
go558a83nk
-
Content Count
2093 -
Joined
... -
Last visited
... -
Days Won
37
Posts posted by go558a83nk
-
-
1 hour ago, overmorrow said:Okay... I can't claim to have solved the issue, but at least I've worked around it. I could. not. get. OpenVPN to work on pfsense - not the old version (2.4.5) that I was using, nor the new one (2.7.2). What I instead did was use this guide to install WireGuard and use that instead. There are still some oddities that would be nice to work out (for example duckduckgo no longer responds even though every other site does) and changing the country I'm in by running Hummingbird on a machine (and thus running a VPN connection through a VPN connection) seems to have issues that I haven't worked out yet, but for people who have issues with getting OpenVPN to play ball on pfsense, I recommend looking at the WireGuard option. You need pfsense 2.6.0 or greater for it to be an option, though.
The OpenVPN issue seemed to be with the internal workings of pfsense. SSH:ing into the pfsense box and just straigth up running openvpn with one of the config files, worked fine, but setting up the ovpn1 interface and commanding it via the GUI didn't work no matter what I tried.
Did you complete the guide's instructions on setting MSS on the LAN interface? -
20 hours ago, al the yank said:Hello,
I see how we are all dealing with fixing our broken access. I did get Eddie to work again with the renewal but I dont like using the SW clients. I tried creating new keys from the Config Generator but no success. Anyone else get this working ok? What a pain...
the config generator doesn't create keys. it creates configs using the keys you've made in the key gen section. https://airvpn.org/devices/ -
1 minute ago, hbs said:
Maybe I misunderstood it.
I thought Wireguard was native on pfSense 7.2 running on the newest FreeBSD base.
I'm thinking of getting my other NIC available on my APU2 to run a separate instance of Wireguard to try to bypass some different streaming geo-blocking in the UK.
It very well might be. Years ago pfsense came out with native wireguard but there were problems so they quickly removed it with a patch. Then somebody who knows what they're doing made a wireguard package which people have been using since then. -
1 minute ago, hbs said:Thanks for the help guys.
I finally did it. But I had to reset to defaults and restart from there.
Since this is an old install I believe my certs were getting stuck somewhere.
@go558a83nk @Air4141841 @Staff
Since I have your attention, I wonder if it will be wise for me to upgrade from pfSense 2.6.0 to the the lastet 2.7.2 in order to start using (testing) Wireguard.
If that is the case it will be nice to have a guide as well.
Thanks
Wireguard would likely be faster. I can't say much more about updating because I use pfsense+ and I'm using a wireguard add-on package. You seem to imply that by updating wireguard is native?
I followed a video guide on wireguard setup years ago. I'm not up to making one myself but you might find it by searching the web and the pfsense subreddit which is often helpful. -
and if somebody did change from tls-auth to tls-crypt you'll need to change a few things in the openvpn config besides updating the certs.
sha512, tls encryption and authentication, different remote IP off the top of my head. -
-
6 minutes ago, clevoir said:
20240409 20:27:44 Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
sha1 being used which is for old tls-auth configs but only staff can quickly say if the entry IP is 1 or 2 and not 3 or 4. that is to say, I'm guessing you and several others are getting tls-auth and tls-crypt things mixed up.
edit: Ok I see your post below mine that shows you used a tls-auth config.Air4141841 reacted to this -
1 hour ago, Devante Weary said:Ah yes, when you don't have a real argument, fall back to the old racism tactic.
For some odd reason you think that if something is codified in law, it cannot be censorship.
They're also living under the assumption that government is benevolent and righteous. Have they forgotten that the government of the very thing they detest (nazism) made illegal many things...was it ok because the government made them illegal?adrift33 and Devante Weary reacted to this -
18 minutes ago, juniormaxx said:i've checked the TLS keys and make sure they're correct and the CA cert is correct. how can i change the other certificates, the option is only to export them, you can't edit. it looks like that one use cert is different.
i'm not having a good day, can anyone help with how to change the certificates or do i have to add everything again.
If you need to change the certs you can add them the same way you added the the others you've been using and then update the openvpn config such that it uses the new certs instead of the old ones (simple drop down selection).
If you, like alanm, are trying to use entry IP 3 or 4 then you'll need to adjust for tls-crypt usage. However, I do wonder if your old version of pfsense has a new enough version of openvpn to even support tls-crypt. -
Are the servers moving to a different datacenter?
-
12 hours ago, overmorrow said:I'm using pfsense to connect, and today it had suddenly stopped working. I suspected that the reason was that I hadn't updated the certs in many years as others seemed to have issues with that too, so I downloaded some new config files and updated the CA and the cert. I also updated the cipher, digest algorithm and tls key to match the new file. Unfortunately I still can't connect. The client tries, and immediately disconnects. The logs do not provide much insight into what's going on... Any suggestions? My config is based on the old pfsense 2.3 -guide available in the forum, (and basically stems from a time when pfsense 2.3 was state of the art).
Apr 8 22:09:19 openvpn 86390 Server poll timeout, restarting Apr 8 22:09:19 openvpn 86390 SIGUSR1[soft,server_poll] received, process restarting Apr 8 22:09:19 openvpn 86390 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Apr 8 22:09:19 openvpn 86390 TCP/UDP: Preserving recently used remote address: [AF_INET]128.127.104.82:443 Apr 8 22:09:19 openvpn 86390 Socket Buffers: R=[42080->262144] S=[57344->262144] Apr 8 22:09:19 openvpn 86390 UDPv4 link local (bound): [AF_INET]XXX.XXX.XXX.XXX:0 Apr 8 22:09:19 openvpn 86390 UDPv4 link remote: [AF_INET]128.127.104.82:443 Apr 8 22:09:19 openvpn 86390 MANAGEMENT: Client connected from /var/etc/openvpn/client1.sock Apr 8 22:09:19 openvpn 86390 MANAGEMENT: CMD 'state 1' Apr 8 22:09:19 openvpn 86390 MANAGEMENT: Client disconnected
1) management: client disconnected is not the VPN client disconnecting. it's pfsense's openvpn management client that's disconnecting from...managing it I guess.
2) otherwise the log shows very little. after the lineUDPv4 link remote: [AF_INET]128.127.104.82:443usually you'd see something about initial TLS packet. If you're not getting any response from the VPN server then perhaps something's blocking it, like a local firewall or your ISP. -
pfsense warned me last month that some old certs were expiring so I'm not surprised that some people are seeing this results. It's unfortunate that software (eddie) or this web site didn't warn people they were using certs about to expire.
-
1 hour ago, Air4141841 said:looks like it from the configuration generator.
I am actually surprised to see almost 50 users connected. previously it was only maybe 7.
I went the opnsense route so I doubt I will be able to test this anytime soon again. my sg3100 is end of life and not getting updates anymore
from what I recall reading you are a heavy Pfsense user. ccorrect?
LOL thanks. I forgot I could use the config generator to narrow down the list. 😳 -
Hello, is Marsic the only server that supports DCO or have more been added to this test? Thanks.
-
Happens to me on any proxy/VPN, not just AirVPN.
-
You can likely insert postup and predown iptables rules (I assume that's what they are) into the AirVPN configs or do other things as listed in the following link
-
-
9 212.222.6.229 72.747 ms 53.818 ms 52.890 ms 10 213.200.116.225 75.413 ms 67.799 ms 65.760 ms 11 87.119.97.186 62.010 ms 61.559 ms 61.516 ms 12 81.95.2.138 66.963 ms 66.516 ms 66.997 ms 13 * * * 14 128.241.10.42 157.959 ms 135.565 ms 135.466 ms 15 129.250.2.252 132.307 ms 134.168 ms 134.819 ms 16 129.250.2.155 136.883 ms 136.940 ms 136.883 ms 17 128.241.9.243 141.064 ms 138.435 ms 137.656 ms 18 37.123.210.65 146.810 ms 141.526 ms 138.384 msRoute trace to the new servers from my ISP. Seems like a problem going from GTT to NTT network which is like hop 12-14. Hop 12 is already in Amsterdam.
-
my quick look tells me you're perhaps not creating a firewall rule on the correct interface. You've got a port forward rule for airvpn_wan_WG_0 but you're not showing a corresponding firewall rule for that interface for port forwarding. when you create the port foreward rule use the filter rule association option at the bottom of the port forward rule setup to create new associated filter rule. this will automatically put the necessary firewall rule on the correct interface.
also you're using an alias for NAT IP for the port forward rule. this should be the IP of the device running the server. I see no reason for an alias as it should be just one local IP, e.g. 192.168.2.22.
again, no reason for an alias for destination ports and NAT ports as AirVPN port forward rules can only forward 1 port each. -
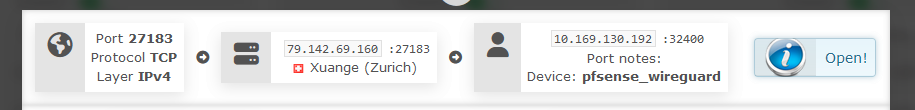
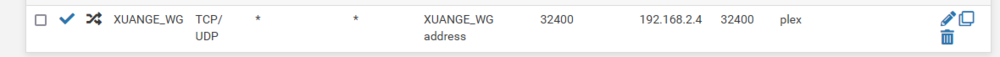
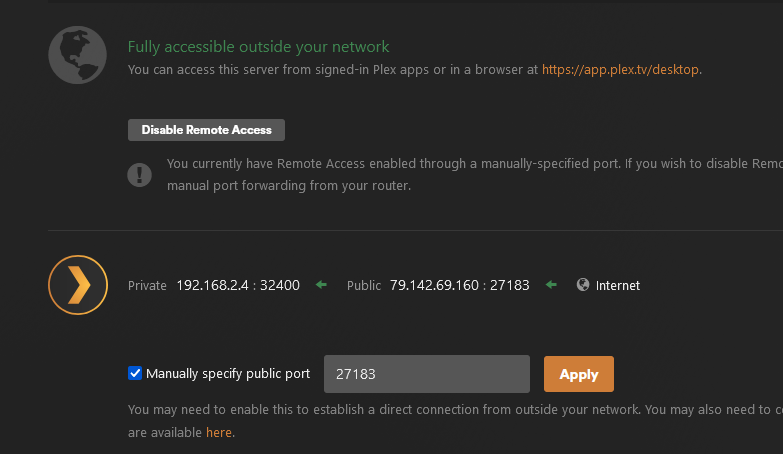
this is my experience but @Staff seems to be saying this isn't the way it works. 27183 mapped to 32400 on Air's servers, pfsense is instructed to forward port 32400 on the VPN interface to my laptop:32400 where plex is listening. I have to instruct plex that the actual public port is not 32400 but 27183. Note that by manually specifying public port plex does not change the private port it listens on - it's always 32400.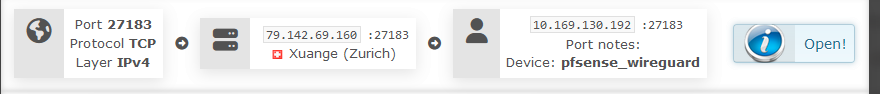
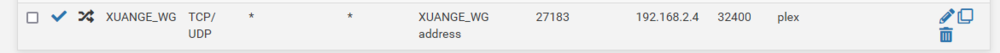
I could make the port forwarding rule on the Air web site 27183-27183 and then change my port forwarding rule in pfsense to VPN interface:27183-laptop:32400 and that would work also.
So, you can see why I say what I say. I'd have to look more into behaviors when the VPN client is on the same device as the plex server but one thing holds true, I know : plex always listens at localhost:32400.
https://support.plex.tv/articles/200931138-troubleshooting-remote-access/
So I really see it as impossible that a port forwarding rule 2***7 forwarded to 2***7 works unless somewhere else in the chain 2***7 forwarded to 32400.
-
1 hour ago, Staff said:
Hello!
Yes, as we wrote (and you couldn't know, but now you know) @robzeta had forwarded, on the AirVPN port panel, remote port 39196 to local port 32400. Therefore Plex, which was configured to listen to public port 39196, could never receive packets. Also (and you couldn't know it as well) the forwarding was active only for UDP (note that the port tester performs a test only in TCP and correctly returned error 111 as expected). Now, @robzeta has deleted port 39196 altogether, so let's wait for the new tests.
Another clarification, this time for us: in the Plex documentation here https://support.plex.tv/articles/200289506-remote-access/ we read:
Therefore we guess that the Media Server refuses to listen if you don't have an account or you did not sign this account in to some other service managed by Plex Inc.? Can you confirm?
Kind regards
Maybe being signed in is the problem. I can assure you that remote port 39196 and local port 32400 is perfectly fine. Plex always listens at 32400 on localhost/LAN, but typically we cannot reserve 32400 with the AirVPN system. So we create the rule with 32400 internal, and tell plex what external port we've been assigned. Plex accommodates this with the "manually specify public port" option for these cases where default 32400 is not being used on the WAN. -
3 hours ago, Staff said:@robzeta
Hello!
Port 39196 reserved to your account is UDP only, so failure on TCP is expected. If Plex needs TCP as well please act accordingly on your account port panel. Furthermore, port 39196 is forwarded to your VPN IP address port 32400, so Plex will never receive any packet on port 39196. This explains also the connection refused error on port 39196 (a test which our port tester runs anyway): your system receives packets on port 32400 and correctly resets the connection. Adjust this setting too.
Kind regards
I don't know what you're seeing regarding TCP and UDP for the port forward, but it's testing both TCP and UDP according to the images. Also, plex always listens at 32400 but an external port of 39196 mapped to 32400 internal is probably what the user has setup and that should work. That's why you must instruct plex that the external port opened is 39196 and not the default 32400. -
no need to do anything on your router so remove what you did there for security. your image of plex remote access settings shows that remote access is working. if you click the "test open" button what happens?
-
4 hours ago, jimmycarter00 said:Why AirVPN is the only one that will make this? Why other vpn will stay still in Italy?
what other VPN is headquartered in Italy?




ANSWERED pfSense just disconnects after cert upgrade
in Troubleshooting and Problems
Posted ...
if that isn't working or the 1280 as Staff suggests you can also try setting MTU and MSS directly on the wireguard interface instead of the LAN interface. I'd suggest 1280 for both MTU and MSS on the wireguard interface and test the sites that aren't working for you. Then try higher values and see if there's a value at which sites stop working again.