-
Content Count
11392 -
Joined
... -
Last visited
... -
Days Won
1982
Posts posted by Staff
-
-
The support answers typically take 1-2 hours (4-5 hours during the weekend nights, CET). If you did not receive any reply please check your spam folder and anyway re-send your support request. You can also elaborate your problem here in the forum, if you wish so.
I allowed 48 hours during the week. Not a weekend. And I had to transmit the requested logs three times before anyone appeared to notice, and whomever I corresponded with agrees that they don't show a single thing out of the ordinary.
Hello!
Maybe some communication problems? The support is much faster than 48 hours.
I'm having the same problem as some other people I've seen on the forum: I'm getting 4/4Mbps through nodes that are not heavily used. Everything on my end is, essentially, perfect, and AirVPN is the only service or protocol or site I access that has this limitation, so I'm going to go ahead and say: it's got to be AirVPN.
Of course it can't be excluded: if there's "bad peering" between all our datacenters bandwidth providers and your ISP, unfortunately this can't be resolved. Although we are careful to put servers in datacenters with POPs connected directly to tier1 and tier2 providers, it's impossible to have a 100% certainty to have good peering/latency/routing etc. with all the ISPs in the world... this is just how the Internet works.
I'm a systems and networks administrator. I've been doing this for over a decade. My router/firewall machine is a Core i5-2500. Four cores, 16GiB of RAM. It's lightly loaded. This is not a problem with a crappy little MIPS32 router at 400MHz or 680MHz. And I'm using a full install of Ubuntu Server 12.04.1 LTS with very few changes from defaults.
Ok, so it is probably safe to assume that the above cause is the most probable cause for your 16 Mbit/s performance.
I have a business-class connection through my ISP. I've never caught them throttling any other type of traffic, so finding that they throttle 443/tcp connections would be quite a surprise.
If you haven't already done so, please try connections over UDP ports (try them all), you might have better performance for obvious reasons. Or, you might notice packet fragmentation (which you can't notice with TCP of course), in which case you might fine-tune OpenVPN for higher performance as you probably already know.
Kind regards
-
Hello, i'm running your service behind a firewall that allows just VPN traffic and HTTP traffic. I've noticed that i cant stablish a conection via the UDP protocol on any port (53, 80, 443...), it always gives this error
Sun Nov 11 10:56:16 2012 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Sun Nov 11 10:56:16 2012 TLS Error: TLS handshake failed
Sun Nov 11 10:56:16 2012 TCP/UDP: Closing socket
It could be that my network is closed to UDP traffic but is open to TCP? Could I be able to bypass that block to UDP traffic?
Hello!
Yes, it looks like your firewall drops every outgoing (or maybe incoming, or both) UDP packet. This will cause several issues to the network users, lot applications can't just be used etc.
Just connect over a TCP port and you should be able to solve every problem. Encapsulating packets in TCP will also allow you to use all the applications which rely on UDP packets and that currently you can't use on your network.
Kind regards
-
Which Windows version are you using?
64 bit Windows 7 Ultimate
When you perform any change, close the preferences window and then you re-open it, are the changes lost?
no the changes will stay until i reboot, then the changes are lost.
one advantage is that i can choose the server with the least load, but i have to remember when i boot or reboot, i'm not automatically behind VPN because i have to manually start the program.
Hello!
Thank you very much for the information. We're sending all of them to the Air client programmer.
Kind regards
-
Hi I have recently purchased AirVPN mainly for torrenting. I use utorrent an would like to know how to set it up properly, as I have a set port and I have portforwarded it on the website but am getting a DANGER signal when checking it on the site.
I would appreciate a fast response.
Thanks
Hello!
Please see here:
If you get a red token on TCP, please make sure that you have NOT forwarded, on the router, the same port(s) you have remotely forwarded. The red token shows you that the port forwarding works, but that your device may be subject to some correlation attacks.
Kind regards
-
[quote name='"engagement" post=5479
1. Is a VM the same as HM?
Hello!
The host is the machine which "hosts" virtualized operating systems (the Virtual Machines' date=' also called "guests"). Typically the host is your computer with your OS.
2. Do you have any useful links with regards of step-by-step of setting up a HM/VM?There are several virtualization programs, amongst which VMWare and VirtualBox are particularly powerful and easy to use.
3. How difficult and what is needed to set up the HM/VM?You need a virtualization program, such as VirtualBox or VMWare, and and operating system to install on one of the Virtual Machines. Once done, you'll have a guest operating system (the new OS installed in the VM) running inside ("hosted") by your host OS.
See for example:
http://en.wikipedia.org/wiki/Virtualbox
4. Regarding Tor is it possible without a VM/HM to have Tor over VPN over VPN?In this case the main problem is not the part regarding TOR, because once you have established a connection over a VPN over a VPN, tunneling over TOR over VPN over VPN is trivial. The core problem is connecting a VPN over a VPN both with OpenVPN clients on the same machine which has one physical network card. There are several issues and if you don't master networking, routing tables and masquerading, then virtualization is a much, much simpler solution.
5. You said performance is slower with VPN over Tor - roughly how much slower percentage wise (a guess is ok)Unfortunately it's impossible to say: it depends on too many factors. In Italy (tested with very few ISPs only), usually the bandwidth by establishing Air (with Holland servers) over a "random" circuit on different days and times of the day oscillates from around 200 kbit/s to 600-700 kbit/s.
Kind regards
-
Do your direction support local to vpn to tor, or do your directions create local to tor to vpn?
Hello!
The following instructions show you how to connect over AirVPN over TOR:
In the above case all the programs will be tunneled over OpenVPN over TOR, leaving open the option to additionally add another tunnel (proxy over Air over TOR, TOR over Air over TOR, VPN over Air over TOR etc. etc.).
In order instead to connect over TOR over AirVPN: first connect to an Air server, then launch TOR. In this case only the programs that are configured to tunnel over TOR will be tunneled over TOR over OpenVPN. The programs not using TOR will be tunneled over OpenVPN alone.
Kind regards
-
I'm still having the same issues.
I was connected to a server, manually disconnected.
I'm trying to connect to Phoenicus via TCP and it won't let me connect. Viscosity is saying invalid user name and password.
Here is the most recent VPN log:
Hello!
The connection, as you can see from the logs, was over UDP, not TCP. You might like to try a connection over TCP while we investigate.
Kind regards
-
I haven't tried TCP. Yet.
Should I go into the file configurator and make a set of connections solely based on the TCP protocol and work with them for awhile and see how it works?
Yes, if you can do that you might give us some useful information for troubleshooting. We will anyway try to reproduce your problem if you can't do that.
Is TCP just as secure?
Basically TCP protects against some replay attacks on top of OpenVPN protection, while with UDP the replay attacks are defeated with OpenVPN replay-protection sliding-window and time window, besides HMAC authentication.
https://airvpn.org/index.php?option=com_kunena&func=view&catid=3&id=3773&Itemid=142#3784
Kind regards
-
Does my connection log look like there were any issues going on?
Hello!
Actually not, no particular problem is displayed in them before the credentials rejection. What happens with a connection over a TCP port?
Kind regards
-
I haven't tried TCP. I thought UDP was the better type of connection?
What are you thoughts of OpenVPN over TCP vs. UDP?
Hello!
You're right, under a performance point of view UDP is better.
Please see here for more information:
https://airvpn.org/faq#udp_vs_tcp
Kind regards
-
I managed to connect to Sirius, but not after quite a bit of trouble in getting it working.
Hello!
Thank you for the information. If you try a connection over a TCP port do you have the same problem?
Kind regards
-
Yes, just yesterday.
Previously, I was able to switch servers on the fly.
Now, the top says I last tried X number of seconds and it failed as I am currently connected to the server I just disconnected from.
And at the bottom, it has my real IP addy and says I am not connected.
Viscosity continues to reject a connection saying my user name and/or password is incorrect.
Hello!
In the last 28 minutes your account has never connected and has tried no connections. If you tried the connection during this time window, can you please send us the Viscosity logs?
Kind regards
-
Hello!
We're looking into this. Did it start to happen to you since yesterday?
Kind regards
-
I'm connected now, but why the website said at the top that I was connected and at the bottom it gave my real ISP is strange.
Any ideas?
Hello!
Were you using different devices?
Kind regards
-
I was connected to Serpentis, and it disconnected by itself.
Now, when I try to connect to another server, it says can't connect on my Viscosity client.
The website said I am already connected to Sirius (which is the server I am trying to connect to) but my Viscosity is saying incorrect username and password.
How do I fix this?
Hello!
Your account is currently connected and exchanging data.
Please let us know at your convenience if the issue is solved.
Kind regards
-
Sorry if this is a stupid question but I am a newbie. I have just installed AirVPN, fired it up and am now using Vuze. Everything works perfectly but do I need to change any Vuze settings? Am I hidden?
Hello!
Normally you don't need to change any setting (but you might like to see anyway how to optimize p2p performance here: https://airvpn.org/faq#p2p ).
For additional security you can perform the following test while you are connected to the VPN:
Finally, you can consider to secure your connection against leaks in case of unexpected VPN disconnection. According to your system please see the guides that are linked in the announcement section of the forum. https://airvpn.org/forums
Kind regards
-
I need help figuring out why I can't get better than a 4/4Mbps connection to AirVPN. I've sent OpenVPN logs to AirVPN support as requested, and can't even get confirmation that anyone is working on the problem.
Hello!
The support answers typically take 1-2 hours (4-5 hours during the weekend nights, CET). If you did not receive any reply please check your spam folder and anyway re-send your support request. You can also elaborate your problem here in the forum, if you wish so.
Kind regards
-
I didn't see anything about the Romanian server Phoenicis in the forums, so I'll ask. What happened to Phoenicis? Will it be returned/replaced/moved?
I woke up this morning, checked out what happened on Air overnight and no Phoenicis. What ever happened, I'm the Admins had very good reasons for taking this course of action. Just curious is all.
More Swedish servers?
Hello!
Unfortunately Phoenicis crashed again and again. We are keeping the server unavailable to premium users while we investigate with the help of the datacenter technicians.
Kind regards
-
I'm using:
Windows 8 (I'm actually liking it thus far, well minus the whole start screen interface thing)
Air VPN Client
As well as the recommended setup for COMODO Firewall (managed to get the settings right on the second go through, *success*)
Hello!
In this case you can't have a DNS leak, the rules will prevent all of them.
[Additional Question] ISP's rated internet speed: 30 MB/s download, My normal speed test average: 43 MB/s download, My new average speed test while using a Air VPN server that is a little bit over 2000 miles away from me: 51.5 MB/s. How does this even make the slightest bit of sense!?
Even assuming that you mean Mbit/s instead of MB/s, it's quite odd. Maybe your ISP allows bandwidth bursts?
Kind regards
-
Hello!
Please re-read, you have been given all the elements on how such attacks have the chance to be successful. In particular, to achieve the scope the adversary, in addition to regularly signed certificates, needs to block TOR or increase significantly the probability that the circuit is established with nodes controlled by the attacker (see the previous message for more details).
You seem to not understand. Even if a website's SSL certificate is compromised, a VPN will not protect you. The data will be sniffed. So this argument is not against Tor alone, but all services. Are you actually arguing that using an OpenVPN will protect you from this type of attack? Are you joking?
Hello!
The VPN will effectively protect the victim because it lets him/her to get out of the cage.
Second, as for blocking Tor, so what? What does this accomplish?
It accomplishes (and accomplished in reality) the attacker purpose. Please note that there's a significant difference between blocking TOR and handling the routes so that the probability that the wished by the attacker circuit is established.
Third, as for an attacker gaining control of the network to such an extent and to manipulate it and then compromise a website's SSL certificate or to forge it, in the hope that some nameless anonymous individual's login credentials are sniffed is so far out in left field it is a joke.
Unfortunately the purposes of the attackers in the past were more sinister. Catching the login credentials and exchanged data of activists in Skype, GMail and Facebook is very useful for a human rights hostile regime. Actually, when 300.000 iranian citizens suffered this attack, and the attack was successful (see the previous link about the incident), the purposes were essentially repression and control.
Do you remember the link you gave in the other thread that “proved” you argument, when in fact it did the opposite, do you remember what the original poster stated? Virtually no one used Tor for sensitive content—all sniffed data was on port 80.
That was a significant example, a proof of concept to show you the basis of more sophisticated MITM of SSL attacks.
The fact remains—this whole argument applies to all services, including the AirVPN. The only difference is that supposedly, the attacker gained control of the Tor network, but of course the VPN operator, who can not be tempted to sniff data traffic like the Tor exit node operator, is exempt. Why?
It should appear quite obvious to the careful reader. While with AirVPN this problem is solved with partition of trust (which not necessarily requires TOR), you can't perform partition of trust with TOR alone in the depicted scenario. In that case, the only remaining option to the attacker is disrupting OpenVPN connections (we will soon provide an additional service to mitigate or even solve the problem of OpenVPN connections disruption).
Cannot the VPN operator, in addition to operating a server, also hack a website, so when people exit out of a single hop service, the data will be decrypted by the operator and/or his friends?
It's even worse: actually, as it was repeatedly showed, it is not necessary at all to hack a website to succeed with the attack. The main difference is that if you can't allow yourself to trust the Air operators, you can hide them all your real packet headers AND payloads, while you can't do that with TOR alone in the depicted scenario.
What is the difference? The difference is that with a single hop VPN service, the operator can see every one's IP address and see exactly where the traffic goes. And thus, he can more easily decide to hack any popular website and sniff all data to that encrypted website.
We have faced this problem since when we designed AirVPN, and our suggested solution is partition of trust, so that you have a service which you don't need to trust if you can't allow yourself to trust it. Additionally, we have designed the system so that (if the customer wishes so) no identity can be correlated to an account. In this case, the only option remaining to the attacker is perform correlations (typical vulnerability of any low latency "anonymity" network). However, timing attacks become extremely difficult with OpenVPN, and even more with OpenVPN over TOR, theoretically the only adversary that can successfully perform them is the global adversary.
Multi-hopping within the same VPN infrastructure (or within different VPNs owned by the same entity), while perfectly possible with Air, does not solve the problem unfortunately, since the operators can trivially correlate all the traffic amongst all the VPN servers, while multi-hopping with different VPNs owned by different entities which do not cooperate with each other, or with a connection over OpenVPN over a proxy, does. Of course you can solve the problem as well connecting over TOR|I2P|etc. over OpenVPN over TOR|I2P|etc. (but not TOR over OpenVPN, unfortunately), in which case you don't have to worry neither about a malignant VPN operator nor a malignant TOR|I2P|etc. exit node. In this case the target can only be defeated by an adversary who can control simultaneously the TOR exit nodes and the VPN server. That this VPN operators can be this adversary, i.e. that they can have the power of a government which can control ISPs and border routers, is an extraordinarily near zero probability.
TOR over OpenVPN does not solve the problem because, if you imagine a really nasty VPN operator, you can assume that he/she hi-jack TOR connections from the VPN server to which you connect to, in order to enhance greatly the probability that you establish a circuit where the exit node is controlled by the same nasty operator (but obviously he/she can't do that if you connect over OpenVPN over TOR).
The purpose of the previously mentioned attacks are the opposite, that is intercepting the traffic to the real website: the hi-jacking may be only at the login page, which may be absolutely necessary in order to allow (only if needed) the correct "interfacing" with the victim toward the real website. After that all the victim traffic comes and goes to the real website. On the victim side, the outgoing traffic is encrypted with the keys already known by the interface, which decrypts the victim traffic, re-encrypts it and sends it to the real website. On the victim inbound flow, the interface decrypts the traffic from the real website (in this phase, if it is wished, packet injections/packet forging are performed) re-encrypts it with the previous keys and sends it to the victim. It is a very similar thing which can be performed in corporate environments to check the payload of https traffic, for which vInspector has been designed, with the difference that in corporate environments certificates don't need to be properly signed or stolen.
I think you are sorely confounding many different things.
Let's make a step back before proceeding. Have you understood how the attack works and why it does not need to hack https website and/or authority servers, and how the SSL/TLS packets to and from the victim are decrypted and re-encrypted?
Absolutely not, this is not a fault of the original website (for example Google), which suffered no security breach. In the example the security breach was in a CA website, but in the given links (for example in the Wikipedia article and in its references) you can see how it is possible to do that without even breaching the security of the sites of an authority.
Yes, I am aware of that. I was not making specific references to any particular hack. The argument was that the breach was on a third party site; it was not the Tor service. Whether the third party site is CA website or Google, it matters little.
We have seen real cases in which the attack does not need neither a breach on any authority website nor a breach on any https website (see the links on the Wikipedia article). We are making specific references to real incidents which really occurred, while the impression (but this admin may well be wrong, no offense meant) is that you are facing the issue in a fantastic, ideal scenario, ignoring the incidents really occurred in the past years. It must be said also, for completeness, that some of the most critical TOR vulnerabilities have been fixed at the end of 2011 ( https://blog.torproject.org/blog/tor-02234-released-security-patches ), while critical vulnerabilities in OpenVPN have not been found until today.
Kind regards
-
If you are making the accusation that the Tor service and its network is insecure, because of fraudulent or compromised SSL certificates, then you need actual evidence to prove this. You cannot make general statements that SSL certificates can be compromised or issued fraudulently and that this could be used to decrypt Tor exit node traffic to compromised HTTPS websites but miraculously protect OpenVPN traffic.
Hello!
As shown, there are currently various known TOR exit nodes which perform exactly that.
In the previous scenario, as it was clearly stated, the attacker was able both to control the significant portion of the TOR network and had valid SSL certificates, regularly signed. In this way using AirVPN can defeat the attacker, simply because the attacker has full control of the border routers, the ISPs in its country and runs a significant number of the only TOR exit nodes (if any) available for establishing a circuit, but not of the networks out of its country. Actually, currently the only way for the attacker to solve this "problem" is only disrupting completely OpenVPN connections.
About the "normal circumstances" you cite, it would help that you define what these normal circumstances are, and anyway it can be a dangerous mistake to assume that such circumstances surely apply to tvhawaii or any other person.
By “normal,” I am here referring to Tor exit nodes (as in the original discussion, before you changed the definitions and the argument) and that data transmitted from Tor exit nodes is safe for encrypted websites, since the encryption of the third party website is independent of the Tor service and is assumed to be secure.
So, what makes you think that the above conditions are met for tvhawaii or any other person? This admin has showed you at least two scenarios in which this was not true, and several scenarios which actually occurred in the recent years, so without knowing the power of the adversary that a person must face, those assumptions can't be held generally true. In particular, the assumption that encryption of the third party website is secure is totally irrelevant: actually the attack does not require to compromise the https website at all.
And even if “a” third party website certificate is not secure, then neither a VPN service nor Tor will protect you when connecting to this compromised website.
The https website is NOT compromised: this is the essence of the attack, and this is the reason for which using a VPN protects the victim. As already stated, currently the only know method to solve this problem for the attacker is only disrupting OpenVPN connections to the victim, thus alerting him/her.
All HTTP traffic, whether a VPN or Tor, can be sniffed in transit.
No, the real header and payload can't be unencrypted when inside the VPN.
So once again, your argument is incorrect.
You're free to believe what you want to believe.

Kind regards
-
hi,
i tried to make AirVPN autostart "start with windows" but don't see the button "OK" (if there is one)
it doesn't seem to work checking/unchecking anything and just closing the window. (see image)
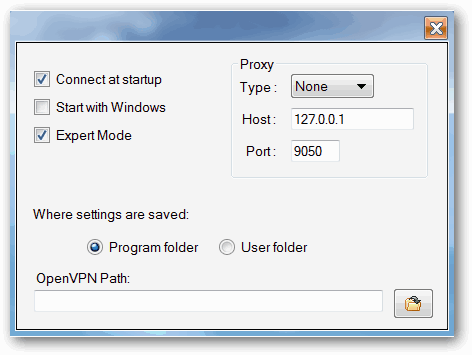
Hello!
That's strange, the Air client stores the information in that window just when you close it. Which Windows version are you using? When you perform any change, close the preferences window and then you re-open it, are the changes lost?
Kind regards
-
First and foremost thank you for the answers admin and the other person :-). Both are very helpful. I will be reseraching into setting up a host machine although this sounds extremely complicated and have no idea what this is just yet. Plus customizing Noscript better as there seem to be many options.
Few questions:
1. Does CCleaner do the same job as cookie monster?
Hello!
Unfortunately this admin knows only the Muppet character Cookie Monster and this Cookie Monster:
http://en.wikipedia.org/wiki/Cookie_Monster_%28computer_program%29
so no proper comparison is currently possible by this admin.
2. In my experience, the exit nodes I generally leave are servers and/or services I am familiar with and "trust."
How does one determine which Tor exit nodes are safe to use etc? Care to share? Also how to set it up? When I tried to set Tor so it didnt use exit nodes in USA it doesnt seem to work as dnsleaktest shows me with USA IP. Any suggestions?
It's very hard if not impossible to answer in a definitive manner to this question. The Tor Project gives some suggestions to lower the probability to establish a circuit with a malicious relay, please see here:
https://trac.torproject.org/projects/tor/wiki/doc/badRelays
3. How do you keep an eye for (LSOs) super flash cookies and what are they?
Local Shared Objects are files stored by Flash (for which they are also called Flash cookies; since they also vaguely remind cookies, they are also called Super Cookies). Their size is arbitrary, there's no theoretical limit to the amount of information which can be stored in them. They are perfect for websites to track users. They might be considered a browser potential security breach. "On 10 August 2009, Wired magazine reported that more than half of the top websites used local shared objects to track users and store information about them but only four of them mentioned it in their privacy policy."
http://en.wikipedia.org/wiki/Local_Shared_Object
You can delete them with options in Flash and you can refuse them by deactivating Flash. Since you use Firefox, an easy way to handle LSO (view, delete, automatic delete etc.) is Firefox add-on BetterPrivacy.
5. I thought my connection with AirVPN provided HTTPS security? How can I ensure I use this everywhere?
Your OpenVPN client works at a lower layer than http and https. It encrypts all your outgoing packets up to Air servers, and all your incoming packets from the server to you. Just like with any higher-layer operating protocol, http and https usage depends on you and the destination website, not on the VPN. For example, let's say that you connect to an Air server, and then to an http website which does not offer https. The data exchanged by you with the website are encrypted between you and the Air server. They remain encrypted between the server and you, so that your ISP (and anybody between you and Air servers) can't see them (neither the real header nor the payload). Once/when the http packets are out on the Internet (out of the VPN, that is), they are NOT encrypted but they never have your IP address.
Kind regards
-
65417 26.232188000 95.211.149.200 192.---.-.- IPv4 71 Fragmented IP protocol (proto=UDP 17, off=1480, ID=6eac) [Reassembled in #65419]65418 26.232464000 95.211.149.200 192.---.-.- IPv4 1506 Fragmented IP protocol (proto=UDP 17, off=0, ID=6eac) [Reassembled in #65419]
Wireshark is showing the above, last night the VPN dropped out could this be the cause, below is Air VPN logs, I have reinstalled windows.
Hello!
Yes, that can be the cause: the logs show a high packet loss. If the problem persists, please try a TCP connection, or tune your OpenVPN client, for example with mssfix. Please see here for details:
If you suffer significant performance loss with a TCP connection, then it's worth trying the above on an UDP connection. You can insert the directives directly in the .ovpn configuration file (anywhere). In this case you will have to use OpenVPN, not the Air client.
Please feel free to keep us updated.
Kind regards


Can't connect via UDP to any server
in General & Suggestions
Posted ...
Hello!
Latency is a parameter which is not controllable, but you should try all the servers to see which can give you the lowest latency. Our server monitor will help you, showing a latency which has no absolute value, but is useful to make comparisons. https://airvpn.org/status
Kind regards