the AirVPN web site you make it with local port 32400.. Then put the external port that's assigned to you into Plex.
-
You need to create a port forward with local port of 32400. External can be whatever AirVPN assigns you and you then put that external port like you know how to do already.
-
Connect to entry 3 or 4, that's tls-crypt.
I think you need the experimental version but I might be wrong on that.
-
If you are not aware, Fortigate allows network admins to enforce network-wide SSL inspection. In laymans terms it means any encrypted data they cannot read, they block.
Which in turn means every VPN out there, PIA, Nord, AirVPN, everything that runs on OpenVPN regardless of SSL or SSH tunnels is certainly blocked and impossible to bypass.
Is there ever going to be a fix for this? Or are we heading towards a time where VPN's and other circumvention becomes obsolete?
so they block https? or do they work as MITM?
-
I agree. airpvn.org is one of the slowest loading web sites I've ever used when I have to login. It's not bad when everything is cached.
JemTheWire reacted to this -
Linux, as Untangle is based on Debian.
-
Eddie is based on OpenVPN. OpenVPN is old and has a number of inefficiencies. One of the most glaring is the fact that it isn't multithreaded. As such, even on the best hardware, you'll be limited to something like 200-250 Mbps per active connection.
CPUs with slower single-core performance or older CPUs missing certain instruction sets can also limit OpenVPN's throughput. What CPU are you using on your test system?
I can get 400+ mbit/s with my pfsense machine. With servers being 1gbps a single user can't expect much more because the server has limits - inbound + outbound = bandwidth limit.
-
Well, the first thing to try is TCP instead of UDP to see if that fixes it.
-
That sort of inactivity is not what causes disconnects. Something is causing the tunnel to not be able to send/receive data at all.
-
"tls-crypt", an OpenVPN feature which makes circumvention of blocks against OpenVPN, an issue which is particularly important in countries controlled by human rights hostile regimes, even more efficient than the other methods we have been providing.
Isn't SSL and SSH still a more effective method of bypassing blocks? As i understand it, a SSL connection is less likely to be blocked than a standard OpenVPN connection with the packet headers scrambled.
tls-crypt has so far been good for people who need to bypass state firewalls and since it can use UDP it performs better than SSL or SSH.
-
Sorry, I meant to reply to your post from a couple days ago and somehow it was marked as read and I forgot to.
Yeah, I've noticed that servers will say the settings don't match if I'm asking for GCM. But, it'll connect with a GCM cipher as you've seen.
I don't know about your CPU but mine is fastest with GCM so I'm glad to have it.
-
So, I did a little test. I connected to two different servers but at the same port. So, both had a 10.30.0.x virtual address. Sure enough, in the routing table of the web GUI only "ovpnc 1" showed under the netif column even though two clients were running according to "ifconfig" at the command line.
However, when I looked at what my exit IP was according to web sites, machines that were supposed to use server "A" were reported as having server A's exit IP. And machines supposed to use the server "B" were reported as having the exit IP of server B.
Could this just a bug in routing table display?
-
-
I'm no expert. There's way too much I don't understand.
The OP may be on to something but I also figured if this were an inevitable problem it would be discussed a lot more in pfsense openvpn topics.
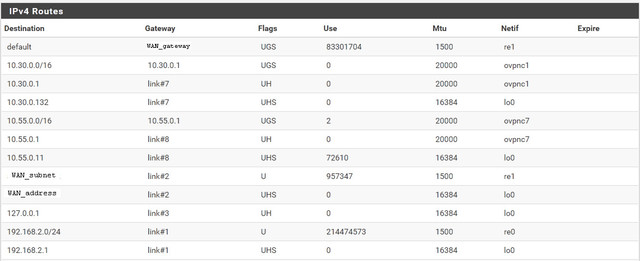
Here's my routing table with two clients up and running. The subnets aren't the same since one of them is to a tls-crypt server now.
-
Are you using the options in the openvpn client setup "don't pull routes" and "don't add/remove routes"?
I currently only use "don't pull" but I tested both and each one separately, and also the topology. Nothing changes what the server pushes to the client.
Much of my pfsense setup is following the excellent guide that's here on the forums. In that don't pull and don't add/remove are selected and therefore you don't have problems of subnets overlapping. And perhaps there are some other settings that affect this too that I don't recall. Anyway, I've never had problems running multiple clients.
What the server pushes doesn't change but it's that pfsense ignores it.
The guide is indeed excellent, and I use it for my base config too.
The issue I describe here is not new, and Air VPN support is aware of this issue. Couple of years ago they moved from a /30 topology to a /16. I am not making this up.
If you are using multiple VPN client connections from the same machine (pfsense or router), please take your time to check your routing table. Go to pfSense, Status, OpenVPN, and record the Virtual Address of each connection. Do any of them share the same 2nd octet, like multiple in the 10.4 or 10.30 range? Look at your routing table, go to pfSense, Diagnostics, Routes. Check that you see all your OpenVPN clients under the "netif" collumn, or just paste both here and let me have a look.
To which ports did you setup your connections?
I've definitely run multiple openvpn clients where the subnets overlapped. yet, I've never had trouble with getting the traffic I wanted through the tunnel I wanted via NAT and firewall rules.
-
Are you using the options in the openvpn client setup "don't pull routes" and "don't add/remove routes"?
I currently only use "don't pull" but I tested both and each one separately, and also the topology. Nothing changes what the server pushes to the client.
Much of my pfsense setup is following the excellent guide that's here on the forums. In that don't pull and don't add/remove are selected and therefore you don't have problems of subnets overlapping. And perhaps there are some other settings that affect this too that I don't recall. Anyway, I've never had problems running multiple clients.
What the server pushes doesn't change but it's that pfsense ignores it.


IPv6 support and new smart features
in News and Announcement
Posted ...
So, which servers are connected to 10Gbit/s lines?