-
Content Count
2089 -
Joined
... -
Last visited
... -
Days Won
83
Reputation Activity
-
 LZ1 reacted to RaineyPass in ProtonVPN (from Protonmail) ...
LZ1 reacted to RaineyPass in ProtonVPN (from Protonmail) ...
I've been using the paid version of Proton for about a year and have no real issues with it. Connects quickly, fast, very few glitches, no leaks, dirt simple interface. It's fairly equivalent to Air from a user standpoint except Proton has more servers with lower loads close to me. Wouldn't disrecommend it in any way.
Also currently use Air and Windscribe. Air definitely has the most sophisticated capabilities of any VPN I've used. Gave up on Mulvad, it was too slow for my location. Windscribe is OK; I don't appreciate the sarcastic comments in the set up app, nor the silly notifications. The base product works well for the most part but there are times it just plain won't stream video, get some weird js error with a giant X on the screen, some manifest overflow message. They're junking it up with blockers and their browser add on is kludgy, not to mention a foolhardy place for a VPN to reside.
Bottom line, if I need a reliable connection for a few hours, it's Air or Proton, not Windscribe.
I'd recommend trying different VPN's, at least try different good ones, some will be fast, some won't depending on your location and other factors. It's easy peasy to find many bad and good comments about any VPN. There are many reasons folks use VPN's; determine your needs and decide based on them, vs. someone else's. Unless a service is well known to sell user data, keep connection logs after disconnects, leak on disconnects (no network lock), spam your email, all the bad stuff that de facto makes it not a VPN, it's worth considering for a trial.
FWIW, my comments on Air's roughness earlier in the thread turned out to be (major blush) an underpowered AC adapter that was affecting everything, particularly wi fi, apparently. Got the right one and my laptop starting working perfectly again. First hand experience with erroneous blaming.
-
 LZ1 reacted to Staff in Mac: Can only connect to internet via AirVPN now... ...
LZ1 reacted to Staff in Mac: Can only connect to internet via AirVPN now... ...
Hello!
If you have never enabled Network Lock you can rule out firewall problems.
We suspect you suffer for a DNS issue. That's unexpected (Eddie must restore DNS settings when you shut it down properly) but we deem it possible since it has been sporadically reported before. Uninstalling Eddie will make no difference.
Anyway, if that's the case, solution will take just 30 seconds of your time. Set publicly reachable DNS in your system while Eddie is NOT running, that's all.
We recommend OpenNIC https://www.opennic.org but of course you can set any favorite DNS.
How to change DNS in Mac:
https://www.macobserver.com/tips/how-to/change-mac-dns-entries/
Kind regards
-
 LZ1 got a reaction from madrat in Eddie disconnects on MacBook Pro sleep ...
LZ1 got a reaction from madrat in Eddie disconnects on MacBook Pro sleep ...
Hello!
Of course it disconnects if your Mac is sleeping and nothing is running. If you use Network Lock, you shouldn't experience any leaks however, which is what you're worried about I presume.
Why do you want it to stay connected if your Mac is asleep and not in use?
-
 LZ1 got a reaction from Bprksons in Slow torrent speeds ...
LZ1 got a reaction from Bprksons in Slow torrent speeds ...
It's quite possible they're throttling. It's possible to tweak traffic shaping to only happen in certain conditions; hence one possible reason why you initially had good regular speeds, but then had issues with torrenting. It's bad practice, but some ISPs do it. Here's some supporting information on SSL and SSH as well, if you're technically inclined. I'm glad it worked anyway - enjoy yourself & welcome to AirVPN !
-
 LZ1 got a reaction from Bprksons in Torrent speeds have become unstable after service upgrade ...
LZ1 got a reaction from Bprksons in Torrent speeds have become unstable after service upgrade ...
Hello!
No logs are attached.
Please try Eddie Preferences>Protocols>SSH or SSL and then reconnecting to a location.
-
 LZ1 got a reaction from W0rkNow in Built in advertising and tracker blocking ...
LZ1 got a reaction from W0rkNow in Built in advertising and tracker blocking ...
Hello!
Absolutely not. For several reasons, including:
It's probably not harmonious with AirVPNs mission to make the Web as free as possible for users to experience, both good and bad. It's outside the purview of what a VPN is supposed to do. If users can't reasonably secure their own computers/browsers, then a VPN will be useless for them anyway. It adds another layer of complexity. Besides mainly being a marketing ploy, used by some of AirVPNs competitors, to give the impression of higher security and privacy. It's simply unnecessary and undesirable, for what is probably the majority of AirVPNs userbase, as such people can easily and would rather control this themselves. It's sort of a stated design goal for Eddie, that it isn't filled with any bloatware. Fortunately, nothing prevents you from installing something precisely like Ublock Origin, ticking off a few desired blocking lists and being on your merry way.
Thank you for sharing your thoughts however. As this topic has appeared a few times before, I think it's fair to lock this thread.
-
 LZ1 reacted to Staff in Eddie Android edition 2.1 released ...
LZ1 reacted to Staff in Eddie Android edition 2.1 released ...
Hello!
We're glad to inform you that Eddie for Android and Android TV version 2.1 has been released!
You can download Eddie from the Google Play Store:
https://play.google.com/store/apps/details?id=org.airvpn.eddie
You can also download Eddie Android 2.1 apk directly from our repository:
https://eddie.website/repository/eddie/android/2.1/org.airvpn.eddie.apk
At the moment Amazon Appstore still features Eddie 2.0.1 but the approval process for version 2.1 should be completed soon, at least according to what Amazon claims.
The application is fully localized. Current implemented languages: Chinese (simplified), Chinese (traditional), Danish, Dutch, English, French, German, Italian, Portuguese, Spanish, Russian, Turkish.
Eddie for Android 2.1 is a major refinement of version 2.0.1 and implements several features which were suggested by the community. It also underwent a deep re-engineering of some architectural components which translates into higher stability, correct co-existence with other VPN and non-VPN applications and in general improved events handling.
Eddie for Android is free and open source software released under GPLv3. We invite you to check from independent 3rd parties the lack of trackers code signatures, for example here: https://reports.exodus-privacy.eu.org/en/reports/search/org.airvpn.eddie
Source code is available on GitLab:
https://gitlab.com/AirVPN/EddieAndroid
Main features:
Free and open source OpenVPN GUI based on OpenVPN 3 The only Android application officially developed by AirVPN Robust, best effort prevention of traffic leaks outside the VPN tunnel Battery-conscious application Low RAM footprint Ergonomic and friendly interface Ability to start and connect the application at device boot Option to define which apps must have traffic inside or outside the VPN tunnel through white and black list Localization in traditional and simplified Chinese, Danish, Dutch, English, French, German, Italian, Portuguese, Russian, Spanish, Turkish Full integration with AirVPN Enhanced security thanks to locally stored encrypted data through master password Quick one-tap connection and smart, fully automated server selection Smart server selection with custom settings Manual server selection Smart attempts to bypass OpenVPN blocks featuring protocol and server fail-over Full Android TV compatibility including D-Pad support. Mouse emulation is not required. Enhancements aimed to increase accessibility and comfort to visually impaired persons AirVPN servers sorting options Customizable "Favorite" and "Forbidden" servers and countries OpenVPN mimetype support to import profiles from external applications NEW: Eddie for Android 2.1 - Release notes
Multiple OpenVPN profile support. The app now imports and manages multiple OpenVPN profiles Support for custom bootstrap servers Support for favorite and forbidden countries AirVPN broadcast messages support User's subscription expiration date is now shown in login/connection information The app is now aware of concurrent VPN use. In case another app is granted VPN access, Eddie acts accordingly and releases VPN resources Optional local networks access. In such case, local network devices are exempted from the VPN and can be accessed within the local devices Localization override. The user can now choose the default language and localization from one of the available ones Favorite and forbidden lists can now be emptied with a single tap VPN Lock can now be disabled or enabled from settings VPN reconnection in case of unexpected OpenVPN disconnection. (It requires VPN Lock to be disabled) User can now generate an OpenVPN profile for any AirVPN server or country and save it in OpenVPN profile manager Danish, Dutch, simplified Chinese and traditional Chinese localization New server scoring algorithm implementing the latest AirVPN balancing factors in order to determine the best server for quick connection Network name and extra information are now shown along with network type Better device network status management Bug fixes
Changelog:
Changelog 2.1 (VC 18) - Release date: 13 March 2019 by ProMIND
- [ProMIND] Production release
Changelog 2.1 RC 1 (VC 17) - Release date: 8 March 2019 by ProMIND
- [NEgiXr] Added Simplified Chinese localization
- [NEgiXr] Added Traditional Chinese localization
- [anonymous] Added Dutch localization
- [ProMIND] Native Library: updated openvpn3, mbedtls, asio, lz4 and boost 1.69.0 from their respective repositories
- [ProMIND] Native Library: fine tuning of compilation options in order to avoid TCP crash in arm32 architecture
- [ProMIND] Updated default manifest.xml
CountryContinent.java
- [ProMIND] CountryContinent(): Added support for simplified and traditional chinese
EddieApplication.java
- [ProMIND] onCreate(): BuildConfig.VERSION_CODE and BuildConfig.VERSION_NAME are now sent to the Log
VPNManager.java
- [ProMIND] The status of VPN Lock and LAN exclusion are now reported to the log at connection
- [ProMIND] In case network connection is MOBILE, LAN exclusion is ignored and forced into the tunnel
LogActivity.java
- [ProMIND] onCreate(): BuildConfig.VERSION_CODE and BuildConfig.VERSION_NAME are now exported to the Log header
- [ProMIND] onCreate(): Settings dump is now exported to the log file
MainActivity.java
- [ProMIND] It now signals whether the app is in foreground by using SupportTools.setAppIsVisible()
NetworkStatusReceiver.java
- [ProMIND] Added NetworkType enum
- [ProMIND] Added getConnectionType() method to properly determine connection type according to NetworkType enum
- [ProMIND] Added a more accurate control in order to avoid duplicate events from BroadcastReceiver
PackageChooserActivity.java
- [ProMIND] ApplicationListLoader class: Package list is now loaded in a UI Thread
SettingsManager.java
- [ProMIND] Added dump() method. Returns a complete dump of the current settings
SupportTools.java
- [ProMIND] Added methods setAppIsVisible() and isAppIsVisible()
- [ProMIND] All information dialogs are now shown only in case the app is in foreground
Changelog 2.1 beta 2 (VC 16) - Release date: 25 February 2019 by ProMIND
NetworkStatusReceiver.java
- [ProMIND] networkDescription(): Fixed Android 9 compatibility
Eddie for Android 2.1 beta 1 - ChangeLog
Changelog 2.1 (VC 15) - Release date: 22 February 2019 by ProMIND
- [ProMIND] Fixed minor bugs reported in crash reports
- [ProMIND] Added country_menu, whitelist_country_menu and blacklist_country_menu menu resource files
- [ProMIND] Added new class OpenVPNProfileDatabase for storing and managing multiple OpenVPN profiles
- [staff] Added Danish localization
AirVPNServerProvider.java
- [ProMIND] getFilteredServerList() now filters server list according to white and black listed countries
AirVPNManifest.java
- [ProMIND] Added private properties load_factor and users_factor to conform to new manifest.xml layout
- [ProMIND] Property speedFactor datatype changed to double
- [ProMIND] Added class Message representing Manifest's messages to be shown to the user
AirVPNServer.java
- [ProMIND] computeServerScore(): score is now computed according to new AirVPNManifest's speedFactor, loadFactor and userFactor
- [ProMIND] getOpenVPNProfile() can now generate country profiles
AirVPNUser.java
- [ProMIND] Added daysToExpiration property to reflect the number of days to AirVPN subscription expiration according to expirationDate property
BootVPNActivity.java
- [ProMIND] Added new class which replaced and superseeded the old one. It takes care of launching the last connected OpenVPN profile at boot time
client.cpp (native library)
- [ProMIND] Client::Impl::socket_protect() updated interface according to new OpenVPN3 interface
ConnectAirVPNServerFragment.java
- [ProMIND] Long press on "favorite" and "forbidden" lists now enables "empty list" context menu
- [ProMIND] AirVPN subscription expiration is now shown in network/vpn status dialog box
- [ProMIND] AirVPN user name is now shown in network/vpn status dialog box
- [ProMIND] CreateGroupList() added support for favorite and forbidden countries management
- [ProMIND] Added methods addCountryToFavorites(), removeCountryFromFavorites(), addCountryToForbidden() and removeCountryFromForbidden()
- [ProMIND] AirVPNServerExpandableListAdapter class: added support for showing and managing countries views as child items in favorite and forbidden groups
- [ProMIND] Added OnItemLongClickListener() to ListView in order to show a message in case item long press and user not logged in to AirVPN
- [ProMIND] Added exportToOpenVPNProfiles() for exporting AirVPN OpenVPN profiles in user's profile list
ConnectionInfoFragment.java
- [ProMIND] Removed showErrorMessage() method. VPN errors are now displayed to txtVpnStatus TextView
- [ProMIND] Removed connection error layout. All VPN errors are now sent to the log and displayed to txtVpnStatus TextView
- [ProMIND] Class now implements EddieEventListener in order to manage VPN events on its own
- [ProMIND] Connection info box now shows OpenVPN profile name in OpenVPN profile connection mode
ConnectOpenVpnProfileFragment.java
- [ProMIND] Added ListView for stored OpenVPN profiles and made it fully Android TV compliant for dpad navigation
- [ProMIND] Added connectDatabaseOpenVPNProfile() for connecting a stored OpenVPN profile
connection_sequence.csv
- [ProMIND] Set a new connection sequence: second attempt is now TCP,443 instead of UDP,53 (which is now third)
CountryContinent.java
- [ProMIND] Load country list according to user locale setting
EddieBroadcastReceiver.java
- [ProMIND] Removed tryRestoreLastProfile(). To start the VPN at boot, this class now starts an intent of BootVPNActivity class
EddieEvent.java
- [ProMIND] Better concurrency support: events are now synchronized and use a local clone of EddieEventListener ArrayList
LogActivity.java
- [ProMIND] Added Android Fingerprint to log
MainActivity.java
- [ProMIND] updateConnectionStatus does not longer propagate VPNManager's events. VPNManager events are now properly managed by EddieEvent class
- [ProMIND] Implemented onSaveInstanceState() to save fragments' state
- [ProMIND] Implemented onRestoreInstanceState() to restore fragments' state
- [ProMIND] onAirVPNManifestChanged() check for manifest's broadcast messages and shows them to the user
- [ProMIND] Added setVpnManager() method in order to set vpnManager object in case the VPN is started by an external event, such as BootVPNActivity class
- [ProMIND] In case of unexpected OpenVPN disconnection, it retries to reconnect to the VPN when the user has set "VPN reconnection" in settings
NetworkStatusReceiver.java
- [ProMIND] Added ExtraInfo and SubtypeName to network description
OpenVPNTunnel.java
- [ProMIND] Changed networkStatusChanged() return type to void
- [ProMIND] VPN Lock is now engaged according to "VPN Lock" setting
QuickConnectFragment.java
- [ProMIND] AirVPN subscription expiration is now shown in network/vpn status box
SettingsActivity.java
- [ProMIND] Added VPN Lock setting
- [ProMIND] Added VPN reconnection setting
- [ProMIND] Added custom bootstrap setting
- [ProMIND] Added language selection setting
- [ProMIND] Added exclude local networks setting
SettingsManager.java
- [ProMIND] Added methods getAirVPNCountryWhitelist(), setAirVPNCountryWhitelist(), isAirVPNCountryWhitelisted(), getAirVPNCountryBlacklist(), setAirVPNCountryBlacklist(), isAirVPNCountryBlacklisted()
- [ProMIND] Added methods isVPNLockEnabled(), setVPNLock()
- [ProMIND] Added methods getSystemApplicationLanguage(), setSystemApplicationLanguage()
- [ProMIND] Added methods areLocalNetworksExcluded(), setExcludeLocalNetwork()
SupportTools.java
- [ProMIND] Added method runOnUiActivity()
- [ProMIND] Added methods saveXmlDocumentToFile() and loadXmlFileToDocument() to write and read plain XML files
- [ProMIND] Added method setLocale()
- [ProMIND] RequestAirVPNDocument(): add custom bootstrap servers to the top of server list in case user has set them in settings
- [ProMIND] Added methods for IP convertion: IPToLong() and longToIP()
VPN.java
- [ProMIND] Added CONNECTION_REVOKED_BY_SYSTEM status
VPNContext.java
- [ProMIND] ensureRoutes(): default routing is now added in case user has not selected local network exclusion
VPNManager.java
- [ProMIND] onStatusChanged() now conforms to EddieEvent class
- [ProMIND] unbindService() does not change VPN status anymore (managed by VPNService)
- [ProMIND] start() now checks for network connection and, in case it is not available, activates a pending connection status to be resumed as soon as the network connection becomes available.
- [ProMIND] createProfileBundle(): add proper route to OpenVPN profile for local network exclusion
VPNManagerListener.java
- [ProMIND] Class deleted. Event moved to EddieEvent.java
VPNService.java
- [ProMIND] Added MSG_REVOKE property to notify client (VPNMaganer) in case of system revocation
- [ProMIND] Removed Status enumerator. The class now conforms to VPN.Status enumerator
- [ProMIND] Removed redundant members vpnStatus and vpnLastError as they are managed by VPN class
For Changelog of older versions, please consult the proper announcement or check directly GitLab.
Kind regards and datalove
AirVPN Staff
-
 LZ1 got a reaction from LMawery in Not network access while connected to OpenVPN ...
LZ1 got a reaction from LMawery in Not network access while connected to OpenVPN ...
It just depends on how many resources you allocate to the VM.
If you have a system with for example 8GB RAM, on newish hardware, it's possible to play games with a VM open. It depends on the games too of course.
Otherwise it's just a case of
Downloading a Linux .iso file. (You can pick Linux Mint or Ubuntu if you're new to it) Following the aforementioned link to download the VM software and set up a VM. Point the VM to the downloaded .iso file. Start up the VM and install Eddie in it. Then take a snapshot - which is like saving your progress. Then when you want to torrent, you start the VM software, load the saved snapshot and start torrenting. Inside the VM where Eddie is running, you'll have an AirVPN IP address. This is the guest OS.
While your Windows system that you used to install the VM software on, is the host OS. Here your IP isn't being hidden when you browse the web.
Even if it looks like a long process, it becomes super quick once you know it. I can firmly recommend getting to know VirtualBox and how to do the above mentioned things .
-
 LZ1 reacted to Guest in Eddie Android edition 2.1 beta released ...
LZ1 reacted to Guest in Eddie Android edition 2.1 beta released ...
After testing RC1:
1: Please can we disable all foreground app notifications? It's a bit annoying having to dismiss a popup saying you are connected, the status bar tells me that. It's one of the perks of OpenVPN for Android since it gets out of your way.
2: Package chooser bug is fixed.
3: Interestingly, if I have an app that relies on the local network, even if I blacklist the app, and set the "exclude local network" option to on, it still doesn't see it on the local network. This is if the option "block connections without a VPN" is selected in Android settings. So my conclusion is Android does something to prevent even local networks talking within the tunnel.
4: Possible integration with the client area to see other connected devices, manage keys etc.
5: IPleak integration: It'd be nice to quickly see what IP leak says without having to go to IPleak, maybe a separate tab and a button you can press to fetch info.
-
 LZ1 got a reaction from Valerian in New plan and lower prices ...
LZ1 got a reaction from Valerian in New plan and lower prices ...
Hello!
That's brilliant stuff, Staff.
Suggestion: Why don't you just add a separate button next to the first plan, called Request Free Trial or Request 3 Day Free Trial, which links to https://airvpn.org/contact/ page, instead of putting it on the same button as the 2 euro plan?
Because I think it's potentially confusing - if the user wants a free trial, they'll click the 2 euro plan and proceed to checkout and then wonder why they still need to pay.
-
 LZ1 got a reaction from Flx in Most Common Problems & Their Suggested Solutions ...
LZ1 got a reaction from Flx in Most Common Problems & Their Suggested Solutions ...
Hello!
I thought it was time to try and collect some of the wisdom floating around and see if we can't create a single thread for solving some of the most common and annoying repeat-issues. So how about it !
I define "common problems" as: if I'm getting a deja-vu every third time I post . Staff will have broken the Matrix by this point.
Each problem will have its own headline and then with any number of solution-oriented links appended underneath. For this reason, this grand list isn't final and is meant to be updated continually.
Naturally, the higher the link number for a solution, the more obscure the solutions are probably getting.
Warning: solutions aren't guaranteed. As with anything technical, trial and error is a core skill
Problem: Bootstrap Failed. Solutions: https://airvpn.org/topic/30824-bootstrap-failed-since-a-week/ Problem: No Internet connection after shutting down AirVPN and/or can only use Internet while AirVPN is on. Solutions: https://airvpn.org/topic/14829-can-only-connect-to-the-internet-browser-through-airvpn/?do=findComment&comment=30509 Windows only: https://airvpn.org/topic/13584-connection-problem-when-not-using-airvpn/?p=38800 MacOS only: https://airvpn.org/topic/27993-cant-connect-to-internet-without-using-airvpn/ https://airvpn.org/topic/21194-virtualbox-is-this-air-vpn-also-cant-connect-internet-unless-signed-in/ Problem: Cannot connect to any AirVPN server. Solutions: https://airvpn.org/topic/22140-cannot-connect-to-german-servers-anymore/ https://airvpn.org/topic/22066-cant-seem-to-connect-to-any-servers/ https://airvpn.org/topic/21418-new-to-airvpn-installed-avpn-on-surface-wwindows-10-cannot-connect-at-school-can-connect-fine-at-most-other-locations/?p=55515 Problem: Issues with Curl. Solutions: https://airvpn.org/topic/27369-cannot-login-curl-is-required/ Problem: Bad packet ID (may be a replay) Solutions: https://airvpn.org/topic/14094-weird-log-entries/ Problem: Being censored and/or speeds being throttled/shaped by ISP or Government. Solutions: https://airvpn.org/topic/28847-connections-from-china/
Problem: MacOS client can't connect. Solutions: https://airvpn.org/topic/18251-airvpn-mac-client-problems/
Problem: Checking route IPv6 Failed. Solutions: https://airvpn.org/topic/29401-checking-route-ipv6-failed-cannot-connect-to-vpn-server-using-eddie/
Problem: Waiting for TUN/TAP to come up. Solutions: https://airvpn.org/topic/26072-route-gateway-is-not-reachable-on-any-active-network-adapters-10401/?do=findComment&comment=70761 Windows only: https://airvpn.org/topic/17440-guide-fix-for-tap-adapter-in-windows/ Windows only: https://airvpn.org/topic/30043-taptun-interface-wont-come-up/
Problem: Experiencing slow and/or fluctuating speeds in general. Solutions: https://airvpn.org/topic/30739-every-vpn-is-slow-for-me-despite-the-well-reviewed-vpns-im-trying-is-it-possible-my-isp-is-causing-this-i-feel-like-someones-playing-a-joke-on-me/?p=80014 https://airvpn.org/topic/18635-looking-for-fast-server-eu-that-goes-beyond-30-40mbit/?p=44998 For online gaming: https://airvpn.org/topic/30135-frequent-spikes-lag-on-videogames/?p=79046 https://airvpn.org/topic/1947-for-those-wondering-about-speed-performance/?p=1967 https://airvpn.org/topic/26157-airvpn-slowing-down-other-machines-in-network/ https://airvpn.org/topic/26117-slow-speed-sort-of/?p=70906 https://airvpn.org/topic/20812-very-very-slow-dns-lookup/ https://airvpn.org/topic/23743-download-speeds-dropping-to-zero-and-going-up-and-down/
Problem: Slow torrent speeds and/or disconnects. Solutions: https://airvpn.org/topic/28082-torrent-on-airvpn-speed-is-very-poor/ https://airvpn.org/topic/26218-slow-torrent-speeds/ https://airvpn.org/topic/23936-repeatedly-getting-disconnects-while-torrenting/ https://airvpn.org/topic/23499-slow-torrenting-speed/ https://airvpn.org/topic/23070-solved-p2p-slow-over-udp-and-fast-over-tcp/ https://airvpn.org/topic/22716-poor-torrenting-connection/ Solutions are in link form without any explanatory text - at least not yet - so that the thread OP stays looking simple and uncluttered, where it's easy to find out what your problem is .
Feel free to contribute with your own helpful links. The more feedback this thread gets, the quicker it can be improved and hopefully made useful.
-
 LZ1 reacted to Staff in New plan and lower prices ...
LZ1 reacted to Staff in New plan and lower prices ...
Hello!
We're very glad to inform you that for the first time in 8 years we have decided to modify our prices to encourage and reward longer terms commitments.
While the shorter term plans remain basically unaltered, we have remarkably lowered prices of the long term plans and we have also added a brand new 3 Years plans for those who like to take greatest advantage from long commitments.
Check out the new price list here:
https://airvpn.org/buy
Kind regards and datalove
AirVPN Staff
-
 LZ1 got a reaction from chuckens in El Capitan 10.11.6 ...
LZ1 got a reaction from chuckens in El Capitan 10.11.6 ...
Hello!
Which Eddie client is this? I'm not sure how it works on Mac, but if the Stable release doesn't work, you could try the Beta client.
Instructions can be found in my signature .
-
 LZ1 reacted to Staff in First impression issues with Eddie for Android. ...
LZ1 reacted to Staff in First impression issues with Eddie for Android. ...
Hello!
We are very glad to inform you that this feature is already implemented. Make sure you run Eddie 2.0 or 2.0.1. In the server view you can define a white list of server(s) according to your preferences.
This feature is missing but you have the option to sort the servers in many ways, even ways which dynamically sort the list according to some server property, for example server load, as you might have noticed.
This feature is already implemented: just make sure that Eddie is the app selected for the proper mimetype (for the ovpn files). However, auto-connection when the ovpn file is imported is missing, we can plan to implement it
Nice suggestion, thank you.
Even this feature can be implemented, yes. We'll think about it.
Thank you!
Kind regards
-
 LZ1 got a reaction from Jeremyx3 in Yet another IP Leak question ...
LZ1 got a reaction from Jeremyx3 in Yet another IP Leak question ...
Hello!
Using Eddie with Network Lock enabled would also prevent WebRTC leaks .
-
 LZ1 got a reaction from itsmefloraluca in FYI: Official NordVPN Android app transmits personal data to third parties ...
LZ1 got a reaction from itsmefloraluca in FYI: Official NordVPN Android app transmits personal data to third parties ...
Hello!
That's certainly interesting. Thank you for taking the time to post it here and making it available in English .
I completely agree that the choice of justification is very poor in this regard.
Moved topic to the proper forum.
-
 LZ1 reacted to nwlyoc in Interactive Wrapper for Eddie's CLI version ...
LZ1 reacted to nwlyoc in Interactive Wrapper for Eddie's CLI version ...
Hello,
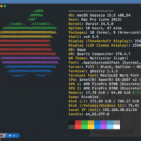
after I posted some suggestions for Eddie's CLI version in this thread and received some helpful information there, I set out to write my own little interface in bash for it to implement the suggestions. Being no programmer it turned out to be quite a project for me, and I would like to share it here in case anybody else prefers to run Eddie in the terminal rather than as a full GUI application. This script still uses Eddie itself, it's just a wrapper to make it as easy to use in the command line as it is as a desktop application. Screenshots are attached.
Some features and advantages:
uses less resources (top shows usually 0.3% CPU usage compared to 4-5% for the desktop version) can be exited without disconnecting interactive, sortable server list option to connect to another VPN with openconnect (since I need to do that from time to time, but it should be easy to add other connection methods as well) option to lock down the system's network traffic by default, so even without Eddie running with its own network lock there will be no leaks What to watch out for:
The default network lock works with direct rules in firewalld because I'm using Fedora. It should be easy to change it to use iptables directly on other distributions since firewalld's direct rules are just a way to directly manipulate iptables. Once activated, the lock will stay in place until manually deactivated (also surviving reboots), so no internet connection will be possible unless connected to AirVPN or other whitelisted VPNs. AirVPN's network lock overwrites the default network lock, so there will be no interference. Check your /etc/resolv.conf file while not running Eddie (because Eddie's network lock replaces that file temporarily) to make sure your router is not set as a nameserver (so no 192.168... address). Some routers will push themselves on that list by DHCP whenever you connect to their network. Since communication with the router is allowed in the lock rules, DNS requests will be handled by the router and sent to whatever DNS server is configured there even when network traffic should be blocked. There are ways to prevent that file from being changed by DHCP, best configure network manager for that if you use it. To connect to other VPNs, their IPs must be whitelisted and DNS requests for their domains must be allowed in the default network lock rules. The rules for airvpn.org can be copied and adjusted. I haven't yet included an option to pass command line arguments to Eddie. So if you need to set more advanced options like black-/whitelists, use of certain protocols etc., you need to set them manually in the connect_server function. All the possible options can be found in 'man eddie-ui'. You need to insert your own API key in line 5. It can be found in your account under Client Area -> API. Without this, connections will still work, but user info and connection status in the main window will not be properly updated. I tried to only use basic system tools. The script relies mostly on dialog, awk and curl (and firewalld as described and openconnect if needed), so it should work on most systems, but I'm not sure. And, lastly, VERY IMPORTANT: As I said, I'm no programmer and new to this, so even though I tried my best to make this script secure and error free, there might very well be some bad practice, never-ever-do-this mistakes or other hiccups in there. It works well for me, but better check it yourself. Feel free to use this as you wish, I hope someone can benefit from this. I'm happy about any improvements and corrections and will update this if I find the time.
UPDATE: A new version which uses Hummingbird and has been improved in many aspects (including automatic connection at boot) can be found here.
#!/bin/bash # an interactive shell script to control the command line version of the AirVPN Eddie client and openconnect more comfortably PROFILE_PATH="$HOME/.airvpn/default.xml" API_KEY="<your api key>" DIALOG_OK=0 DIALOG_CANCEL=1 DIALOG_EXTRA=3 DIALOG_ESC=255 HEIGHT=0 WIDTH=0 BACKTITLE="VPN Control" FORMAT="text" URL="https://airvpn.org/api/" PID=$$ function check_sudo { # check if user has sudo privileges sudo -vn &> /dev/null # gain sudo privileges for commands that need it (better than running everything with sudo) if [ $? = "1" ] then unset EXIT_STATUS_SUDO PASS_PROMPT="Establishing VPN connections and changing network traffic rules requires root privileges. Please enter your password:" until [ "$EXIT_STATUS_SUDO" = "0" ] do dialog \ --backtitle "$BACKTITLE" \ --title "Password Needed" \ --output-fd 1 \ --insecure \ --passwordbox "$PASS_PROMPT" 11 35 | xargs printf '%s\n' | sudo -Svp '' &> /dev/null EXIT_STATUS_PIPE=( "${PIPESTATUS[@]}" ) EXIT_STATUS_DIALOG="${EXIT_STATUS_PIPE[0]}" EXIT_STATUS_SUDO="${EXIT_STATUS_PIPE[2]}" EXIT_SUDO_TEST="${EXIT_STATUS_PIPE[2]}" PASS_PROMPT="The password you entered is incorrect. Please try again:" case $EXIT_STATUS_DIALOG in $DIALOG_CANCEL|$DIALOG_ESC) return 1 ;; esac done # keep sudo permission until script exits or permissions are revoked (e.g. when computer goes to sleep) while [ "$EXIT_SUDO_TEST" = "0" ]; do sudo -vn; EXIT_SUDO_TEST=$?; sleep 60; kill -0 "$PID" || exit; done &> /dev/null & fi return 0 } function get_list { SERVICE_NAME="status" ARGS="{ \"format\":\"$FORMAT\", \"service\":\"$SERVICE_NAME\" }" timeout --signal=SIGINT 10 curl -s -d "$ARGS" -X POST "$URL" > "/tmp/.eddie_server_list.txt" } function sort_list { # pipe server status list to awk, filter out unnecessary stuff, # combine lines that relate to same server into single lines which are saved as array, # loop through array to format info, # print array and sort according to options, # add numbers to list for menu LIST=$(awk -F '[.]' \ 'BEGIN{OFS=";"} \ /^servers/ && !/ip_/ && !/country_code/ {c=$2; \ if (c in servers) servers[c]=servers[c] OFS $3; \ else servers[c]=$3; \ for (k in servers) gsub(/;bw=/, " :", servers[k]); \ for (k in servers) gsub(/;bw_max=/, "/", servers[k]); \ for (k in servers) gsub(/;currentload=/, " :", servers[k]); \ for (k in servers) gsub(/;health=/, "%:", servers[k]); \ for (k in servers) gsub(/;.*=/, ":", servers[k]); \ for (k in servers) gsub(/^.*=/, "", servers[k])} \ END{ \ for (c in servers) print servers[c]}' "/tmp/.eddie_server_list.txt" | sort -t ":" $1 | awk -F '[;]' 'BEGIN{OFS=":"} {print v++";"$1}') } function get_userinfo { SERVICE_NAME="userinfo" ARGS="{ \"format\":\"$FORMAT\", \"service\":\"$SERVICE_NAME\", \"key\":\"$API_KEY\" }" # filter specific lines, save values to variables after protecting whitespace read U_LOGIN U_EXP U_CONNECTED U_DEVICE U_SERVER_NAME U_SERVER_COUNTRY U_SERVER_LOCATION U_TIME <<< $( \ timeout --signal=SIGINT 10 curl -s -d "$ARGS" -X POST "$URL" | \ awk -F '[=]' \ 'BEGIN{ORS=";"} \ /^user.login|^user.expiration_days|^user.connected|^sessions.*device_name|^connection.server_name|^connection.server_country=|^connection.server_location|^connection.connected_since_date/ \ {print $2}' | \ sed 's/\ /\\\ /g' | sed 's/;/\ /g' \ ) if [ "$U_CONNECTED" = "1" ] then U_CONNECTED="connected" U_SERVER_FULL="$U_SERVER_NAME ($U_SERVER_LOCATION, $U_SERVER_COUNTRY)" U_TIME=$(date -d "$U_TIME UTC" +"%m/%d/%Y %H:%M:%S") else U_CONNECTED="not connected" U_SERVER_FULL="--" U_TIME="--" fi } function connect_server { if [ "$KILLED" = "true" ] then # create pipes to process status of client if [ ! -p "/tmp/.eddie_fifo1" ] then mkfifo "/tmp/.eddie_fifo1" fi if [ ! -p "/tmp/.eddie_fifo2" ] then mkfifo "/tmp/.eddie_fifo2" fi # run eddie in background and detached from current window, pipe output to named pipe (sudo eddie-ui --cli --netlock --connect --server="$1" --profile="$PROFILE_PATH" | tee "/tmp/.eddie_fifo2" &> "/tmp/.eddie_fifo1" &) cat "/tmp/.eddie_fifo2" | dialog --backtitle "$BACKTITLE" --title "Connecting to AirVPN..." --progressbox 20 80 & timeout --signal=SIGINT 60 grep -q -m 1 "Initialization Sequence Completed" "/tmp/.eddie_fifo1" INIT_EXIT=$? pkill -f cat.*eddie_fifo2 if [ $INIT_EXIT = "0" ] then get_userinfo else U_CONNECTED="error during connection attempt" U_SERVER_FULL="--" U_TIME="--" fi else U_CONNECTED="error during disconnection" U_SERVER_FULL="--" U_TIME="--" fi } function disconnect_server { # check for running instance of eddie pgrep -f mono.*eddie-ui &> /dev/null if [ $? = 0 ] then # kill process and wait for confirmation from process output if [ -p "/tmp/.eddie_fifo1" -a -p "/tmp/.eddie_fifo2" ] then sudo pkill -2 -f mono.*eddie-ui & cat "/tmp/.eddie_fifo1" | dialog --backtitle "$BACKTITLE" --title "Disconnecting AirVPN..." --progressbox 20 80 & timeout --signal=SIGINT 10 grep -q -m 1 "Shutdown complete" "/tmp/.eddie_fifo2" else # in case connection was started without this script sudo pkill -2 -f mono.*eddie-ui sleep 5 fi # give some time to completely close process, without sleep it's too early for new connection sleep 3 pgrep -f mono.*eddie-ui &> /dev/null if [ $? = 1 ] then KILLED1="true" else KILLED1="false" fi else KILLED1="true" fi # check for running instance of openconnect pgrep -f "openconnect.*--" &> /dev/null if [ $? = 0 ] then sudo pkill -2 -f "openconnect.*--" sleep 1 pgrep -f "openconnect.*--" &> /dev/null if [ $? = 1 ] then KILLED2="true" # somehow openconnect doesn't receive SIGINT and shuts down improperly, # so vpnc can't restore resolv.conf by itself sudo cp "/var/run/vpnc/resolv.conf-backup" "/etc/resolv.conf" else KILLED2="false" fi else KILLED2="true" fi if [ "$KILLED1" = "true" -a "$KILLED2" = "true" ] then KILLED="true" else KILLED="false" fi } function define_lock { if [ "$1" = "activate" ] then GAUGE_TITLE="Activating Network Lock" RULE_ACTION="add-rule" elif [ "$1" = "deactivate" ] then GAUGE_TITLE="Deactivating Network Lock" RULE_ACTION="remove-rule" else return 1 fi GAUGE_BODY="$1" IPRULES=(\ #allow loopback "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv4 filter INPUT 0 -i lo -j ACCEPT" \ "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv4 filter OUTPUT 0 -o lo -j ACCEPT" \ #allow lan (out) and broadcasting/dhcp "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv4 filter OUTPUT 0 -s 192.168.0.0/16 -d 192.168.0.0/16 -j ACCEPT" \ "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv4 filter INPUT 0 -s 255.255.255.255 -j ACCEPT" \ "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv4 filter OUTPUT 0 -d 255.255.255.255 -j ACCEPT" \ # allow tun device to communicate (so any VPN connection should be possible, also without Air, but respective DNS requests must be allowed) "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv4 filter FORWARD 0 -o tun+ -j ACCEPT" \ "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv4 filter FORWARD 0 -i tun+ -j ACCEPT" \ "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv4 filter OUTPUT 998 -o tun+ -j ACCEPT" \ # optional masquerade rule (NAT/ports) "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv4 nat POSTROUTING 0 -o tun+ -j MASQUERADE" \ # allow ipv4 only to airvpn.org for status update # allow DNS query to resolve hostname (hex string reads "06 airvpn 03 org" - numbers are counting bits), # restrict packet length to length of this specific request package (might change?) to avoid hijacking # of query (very unlikely I guess, but who cares if we're already being paranoid for the fun of it), # whitelist destination IP for TCP handshake "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv4 filter OUTPUT 1 -p udp --dport 53 -m string --hex-string '|06 61697276706e 03 6f7267|' --algo bm -m length --length 0:126 -m recent --set -j ACCEPT" \ "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv4 filter OUTPUT 1 -p tcp --dport 53 -m string --hex-string '|06 61697276706e 03 6f7267|' --algo bm -m length --length 0:126 -m recent --set -j ACCEPT" \ # add rules for other domains you wish to allow DNS requests to here (packet length can be determined with e.g. wireshark) and adjust array index # # allow SYN request to whitelisted IP to initiate handshake, remove IP from whitelist "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv4 filter OUTPUT 1 -p tcp --syn --dport 53 -m recent --remove -j ACCEPT" \ # allow outgoing connection to Air's IP "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv4 filter OUTPUT 1 -d 5.196.64.52 -j ACCEPT" \ # add rules for other IPs you wish to allow connections to here # # allow communication "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv4 filter INPUT 1 -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT" \ # drop outgoing ipv4 (if not specifically allowed by other rules) "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv4 filter OUTPUT 999 -j DROP" \ # block incoming ipv4 "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv4 filter INPUT 999 -j DROP" \ # drop all ipv6 "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv6 filter OUTPUT 0 -j DROP" \ "sudo firewall-cmd --direct --permanent --$RULE_ACTION ipv6 filter INPUT 0 -j DROP" \ # reload and restart firewalld to activate permanent rule changes "sudo firewall-cmd --reload" \ "sudo systemctl restart firewalld"\ ) toggle_lock } function toggle_lock { PERCENTAGE_STEP=$(awk -v rules="${#IPRULES[@]}" 'BEGIN {print 100/rules}') PERCENTAGE=0 COUNTER=0 # initial window dialog --backtitle "$BACKTITLE" \ --title "$GAUGE_TITLE" \ --mixedgauge "Applying iptable rules to $GAUGE_BODY the default network lock..." 35 80 "$(awk -v per="$PERCENTAGE" 'BEGIN {printf "%.0f", per}')" \ "Allow Loopback IN" "${RESULT[0]}" \ "Allow Loopback OUT" "${RESULT[1]}" \ "Allow LAN OUT" "${RESULT[2]}" \ "Allow DHCP IN" "${RESULT[3]}" \ "Allow DHCP OUT" "${RESULT[4]}" \ "Allow tun out FORWARD" "${RESULT[5]}" \ "Allow tun in FORWARD" "${RESULT[6]}" \ "Allow tun out OUT" "${RESULT[7]}" \ "tun masquerade" "${RESULT[8]}" \ "Allow DNS via UDP to airvpn.org" "${RESULT[9]}" \ "Allow DNS via TCP to airvpn.org" "${RESULT[10]}" \ "Allow connection initiation" "${RESULT[11]}" \ "Allow traffic to airvpn.org" "${RESULT[12]}" \ "Allow established connections" "${RESULT[13]}" \ "Block IPv4 OUT" "${RESULT[14]}" \ "Block IPv4 IN" "${RESULT[15]}" \ "Block IPv6 OUT" "${RESULT[16]}" \ "Block IPv6 IN" "${RESULT[17]}" \ "activate changes" "${RESULT[18]}" \ "restart firewalld" "${RESULT[19]}" for i in "${IPRULES[@]}" do RESULT["$COUNTER"]=$(eval $i) (( COUNTER++ )) PERCENTAGE=$(awk -v per="$PERCENTAGE" -v per_step="$PERCENTAGE_STEP" 'BEGIN {print per+per_step}') # progress window dialog --backtitle "$BACKTITLE" \ --title "$GAUGE_TITLE" \ --mixedgauge "Applying iptable rules to $GAUGE_BODY the default network lock..." 35 80 "$(awk -v per="$PERCENTAGE" 'BEGIN {printf "%.0f", per}')" \ "Allow Loopback IN" "${RESULT[0]}" \ "Allow Loopback OUT" "${RESULT[1]}" \ "Allow LAN OUT" "${RESULT[2]}" \ "Allow DHCP IN" "${RESULT[3]}" \ "Allow DHCP OUT" "${RESULT[4]}" \ "Allow tun out FORWARD" "${RESULT[5]}" \ "Allow tun in FORWARD" "${RESULT[6]}" \ "Allow tun out OUT" "${RESULT[7]}" \ "tun masquerade" "${RESULT[8]}" \ "Allow DNS via UDP to airvpn.org" "${RESULT[9]}" \ "Allow DNS via TCP to airvpn.org" "${RESULT[10]}" \ "Allow connection initiation" "${RESULT[11]}" \ "Allow traffic to airvpn.org" "${RESULT[12]}" \ "Allow established connections" "${RESULT[13]}" \ "Block IPv4 OUT" "${RESULT[14]}" \ "Block IPv4 IN" "${RESULT[15]}" \ "Block IPv6 OUT" "${RESULT[16]}" \ "Block IPv6 IN" "${RESULT[17]}" \ "activate changes" "${RESULT[18]}" \ "restart firewalld" "${RESULT[19]}" done # final window to show results dialog --backtitle "$BACKTITLE" \ --title "$GAUGE_TITLE" \ --mixedgauge "Applying iptable rules to $GAUGE_BODY the default network lock..." 35 80 "$(awk -v per="$PERCENTAGE" 'BEGIN {printf "%.0f", per}')" \ "Allow Loopback IN" "${RESULT[0]}" \ "Allow Loopback OUT" "${RESULT[1]}" \ "Allow LAN OUT" "${RESULT[2]}" \ "Allow DHCP IN" "${RESULT[3]}" \ "Allow DHCP OUT" "${RESULT[4]}" \ "Allow tun out FORWARD" "${RESULT[5]}" \ "Allow tun in FORWARD" "${RESULT[6]}" \ "Allow tun out OUT" "${RESULT[7]}" \ "tun masquerade" "${RESULT[8]}" \ "Allow DNS via UDP to airvpn.org" "${RESULT[9]}" \ "Allow DNS via TCP to airvpn.org" "${RESULT[10]}" \ "Allow connection initiation" "${RESULT[11]}" \ "Allow traffic to airvpn.org" "${RESULT[12]}" \ "Allow established connections" "${RESULT[13]}" \ "Block IPv4 OUT" "${RESULT[14]}" \ "Block IPv4 IN" "${RESULT[15]}" \ "Block IPv6 OUT" "${RESULT[16]}" \ "Block IPv6 IN" "${RESULT[17]}" \ "activate changes" "${RESULT[18]}" \ "restart firewalld" "${RESULT[19]}" sleep 2 unset RESULT check_lock } function check_lock { # check for success (not really though, needs improvement) LOCK_RULES=$( sudo firewall-cmd --direct --permanent --get-all-rules | wc -l ) if [ "$LOCK_RULES" -gt 16 ] then LOCK_ACTIVE="active" else LOCK_ACTIVE="inactive" fi } function yesno { dialog \ --backtitle "$BACKTITLE" \ --title "$1" \ --clear \ --yesno "$2" \ $HEIGHT $WIDTH EXIT_STATUS=$? } check_sudo if [ $? = "1" ] then clear exit fi get_userinfo # if currently connected by openconnect, set status to unknown (connection could have been established outside of this script) pgrep openconnect &> /dev/null if [ $? = 0 ] then U_CONNECTED="connected (openconnect)" U_SERVER_FULL="unknown" U_TIME="unknown" fi check_lock while true; do exec 3>&1 selection=$(dialog \ --cr-wrap \ --backtitle "$BACKTITLE" \ --title "Main Menu" \ --clear \ --cancel-label "Quit" \ --menu "This is a control script for VPN connections, primarily for Eddie, the AirVPN client.\nThis script can be exited and re-entered without affecting a running connection.\n\nUser: $U_LOGIN\nDays Until Expiration: $U_EXP\n\nDefault Network Lock: $LOCK_ACTIVE\n\nStatus: $U_CONNECTED\nServer: $U_SERVER_FULL\nConnected Since: $U_TIME\n\nPlease select one of the following options:" $HEIGHT $WIDTH 6 \ "0" "Connect to Recommended Server" \ "1" "Connect to Specific Server" \ "2" "Connect via openconnect" \ "3" "Disconnect" \ "4" "Refresh User Info" \ "5" "Toggle Default Network Lock" \ 2>&1 1>&3) EXIT_STATUS=$? exec 3>&- case $EXIT_STATUS in $DIALOG_CANCEL|$DIALOG_ESC) yesno "Quit" "Exit Script?" case $EXIT_STATUS in $DIALOG_CANCEL|$DIALOG_ESC) ;; $DIALOG_OK) break ;; esac ;; esac case $selection in 0 ) check_sudo if [ $? = "0" ] then disconnect_server connect_server "" fi ;; 1 ) while true; do exec 3>&1 SERVER_SORT=$(dialog \ --backtitle "$BACKTITLE" \ --title "Sort Server List" \ --no-collapse \ --ok-label "sort ascending" \ --extra-button \ --extra-label "sort descending" \ --menu "Please choose how you want to sort the server list." \ 14 0 7 \ "1" "Name" \ "2" "Country" \ "3" "Location" \ "4" "Continent" \ "5" "Bandwidth" \ "6" "Users" \ "7" "Load" \ 2>&1 1>&3) EXIT_STATUS=$? exec 3>&- case $EXIT_STATUS in $DIALOG_CANCEL|$DIALOG_ESC) break ;; $DIALOG_EXTRA) SERVER_SORT_OPTION="r" ;; $DIALOG_OK) SERVER_SORT_OPTION="" ;; esac if [ "$SERVER_SORT" = "5" -o "$SERVER_SORT" = "6" -o "$SERVER_SORT" = "7" ] then SERVER_NUM_OPTION="n" else SERVER_NUM_OPTION="" fi if [ ! -f "/tmp/.eddie_server_list.txt" ] then get_list fi while true do sort_list "-k$SERVER_SORT,$SERVER_SORT$SERVER_SORT_OPTION$SERVER_NUM_OPTION" IFS=$';\n' exec 3>&1 SERVER_NMBR=$(dialog \ --backtitle "$BACKTITLE" \ --title "Server List" \ --colors \ --no-collapse \ --extra-button \ --extra-label "Refresh List" \ --column-separator ":" \ --menu "Choose a server from the list to connect to it. (Press ESC to go back.)\n\n\Zb # Name Country Location Continent Bandwidth Users Load Health\ZB" \ 40 102 31 $LIST 2>&1 1>&3) EXIT_STATUS=$? exec 3>&- IFS=$' \t\n' case $EXIT_STATUS in $DIALOG_CANCEL) break 2 ;; $DIALOG_ESC) break ;; $DIALOG_EXTRA) get_list ;; $DIALOG_OK) check_sudo if [ $? = "0" ] then SELECTED_SERVER=$(printf -- '%s\n' "${LIST[@]}" | grep "^$SERVER_NMBR;" | cut -d ";" -f 2 | cut -d ":" -f 1) disconnect_server connect_server "$SELECTED_SERVER" break 2 fi ;; esac done done ;; 2 ) exec 3>&1 # adjust field lengths if necessary CONNECT_INFO=$(dialog \ --backtitle "$BACKTITLE" \ --title "VPN via openconnect" \ --insecure \ --mixedform "Please provide your login credentials to connect to a VPN via openconnect:\n(Leave unneeded fields blank and type options as in command line, separated by space.)" $HEIGHT $WIDTH 6 \ "Server:" 1 1 "" 1 21 25 0 0 \ "Group:" 2 1 "" 2 21 25 0 0 \ "User:" 3 1 "" 3 21 25 0 0 \ "Password:" 4 1 "" 4 21 25 0 1 \ "Additional Options:" 5 1 "" 5 21 25 0 0 \ 2>&1 1>&3) EXIT_STATUS=$? exec 3>&- case $EXIT_STATUS in $DIALOG_CANCEL|$DIALOG_ESC) ;; $DIALOG_OK) check_sudo if [ $? = "0" ] then disconnect_server if [ "$KILLED" = "true" ] then if [ ! -p "/tmp/.eddie_fifo1" ] then mkfifo "/tmp/.eddie_fifo1" fi ALT_SERVER=$(echo -n "$CONNECT_INFO" | cut -d$'\n' -f 1) ALT_GROUP=$(echo -n "$CONNECT_INFO" | cut -d$'\n' -f 2) ALT_USER=$(echo -n "$CONNECT_INFO" | cut -d$'\n' -f 3) ALT_PASS=$(echo -n "$CONNECT_INFO" | cut -d$'\n' -f 4) ALT_OPTS=$(echo -n "$CONNECT_INFO" | cut -d$'\n' -f 5) echo "$ALT_PASS" | (sudo openconnect $ALT_OPTS --authgroup=$ALT_GROUP --user=$ALT_USER --passwd-on-stdin $ALT_SERVER &> "/tmp/.eddie_fifo1" &) timeout --signal=SIGINT 3 cat "/tmp/.eddie_fifo1" | dialog --backtitle "$BACKTITLE" --title "Connecting via openconnect..." --timeout 5 --programbox 20 80 U_CONNECTED="connected" U_SERVER_FULL="$ALT_SERVER" U_TIME=$(date +"%m/%d/%Y %H:%M:%S") else U_CONNECTED="error during disconnection" U_SERVER_FULL="--" U_TIME="--" fi fi ;; esac ;; 3 ) check_sudo if [ $? = "0" ] then disconnect_server if [ "$KILLED" = "true" ] then get_userinfo else U_CONNECTED="error during disconnection" U_SERVER_FULL="--" U_TIME="--" fi if [ -p "/tmp/.eddie_fifo1" ] then rm "/tmp/.eddie_fifo1" fi if [ -p "/tmp/.eddie_fifo2" ] then rm "/tmp/.eddie_fifo2" fi fi ;; 4 ) get_userinfo ;; 5 ) pgrep -f mono.*eddie-ui &> /dev/null if [ $? = 0 ] then dialog --backtitle "$BACKTITLE" --title "Toggle Network Lock" --timeout 3 --msgbox "You need to be disconnected to change network traffic rules." 10 35 else if [ "$LOCK_ACTIVE" = "inactive" ] then yesno "Toggle Network Lock" "Are you sure you want to activate the default network lock and block all connections while not connected to (any) VPN?" case $EXIT_STATUS in $DIALOG_CANCEL|$DIALOG_ESC) ;; $DIALOG_OK) check_sudo if [ $? = "0" ] then define_lock "activate" fi ;; esac else yesno "Toggle Network Lock" "Are you sure you want to deactivate the default network lock and allow all connections, even when not connected to a VPN?" case $EXIT_STATUS in $DIALOG_CANCEL|$DIALOG_ESC) ;; $DIALOG_OK) check_sudo if [ $? = "0" ] then define_lock "deactivate" fi ;; esac fi fi ;; esac done clear
-
 LZ1 got a reaction from itsmefloraluca in FYI: Official NordVPN Android app transmits personal data to third parties ...
LZ1 got a reaction from itsmefloraluca in FYI: Official NordVPN Android app transmits personal data to third parties ...
Hello!
That's certainly interesting. Thank you for taking the time to post it here and making it available in English .
I completely agree that the choice of justification is very poor in this regard.
Moved topic to the proper forum.
-
 LZ1 reacted to OpenSourcerer in FYI: Official NordVPN Android app transmits personal data to third parties ...
LZ1 reacted to OpenSourcerer in FYI: Official NordVPN Android app transmits personal data to third parties ...
A german IT security blogger recently discovered that NordVPN's official android app transmits personally identifiable information to NordVPN and a few third parties.
The checked version of their app is v3.9.8 which seems a few versions behind the current branch but still fairly recent.
The blogger discovered that a user's Google mail address along with the advertising ID and a bit of other info are sent to Iterable, AppsFlyer and Tune along with some Google services like Analytics - all seemingly without the user's consent and even without mentioning it in the app's ToS.
Of course customer support has been asked as well. Their answer was not satisfactory:
Everyone interested in some of the HTTP POSTs discovered can look at them in the article linked above. The article itself is German-language, but it doesn't contain more info than this, only a bit of the writer's opinion which I share: It's very questionable that a "no-log" or even "privacy-centered" VPN provider like NordVPN is bold enough to state "marketing reasons" as their justification to track users of their Android app. Even worse that this tracking is performed by third parties who will most likely use this data in cross-referencing...
Try to avoid NordVPN. Searching for "NordVPN" in this forum alone will yield more than enough reason. One in three newly created threads is about them.
-
 LZ1 reacted to Staff in two sessions to same server causes 2 minute restarts ad infinitum ...
LZ1 reacted to Staff in two sessions to same server causes 2 minute restarts ad infinitum ...
Hello!
If you resolve a country or a continent or a planet name to determine which VPN server the system will connect to, what you experience is not a bug. When you connect multiple devices with the same key to the same OpenVPN daemon, only the last one receives properly packets, and will cause a disconnection to all the other ones. Not only this is not an OpenVPN bug, but this is a very appropriate and correct behavior: the opposite would be a real catastrophe!
Each computer can't know what any other is doing, unless you query Air API to determine the status of your account and make connection decisions accordingly. However, to connect multiple devices to the same servers, we already offer the option to use multiple client certificate/key pairs by the same account:
https://airvpn.org/topic/26209-how-to-manage-client-certificatekey-pairs
The other problem you mention. i.e. that a VPN server which goes down is still the "best" server according to some FQDN, is due to TTL. Actually, our authoritative DNS update the records every 2 minutes, but TTL is 1 hour, so on average you might have some DNS server updating the records after 30 minutes.
Now that you know that this is not true, let's go deeper into the matter. An OpenVPN daemon runs always in the same core of a CPU. Even with AES-NI supporting CPUs, it's impossible, with our ciphers, to squeeze the full bandwidth we have available. Therefore, some sort of balancing becomes necessary.
Last year we implemented a new balancing system which turned out to work very well. Each VPN server runs as many OpenVPN daemons as possible (according to the CPU cores amount), and each daemon lives in its own private subnet. Servers welcome OpenVPN clients at kernel level by sending them to the OpenVPN daemon which is running in the least loaded core. It was a huge improvement when compared to the previous, relatively rudimentary in comparison, load balancing.
In this way we have been able to break the previous 900 Mbit/s limit on a single server (we touched around 1.7 Gbit/s on a server with hundreds of connected clients).
Therefore, when multiple clients with the same pair connect to the same VPN server, they might have no problems if they are sent to different OpenVPN daemons. However, the likelihood that it happens when such connections occur at the same time is very tiny, because load core competition can cause a core supremacy change in a longer time, given the redundancy of our infrastructure. Anyway, it's not the correct approach, as you experienced.
Our users who want to achieve the purpose need therefore to take care, as it is perfectly normal and somehow even trivial, of their own devices by managing correctly the client pairs. It's a 30 seconds job in general and we provide all the necessary tools with an extremely comfortable graphic interface, both on our web site and in our free and open source software for Android, Linux, Mac and Windows.
Kind regards
P.S. We fixed the typo in the thread ("ad infinitem" --> "ad infinitum")
-
 LZ1 reacted to OpenSourcerer in Android tv box verliert Verbindung ~60 min ...
LZ1 reacted to OpenSourcerer in Android tv box verliert Verbindung ~60 min ...
It's a freaking disease, ever since Mr. wolke68 started a thread in german...
-
 LZ1 got a reaction from flat4 in What's your e-mail provider? ...
LZ1 got a reaction from flat4 in What's your e-mail provider? ...
Hello!
I don't think it has been mentioned, so I thought it would be relevant to point out that AirVPN doesn't require the use of a valid e-mail account in order to sign up.
-
 LZ1 reacted to ixochina in Alternative for China 2018 (a second VPN) ...
LZ1 reacted to ixochina in Alternative for China 2018 (a second VPN) ...
I can personally confirm that TCP port 443 works always and UDP as well - but not as always as TCP. We are into 2019 and still Airvpn is working perfectly in China. Connecting via Eddie is a sure way to go.
-
 LZ1 reacted to OpenSourcerer in Guide To Getting Started + Links For Advanced Users ...
LZ1 reacted to OpenSourcerer in Guide To Getting Started + Links For Advanced Users ...
... Kitalpha being the only exception due to missing IPv6 support, rest of the features are there. Makes it a Gen1.9 server.
I'm beginning to like these summaries..
-
 LZ1 got a reaction from Freejumping in Eddie and Fire Stick ...
LZ1 got a reaction from Freejumping in Eddie and Fire Stick ...
For reference, in case anyone wondered.