
InactiveUser
-
Content Count
214 -
Joined
... -
Last visited
... -
Days Won
29
Posts posted by InactiveUser
-
-
how do I stop stunnel from running within termux?
First, enable the extended keyboard as described in the Addendum: Tips section.
Then you can press CTRL + c to stop stunnel.
-
I carefully followed this guide and configured everything accordingly.
Connectbot correctly starts ssh connection and port forwarding,
When I start openvpn it starts but the logs keep on saying
Connection reset, restarting [0]
SIGUSR1[soft,connection-reset] received, process restarting
and noting works...
I'm sorry for my late reply. Do you still need help?
If so, please tell me the version numbers of your apps and Android OS.
Also, please double-check that you excluded ConnectBot from OpenVPN's routing in the ALLOWED APPS tab.
-
Do i have to connect the the server specific .ssl?
or is okay if connect in Termux to lets say airvpn_NL.ssl and when connect in OpenVPN i use Bulgaria.ovpn?
The *.ssl files contain server-specific entry IP addresses and the *.ovpn files contain server-specific route addresses. Therefore you can't mix *.ovpn and *.ssl files from different servers.
Which is safer? AirVpn over SSL or SSH?
It don't think it makes a difference at all. The main purpose of SSL/SSH modes is firewall/censorship circumvention, not security. If your ISP does not block or throttle direct OpenVPN connections, I see little reason to use SSL or SSH.
-
@333_half_evil:
That's correct, please select Linux instead of Android.
If you selected Android, the SSL connection mode would be unavailable as it is not one of the officially supported modes for this platform. However, the generated config files for Linux work perfectly fine on Android. Only one adjustment is necessary, which is described in step #6 of part 1.
333_half_evil reacted to this -
Is there a reason why you are not using the stunnel app in android?
Yes, there are some reasons:
First, I have doubts regarding the app's maintenance status (last updated July 2015) and its obscure developer (website SmallApps.eu = 403 Forbidden).
Maybe most importantly though, I avoid recommending software that is exclusively available through proprietary channels (Google Play Store). There is no F-Droid version or access to source code available.
-
Thanks for your suggestions, mikevvl.
I do agree that it's generally a good idea to move those files out of shared storage. I'll add this suggestion to my "Tips" section.
Regarding your second suggestion: I wrote this tutorial with the goal of minimizing the number of required steps, which is why I won't be incorporating your second suggestion. While additional tweaks and scripts may improve EoU, they also add a certain level of complexity.
-
-
[accidental double post]
-
but when i run it with the widget, it says "Permission denied". Can anyone help me?
I think I know why: You're calling /bin/bash which likely does not exist on your phone. The shebang line (#!/bin/bash) is not necessary here, just leave it out. I've created a quick tutorial for Termux:Widget, including a small video, please try it out and compare it to your approach:
Termux:Widget usage
The following steps assume that you have successfully followed the main tutorial.
Instead of manually typing the two commands necessary to launch stunnel, we can do the same with a script. A script is nothing more than a text file that contains the commands we need to run.
Here is a video on Vimeo that demonstrates steps 3 to 6.
1. Create a text file with the following contents. Please adjust the second line to whatever server you happen to be using! For this tutorial, I'll be using the server BE-Brussels_Capricornus:
cd storage/shared/AirVPN stunnel AirVPN_BE-Brussels_Capricornus_SSL-443.ssl
2. Save the file; choose whatever file name you want, but make sure you use the .sh file extension. For this tutorial, I'll name the file:
capricornus.sh
Put your file into the AirVPN folder on your phone (the same folder you have already been using for the main tutorial).
3. Open Termux and run:
cd
This makes sure we are in stunnel's home directory. Now run:
mkdir .shortcuts
This will create a (hidden) folder that is required for Termux:Widget. That's where we need to copy our script to:
cp storage/shared/AirVPN/capricornus.sh .shortcuts
4. Leave Termux. Now install Termux:Widget from your preferred app store (FDroid or Google Play)
5. On your phone's home screen, enter your widget/wallpaper settings by long-pressing on a free spot on your home screen. Tap the WIDGETS button and find the Termux:Widget item.
Drag one of the Termux:Widget items onto your home screen. For this tutorial, I'll use the "All shortcuts 2x2" option.
6. You should now see your script listed within that new widget on your home screen. Tap on your script to run it.
7. You can add and use as many .sh scripts for different stunnel connections as you like, as long as you also create/generate the corresponding .ovpn and .ssl files.
-
I've tried using 22, 80 and 53, I get the same fail when editing the port forward.
I cannot reproduce your port forwarding error. Just to clarify: The purely local port fowarding is not affected by your choice of the AirVPN server port (22, 80, 53, 38915).
Port forwarding is always the same, forwarding 127.0.0.1:1412 to 127.0.0.1:2018.
I also don't understand the error message "ports under 1024 or port already used". No local ports under 1024 are involved. Is maybe another instance of sshtunnel, or some other app, somehow using 1412 or 2018?
What's your Android version? Works for me on 7 and 8.
Not directly related, but I should also add that some Air entry IPs don't listen on all of the SSH ports (22, 80, 53, 38915). That's why you can't just manually change the SSH port in your config files. Instead, use the Config Generator to generate new configs for your desired port in order to get the correct entry IP.
-
First off, sorry for not maintaining this thread, although the broad strokes of this guide still work to this day. I may write a new one if time permits.
Can I use OpenVPN on 443 port somehow on this with SSH on andriod? Port forwarding doesn't accept port below 1024 though.
Hi, same question here please.
I assume both of you want to want connect to Air's servers on port 443, using SSH?
That's currently not possible, but it's got nothing to do with your local port forwarding: Air's servers simply don't accept SSH connections on port 443.
The Config Generator only lists ports 22, 80, 53 and 38915 for SSH. I'd suggest opening a ticket to ask staff about the possibilities of SSH on 443. -
Attention everybody: A new and improved version of this tutorial can be found here:
https://airvpn.org/topic/24349-how-to-airvpn-via-sslstunnel-on-android-678/
-
Goal
We want to use AirVPN's SSL tunneling mode on Android. SSL tunneling can be very useful, especially to defeat firewalls that block OpenVPN or SSH on a protocol level. We will use the Termux Terminal Emulator to install and run stunnel and OpenVPN for Android to manage the OpenVPN connection.Requirements
- Android 6.0 or newer (5.0 and derivatives thereof such as FireOS should work too)
- the Android device does not have to be rooted
- Google PlayStore or the free & open source F-Droid market (recommended)
- OpenVPN for Android (FOSS) – or Air's official Eddie Android Edition Please stay tuned for future Eddie releases as they may include native SSL tunnel support (which would make this cumbersome guide unnecessary)
- Termux Terminal Emulator (FOSS)
- stunnel (FOSS), via Termux repository
- a separate computer to download/edit the config files (entirely optional, but recommended)
Setup instructions
Part 1: generate AirVPN config files
1/7: open AirVPN's config generator. When asked for your operating system, pick Linux: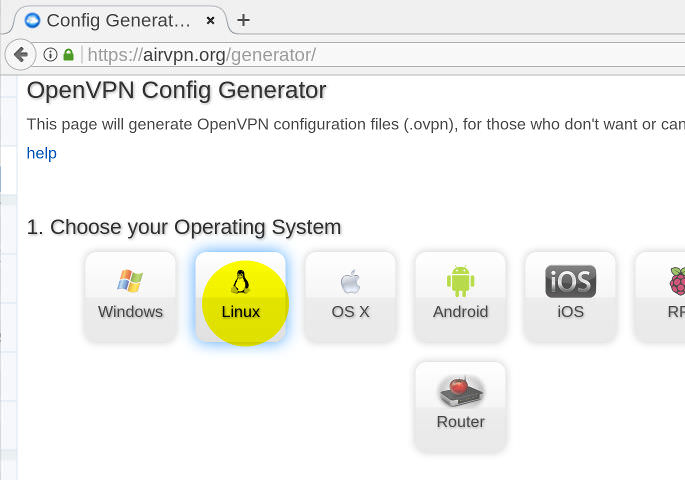
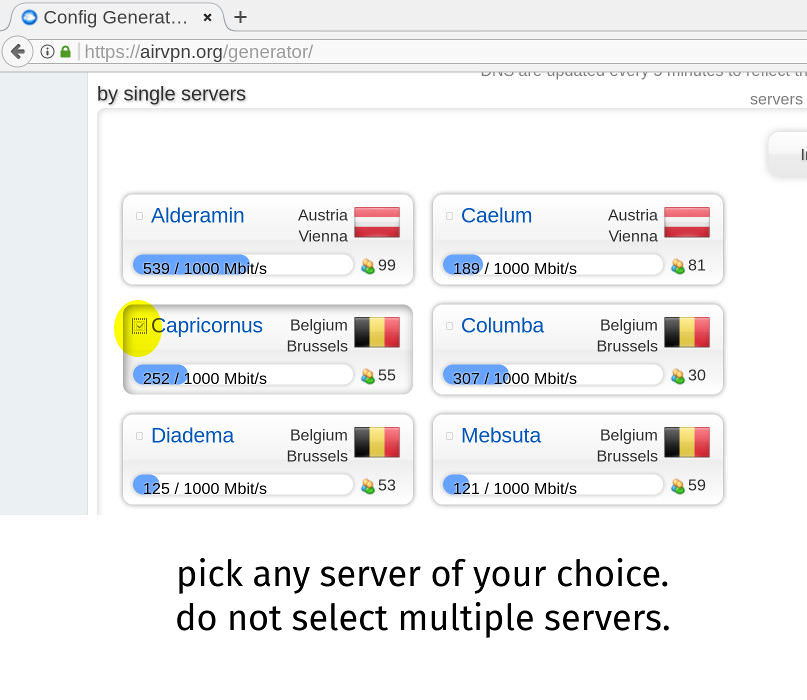
2/7: Choose servers: Pick a single server. Do not select more than one. Do not select a whole region.
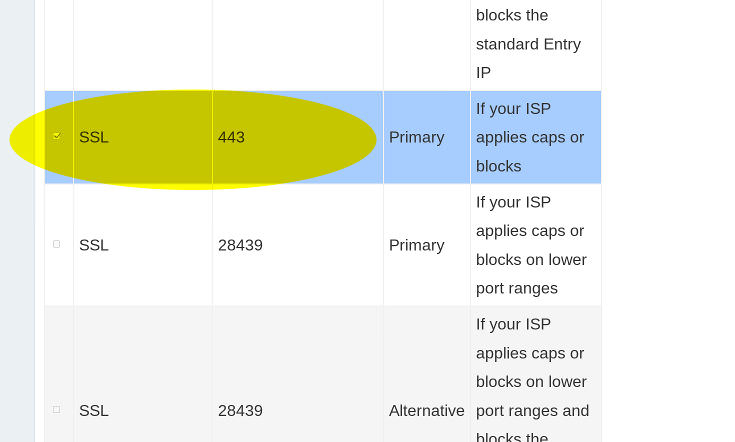
3/7: Protocols: First, enable Advanced Mode:

Now select the SSL mode, port 443:
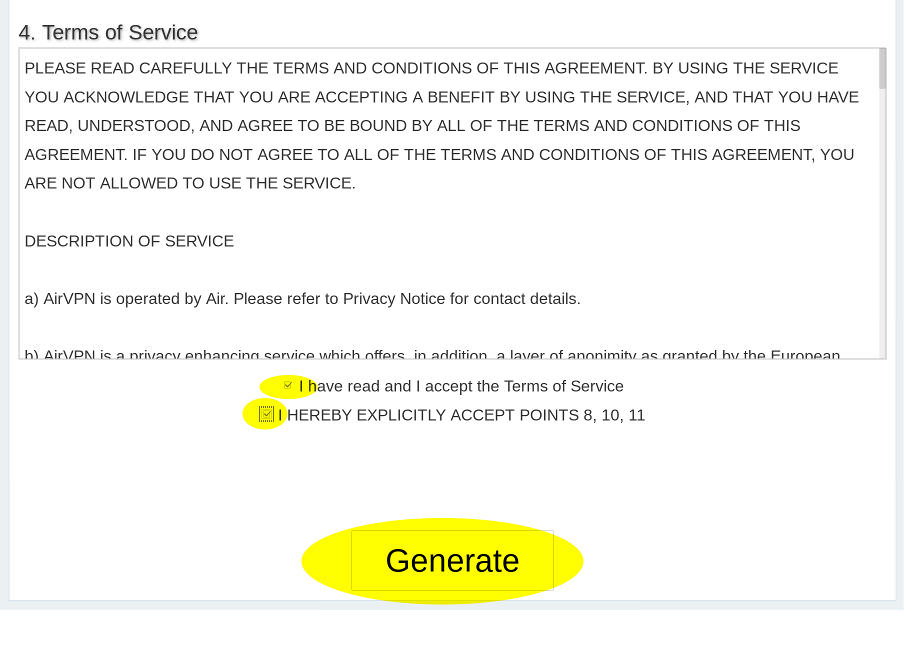
4/7: Accept Terms of Service and generate the config files:
5/7: Download the generated zip archive:
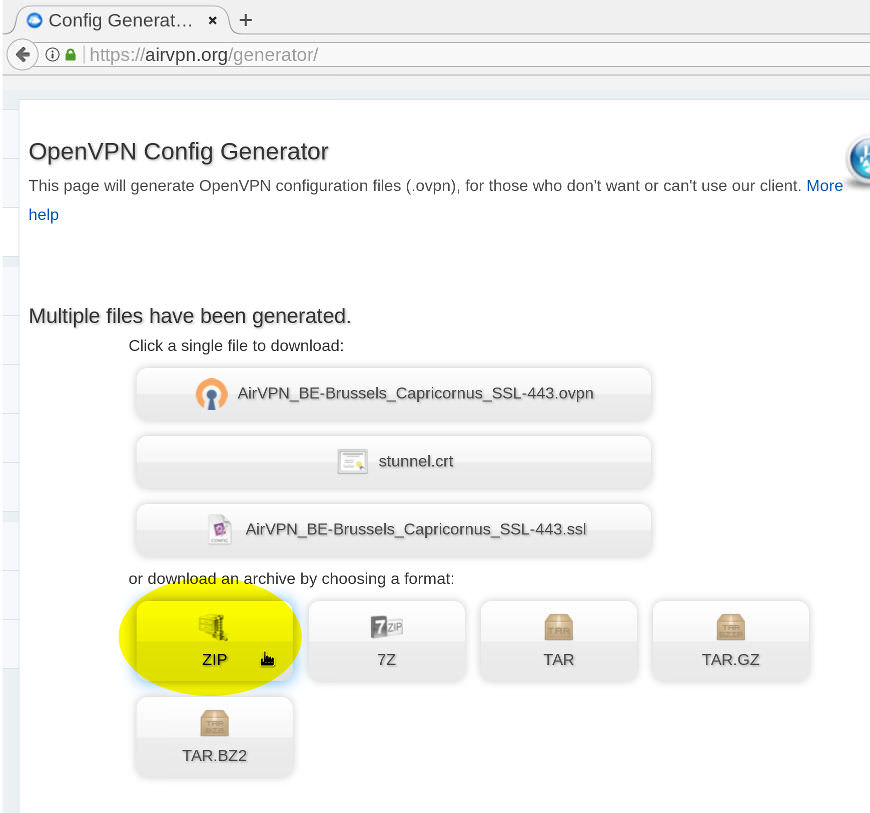
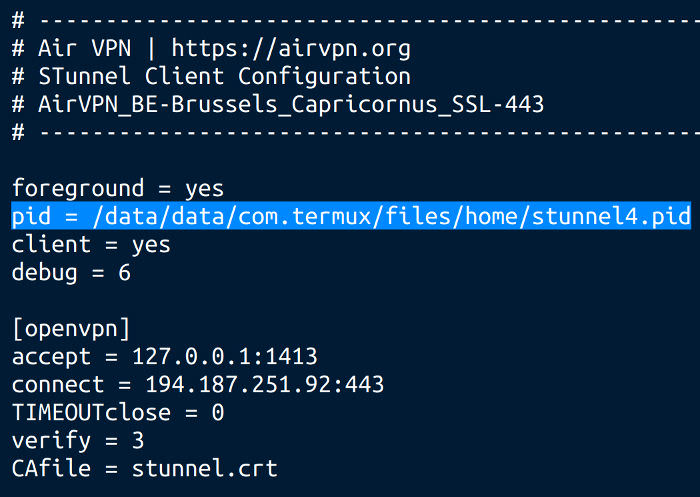
6/7: unzip AirVPN.zip and open the *.ssl file in a text editor.
find this line:pid = /tmp/stunnel4.pid
replace it with:
pid = /data/data/com.termux/files/home/stunnel4.pid
7/7: Now transfer the AirVPN folder to your phone's sdcard / main storage directory. For ease of use, don't put it into any subdirectories. Instead, put it into your "root" storage directory, meaning on the same level as your other default Android folders such as Documents, Download and Movies.
Part 2: Install and prepare Android software
1/3: Install OpenVPN for Android, via F-Droid or Play Store. Don't configure anything just yet.
2/3: Install Termux Terminal Emulator, via F-Droid or PlayStore- open Termux and run:
termux-setup-storage
- Allow Termux to access files on your device. (Android 8.0 Oreo users, please read the note at the end of this tutorial).
- The pkg command is used to install und update software packages. Make sure your base packages are all up to date:
pkg upgrade
- now install stunnel:
pkg install stunnel
3/3: Still in Termux, jump to the AirVPN folder you copied to your phone:
cd storage/shared/AirVPN
The command
ls
should list 3 files:
- AirVPN*.ovpn (the OpenVPN config file)
- AirVPN*.ssl (the stunnel config file)
- stunnel.crt (stunnel certificate)
Now start stunnel:
stunnel AirVPN*.ssl
- press the Home button to get out of Termux.
- Start OpenVPN and import the AirVPN*.ovpn config file
- Edit your new OpenVPN connection (tap the "pencil button")
- in the ALLOWED APPS tab, tick the box next to Termux
- return to OpenVPN's connection list
- your VPN connection is now configured. A tap on its name will establish the connection.
- verify that a connection has been established by looking for the log entry Initialization Sequence Completed
- browse to ipleak.net (or any similar site) to verify that your traffic is indeed routed through the VPN tunnel
Here's a short video, demonstrating the steps above: https://vimeo.com/246306477
Part 3: Usage instructions
Now that everything is configured, future usage will be much easier:
- open Termux
- navigate to your AirVPN folder:
cd storage/shared/AirVPN
- now run stunnel:
stunnel AirVPN*.ssl
- Press the Home button and open the OpenVPN app
- Connect to your VPN profile
Addendum: Tips- as an alternative to OpenVPN for Android, you can also use Air's official Eddie Android edition. Don't forget to dive into Eddie's settings to exclude ("blacklist") Termux from the VPN tunnel.
- don't forget to periodically run
pkg upgrade
to keep all of Termux' packages, including stunnel, up-to-date. - To prevent leaks, it's recommended to let OpenVPN set the default route for both IPv4 and IPv6; as well disabling the LAN bypass:
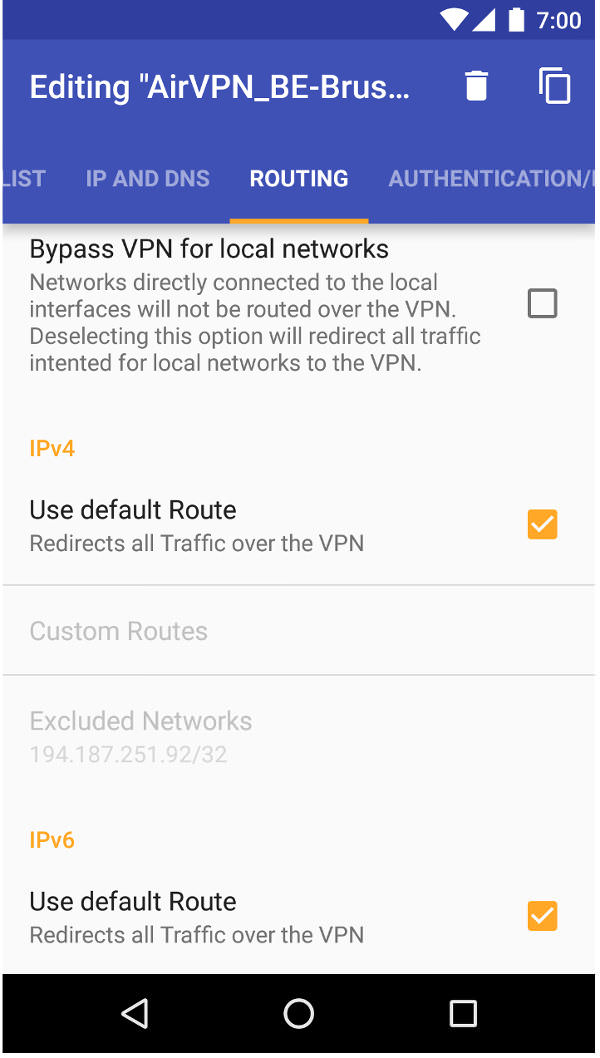
- you may want to take a look at Termux:Widget (via F-Droid or Play Store. It's an extension to Termux. If you put your stunnel commands into shell scripts, stored in ~/.shortcuts/ , you can launch them via Home screen widgets.
- enable Termux' extended keyboard by sliding out the left-side menu and long-pressing the KEYBOARD button. This will enable a row of additional keys, such as CTRL, ALT and TAB which are very useful in a terminal environment -- especially the TAB key, allowing you to autocomplete command and path names. Here's a short video on Vimeo demonstrating the extended keyboard.
- you may generate config files for as many servers as you like, put them into your AirVPN folder on your phone and add the *.ovpn profiles to OpenVPN.
- you may want to consider AFWall+ for additional firewalling (root required)
- it is recommended to move the *.ssl and stunnel.crt files out of Android's shared storage and into Termux' private data directory, while also deleting the no longer needed *.ovpn file:
cd ~ mkdir st cd storage/shared/AirVPN cp *.ssl stunnel.crt ~/st rm *.ssl stunnel.crt *.ovpn
Moving those files obviously changes the paths of your Termux commands. Instead of running:cd storage/shared/AirVPN stunnel AirVPN*.ssl
You'd now need to run:cd ~/st stunnel AirVPN*.ssl
Addendum: Caveats
- Following this tutorial will add the Termux app to OpenVPN's exclusion list, allowing it connect to the VPN server. But this also means that anything else you may do via Termux will also bypass the VPN tunnel. If you need a VPN-tunneled terminal app, I recommend using Termux only to run stunnel; using another terminal emulator app for your other tasks.
Addendum: Testing and bugs
This tutorial has been tested on:
- Stock Android 6.0
- Stock Android 7.0
- Stock Android 8.0
- LineageOS 14.1 (~ Android 7.1.x)
- Fire OS 5.6.0.0 (~ Android 5.x), testing done by user steve74it
Important Notice for Android 8.0+ (Oreo) users:
The command termux-setup-storage does not work (yet). Instead, follow this workaround to access storage:
https://github.com/termux/termux-app/issues/157#issuecomment-246659496
The workaround will no longer be necessary once this bug is resolved:
https://github.com/termux/termux-packages/issues/1578EDIT LOG
- Thu Dec 7 20:24 UTC 2017: initial release
- Thu Dec 7 20:40 UTC 2017: formatting corrections
- Thu Dec 7 20:58 UTC 2017: spelling
- Fri Dec 8 18:47 UTC 2017: add recommended route settings. credit and thanks to Darkspace-Harbinger
- Fri Jan 5 17:30 UTC 2018: add note that this guide is functional on FireOS 5.6 (Android 5.x). testing done by user steve74it, thank you!
- Mon Jan 22 18:34 UTC 2018: add mikevvl's security tip to move files out of shared storage. thank you!
- Sun Jul 15 12:16 UTC 2018: recommend against alternative VPN apps (thanks steve74it)
- Tue Jul 17 12:20 UTC 2018: mention Eddie compatibility (thanks steve74it)
Any corrections, further testing, as well as general suggestions for improvement would be much appreciated.
-
When will the next update? I have a hard time starting on my system.
Any ideas?
Thursday/Friday unless somebody else beats me to it.
-
DarkSpace-Harbinger's solution works, thanks! This whole tutorial needs a make-over, it contains too many outdated statements. I'll work on a new version soon, unless somebody else wants to take over which would be much appreciated. I'm not an Android power user at all.
-
I could establish a stunnel connection on android (light is green) but if if I start open vpn and try to connect I get:
NETWORK EOF ERROR
See attache files:
Happens with openvpn for android and openvpn connect.
Are you on Android 7.0 or newer? It looks like Android 7.0 introduced some changes that make it impossible to use OpenVPN through stunnel. Unfortunately, this tutorial is obsolete unless a solution is found.
Related bug reports:
https://www.stunnel.org/pipermail/stunnel-users/2017-October/005845.html
https://github.com/schwabe/ics-openvpn/issues/740
https://productforums.google.com/forum/#!topic/nexus/8SybHHQoEDg
-
[..] would it be a good idea to run a script on boot time to remove the 192.168 IP from this file, if my goal is to prevent DNS leaks?
Don't use scripts, NetworkManager will override your manual changes sooner or later. There is a more reliable way to get rid of your default DNS: Go into GNOME's network settings. Edit your Wi-Fi connection. Disable "automatic" DNS and configure Air's server instead. Screenshot attached.
-
Thanks zhang888, I agree you make a very valid point: Most of Firejail's flaws that are currently discussed don't concern sandbox escapes. Even in its current state, using firejail can go a long way to prevent certain classes of attacks. That said, I still feel squeamish about putting something on my system that is known to contain lots of avenues for privilege escalation.
-
* Analysis: Sandboxing is cool, but it has to be done right.
* Firejail has too broad attack surface that allows users
* to specify a lot of options, where one of them eventually
* broke by accessing user-files while running with euid 0.
* There are some other similar races. Turns out that it can be
* _very difficult_ to create a generic sandbox suid wrapper thats
* secure but still flexible enough to sandbox arbitrary binaries.
by Sebastian Krahmer. Quoted from: http://seclists.org/oss-sec/2017/q1/20
I've kicked the tires a couple of times over the last year and
my feeling is that there remains a lot of low hanging exploitable fruit.
Although the devs have, with some encouragement, introduced macros to
permanently drop privs or drop euid 0 where possible there are still
places where that is not the case.
Setuid-root makes me sad, copy_file() worries me still and the ability
for a non-priv user to run any seccomp filter on anything feels like an
accident waiting to happen (assuming it cannot already be exploited).
by Martin Carpenter. Quoted from: http://seclists.org/oss-sec/2017/q1/25
As someone who has mentioned and recommended Firejail, I want to share a couple thoughts:
On one hand, Firejail is still in relatively early development, which means flaws are to be expected.
On the other hand, it is worrying that both of these security researchers have also raised serious concerns regarding Firejail's general design. It makes you wonder whether Firejail can still be a viable solution, even after these particular flaws are fixed.
What have I personally learned from this? Actually, there's nothing new here.
But there are certain "truths" of IT security that I tend do downplay, despite being aware of them. Probably because they are inconvienent truths:
1. using unaudited software is dangerous
2. audits are rare and if they do happen, they often produce scary results
3. setuid is dangerous
4. more security measures != more security
5. desktop security is in a dreadful state
Finally, I want to stress that the purpose of this thread is not to disparage Firejail. It's an awesome project, a lot of effort is being put into it. I hope it can be salvaged. But for the time being, I'm just not sure it's advisable to use it.
-
Using containers definitely creates less resource overhead than using virtual machines.
I personally prefer LXC, here's the Arch Wiki entry:
https://wiki.archlinux.org/index.php/Linux_Containers
Example of how to use OpenVPN in an LXC container:
https://wiki.archlinux.org/index.php/OpenVPN_in_Linux_containers
I cannot vouch for this solution as I have yet to try it myself, but it should give you some ideas on how to proceed.
Maybe I'll come up with a tutorial on this topic but I'm not sure I can find the time, so, no promises.
-
Good observations by nemoAnon, thank you!
Unrelated addition: For those that find it inconvenient to get the stunnel binary from the project's website (and manually keep it up to date!), I can recommend Termux. It's a nice alternative terminal emulator that allows you to install additional packages from their repositories with the apt package manager. Stunnel is among the available packages.
To some extent you're trading security for convenience as you won't be getting the stunnel binary directly from the stunnel project, but from the Termux repos.
I haven't actually tried using Termux yet, but I don't see any reason why it wouldn't work for our purpose. I might post new instructions if anyone needs help adapting them to Termux. Or maybe another friendly soul helps out
-
I actually wouldn't want MUC backlog to be disabled, but if Air staff agree with you, they would have to set history_size 0 in ejabberd's global config. There is no per-room configuration option AFAIK.
-
severed all ties with him. If you are looking on the Cryptostorm forums, any posts by "Pattern_Juggled" were Spink.
Thanks for pointing that out, because the Cryptostorm people certainly didn't:
Pattern_Juggled still holds the title Site Admin. Forums usually allow you to ban accounts or change at least their title, but apparently Cryptostorm don't think it's necessary to visibly distance themselves from their former admin, now convicted zoophilic, snitching drug-smuggler. Is that how you handle this correctly? Really?
in this case, just because some dude likes to screw animals doesn't mean a website is a government honeypot. You just can't stretch that far. Sorry.
Now you're the one stretching and reaching. Read my post, I don't claim CS to be a honeypot. I'm expressing how CS excude a terribly seedy atmosphere, underlined not only by Spink's prior involvement, but (more importantly even) also the ridiculous amount of gobbledegook and hot air. All of their material reads like it's written by 15-year olds.
For example, first, they don't even think about declaring their software license. Then, they pick a non-free license. Seriously? Who approaches software development like that?
If anything they are way too inattentive to their network.
Yeah, I think they are inattentive to a lot of things. Like proper, clear documentation. Is their forum section "how it works | guides, whitepapers, tech details [cryptostorm.org/howto]" the right place to look for whitepapers and tech details? Because all I see are connection howtos and a lot of hot air. Please, point me to whitepapers, audit reports, or at least server-side tech details. I'm happy that you're confident in their network but I can't find anything that would convince me. Their pompous forum posts are void of any technical information.
This is the "best" description of their token system I could dig up. They're rambling and rambling and spewing gobbledegook. Nothing of substance, no specification, no server-side code, nothing.
Whitepapers? Specs? Implementation details about their their "darknet"? Anything remotely like this or this?
Take off the tin foil.
I'm not wearing any: My disdain for CS is not fueled by paranoia, but lack of credible information that would support anything CS do. All there is to be found is evidence to the contrary: a poorly run project with a dubious past.
-
Oh, now this is delicious. Cryptostorm on trust and honeypots? Well they would know, that's for sure. Let's do some investigatory
journalismgoogling.1. Who's behind CryptoStorm?
CryptoStorm is a reincarnation of VPN service CryptoCloud, a subsidiary (or possibly close working partner) of Baneki Privacy Computing
2. Any interesting people @ Baneki? Let's ask Bloomberg:
Baneki Privacy Computing, Inc.
Mr. Douglas SpinkChief Technology Officer
source
3. Spink, Spink, I've heard that funny name before...Spink was arrested in 2005 after investigators pulled him over with a load of nearly 375 pounds of cocaine, valued at $34 million. He was given a lenient, three-year sentence because of his extensive cooperation with investigators.
source
4. But wait, there's more:
In April 2010, ex-cocaine smuggler Douglas Spink briefly dominated headlines when police raided his property in Whatcom County, Washington. Inside, they found a Welsh tourist making use of what the press has since described as an animal brothel, replete with tail-less mice covered in Vaseline. Overnight, Spink became the poster boy for the bizarre, brutal world of bestiality.
source
5. Fast forward to that 2014 CryptoStorm post:
Backstory. This is a big one, a very big one. Every tech team - every man or woman in the security tech world - has a backstory. Some really don't want to share those backstories, for any of a host of reasons.
If the people associated with the project do strange and organic things, that's a good sign.
People "associated with CryptoCloud/CryptoStorm" have been up to strange things indeed, wouldn't you say?
PostscriptMy post is, I hope that's obvious, polemical. I don't claim that Spink still pulls the strings over there (which would be difficult anyway because I think he is, once more, back in jail).
However, these are my serious points:
- Considering Baneki's "backstory", any serious person would run for the hills. Yet, CryptoStorm is still a thing. That should make you wonder about those who willingly associate themselves with such a tarnished project.
- CryptoStorm try to up their "street cred" by talking some "real shit" about "LEOs", "spooks", "paid shills", and who to trust. They want to teach you how to spot dodgy people. For me, that itself is the biggest warning sign of all. That's exactly how I would advertise my own honeypots.


SSH-Tunneled VPN on Stock Android
in General & Suggestions
Posted ...
ConnectBot's text output disappears sometimes but I think that's just a glitch, not a problem.
My Android and software versions are identical to yours. I haven't had much time to debug this, but here are my results:
Capricornus: fail (sshtunnel not established, local port 1412 stays closed)
Agena: success (I don't think I did anything differently)
Iskanda attempt #1: fail (sshtunnel not established, local port 1412 stays closed)
Iskanda attempt #2: fail (ConnectBot opens local port 1412, but no response from VPN server)
Iskanda attempt #3: fail (ssh connection refused (ECONNREFUSED)
I didn't have much time, but during my limited experiments using Linux instead of Android, I saw some similar problems. I doubt Android is the culprit here!
TL;DR + suggestions: