Search the Community
Showing results for tags 'opnsense'.
Found 12 results
-
This is an updated version of this guide. I hope it gets moved soon to the guides section. This guide should be complete now, but please note that the IPv6 port forwarding might not be 100% complete. Any advice is appreciated. Disclaimer In general, DO NOT TRUST ME! I'm not a security expert. I do not know what I'm doing here! This guide is based on: OPNsense 24.7.12_4-amd64 FreeBSD 14.1-RELEASE-p6 OpenSSL 3.0.15 Update: 2025-03-27: I updated to the latest version and this Guide is still correct OPNsense 25.1.4_1-amd64 FreeBSD 14.2-RELEASE-p1 OpenSSL 3.0.16 It should work in previous and future versions of OPNsense, but I can't guarantee it This guide is based on the official Instructions but required modification: https://docs.opnsense.org/manual/how-tos/wireguard-selective-routing.html it is also based on this guide. It's however not 100% correct, so I adjusted base on the official OPNsense guide and included the IPv6 setup. This is why I started a new guide instead of altering my previous one, inspired by the original Sj0r guide. 1. Preparation (not required if you access the firewall from LAN) Some advice here… Opening the WAN interface to allow administration is not good! I am doing this because the firewall sits in my private LAN, and I'm not doing any port forwarding on my main router ! If your firewall is connected directly to the internet, do not do this! Again, in general, DO NOT TRUST ME! I'm not a security expert. I do not know what I'm doing here! Now that you know it… 1.1 Deselect “Block private networks” and “Block bogon networks” in Interfaces → WAN. After doing so: hit save and “Apply changes”. 1.2 Select "Disable reply-to" in Firewall → Settings → Advanced. Hit save at the end. 1.3 Add incoming WAN rule to allow administration. Go to Firewall → Rules → WAN Add a TCP rule from "WAN net" to "This Firewall" on HTTPs. 2. Information gathering. We'll grab some info that we need to configure the WireGuard Tunnel. 2.1 Login to the AirVPN Website. 2.2 Got to VPN Devices. 2.3 Add a new device. 2.4 Go to Config Generator. 2.5 In "Choose your OS" select "router". 2.6 In "Choose protocols" select "WireGuard. 2.7 In "Choose your device/connection" Select the device you have created in 2.3 2.8 Select your country under "By Countries". I selected Germany this time. 2.9 Scroll way down and download your config. This is an example of a WireGuard config: (the keys and IP are random and will not work, use your own) [Interface] Address = 10.10.10.10/32 PrivateKey = X72xgdx23XDomnSXmcy#S4Jc#9Y5G*vU$wg^n499yn6 MTU = 1320 DNS = 10.128.0.1 [Peer] PublicKey = VTSQ77Uk4^&RY4h%S$#9h8PR2T&xyya&yPTtk6oD^m$ PresharedKey = b7&&7bntmCS5q%&4J*mSKBAUvV4XEqHerwscvbappXQ Endpoint = nl3.vpn.airdns.org:1637 AllowedIPs = 0.0.0.0/0 PersistentKeepalive = 15 3. Setup IPv6 base configuration on your LAN. We need to ensure that IPv6 communication is working on your LAN interface before we establish the VPN tunnel. Please note that I do not have an IPv6 address configured on my WAN interface to be distributed to LAN for security. Instead, I use a ULA address on the LAN. For those who do not know what ULA addresses are, these are the IPv6 equivalent to IPv4 private addresses like 10.x or 192.168.x. They are only routable on the LAN, and you will not be able to use them to reach an IPv6 destination on the internet. 3.1 WAN 3.1.1 Go to Interfaces → WAN The WAN interface looks like this: 3.2 LAN 3.2.1 Go to Interfaces → LAN The LAN interface looks like this in the upper section: Now we set up the IPv6 Configuration. 3.2.2 generate yourself a ULA address using this site: https://unique-local-ipv6.com/ 3.2.3 Enter the IPv6 network you have generated into the “IPv6 address” field and add “::1” at the end. Hit Save. 3.3 LAN DHCP IPv6 3.3.1 Go to Services → ISC DHCPv6 → LAN 3.3.2 In the Range section under from add your IPv6 network address from 3.2.2 and add a “::1000” to the end. In the to section, add your IPv6 network address again and this time add a “::2000” to the end. Hit Save at the bottom of the page. 3.4 Router advertisement 3.4.1 Go to Services → Router Advertisement → LAN 3.4.2 Set Router Advertisements to Managed Hit Save at the bottom of the page. 3.5 Test IPv6 configuration Now you should test if you can ping the OPNsense firewall IPv6 address from the LAN. 3.5.1 Connect a client to the LAN 3.5.2 On Linux or Windows, open a terminal and type ping -6 and the IPv6 from 3.2.1 ending with ::1 like “ping -6 fd2d:7173:d519::1”. This needs to be successful! If this is not successful, fix it! Only continue once this is successful!!! 4. WireGuard configuration. In the current Version of OPNsense you do not need to install the WireGuard plugin, this is already installed. 4.1 Peer configuration 4.1.1 in OPNsense go to VPN → WireGuard → Peers. 4.1.2 Create a peer with the following information: 4.1.3 Name: wg_airvpn_<country code>. Mine is called WG-AirVPN-DE 4.1.4 Public key: <PublicKey under heading [Peer] of your generated WG Config> 4.1.5 Pre-shared key <presharedKey under heading [Peer] of your generated WG Config> 4.1.6 Allowed IP's: 0.0.0.0/0 and ::/0 for IPv6 support 4.1.7 Endpoint Address: <Endpoint under heading [Peer] of your generated WG Config> 4.1.8 Endpoint port: 1637 (default port) 4.1.9 Keepalive interval: 15 (default interval) 4.2 Instance configuration 4.2.1 In OPNsense go to VPN → Wireguard → Settings → Instances 4.2.2 Create an instance with the following information: 4.2.3 Enable Advanced Mode. (upper left corner) 4.2.4 Name: <Endpoint Name i.e. WG-Inst-AirVPN-DE> 4.2.5 Private Key: <PrivateKey under heading [Interface] of your generated WG Config> 4.2.6 MTU: 1320 4.2.7 DNS servers <DNS Servers of your generated WG Config> 4.2.8 Tunnel Address: <Address including /32 under harding [Interface] of your generated WG Config> Please review the screenshot below. For IPv6 add the given address and instead of /128 chose /64 to reach the gateway for gateway monitoring. 4.2.9 Peers: <select peer that you created with step 4.1> 4.2.10 Disable routes: Enabled. 4.2.11 Gateway: 10.128.0.1 Hit Save 4.3 Enable WireGuard configuration Go to VPN → WireGuard → Instance and click on "Enable WireGuard" 4.4 Assign WireGuard Interface 4.4.1 in OPNsense go to Interfaces → Assignments 4.4.2 You'll find a “wg0(WireGuard - WG-Inst-AirVPN-DE)” (or similar) interface. 4.4.3 Type a Description, I've picked “[IntAirVPNDE]” and click Add. 4.5 Enable the Interface 4.5.1 Interfaces → Assignments → [IntAirVPNDE] 4.5.2 Enable: Enable the Interface. No further configuration required. Ensure the “Block private networks” and “Block bogon networks” options are not selected, as shown below. 4.6 Create a gateway - IPv4 4.6.1 In OPNsense go to System → Gateways → Configuration 4.6.2 Add a Gateway with the following information: 4.6.3 Name: GW-AirVPN-DE-v4 4.6.4 Interface: Select IntAirVPNDE as created in step 4.4 4.6.5 Address Family: IPv4 4.6.6 IP address: 10.128.0.1 4.6.7 Far Gateway: Enabled 4.6.8 Disable Gateway Monitoring: Disabled. 4.6.9 Monitor IP: 10.128.0.1 4.7 Create a gateway - IPv6 4.7.1 In OPNsense go to System → Gateways → Configuration 4.7.2 Add a Gateway with the following information: 4.7.3 Name: GW-AirVPN-DE-v6 4.7.4 Interface: Select IntAirVPNDE as created in step 4.4 4.7.5 Address Family: IPv6 4.7.6 IP address: fd7d:76ee:e68f:a993::1 (use the IPv6 DNS server from the WG Config) 4.7.7 Far Gateway: Enabled 4.7.8 Disable Gateway Monitoring: Disabled. 4.7.9 Monitor IP: fd7d:76ee:e68f:a993::1 (same as 4.7.6) 5. Alias Create at least one alias for the DNS configuration to prevent DNS leaks. You might want to create a separated alias for clients you want to run through the VPN, but as I do not need this, I skip it. The idea of how to set this up is similar. Please note for DNS leaks, there are multiple ways to prevent DNS leaks. I tested mine using ipleak.net and dnsleaktest.com. There is also a complete section about dealing with DNS leaks in the OPNSense guide. 5.1 Alias setup 5.1.1 Create the DNS alias. Firewall → Aliases 5.1.2 Click add 5.1.3 Enable: selected 5.1.4 Name: VPN_DNS_Server 5.1.5 Type: Host(s) 5.1.6 Content: 10.4.0.1, 10.128.0.1, 10.5.0.1, 10.7.0.1, fd7d:76ee:e68f:a993::1 5.2 Forward all DNS queries to the VPN DNS servers This might collide if you got clients on your LAN which should not go through the VPN, so this might need adjustments then. 5.2.1 Go to Firewall → NAT → Port Forward and click "+" to add a new rule. 5.2.2 Interface: LAN 5.2.3 TCP/IP Version: IPv4+IPv6 5.2.4 Protocol: TCP/UPD 5.2.5 Source: LAN net 5.2.6 Destination: Any 5.2.7 Destination port range: from: DNS to: DNS 5.2.8 Redirect target IP: VPN_DNS_Server (the Alias created in 5.1) 5.2.9 Redirect target port: DNS 5.2.10 Description: Redirect DNS requests from LAN to VPN DNS servers 5.2.11 NAT reflection: Disabled 5.2.12 Filter rule association: None 6. Outbound NAT 6.1 Switch to hybrid rules 6.1.1 Go to Firewall → NAT → Outbound 6.1.2 Select "Hybrid outbound NAT rule generation" 6.1.3 Click Save then apply the change 6.2 Add IPv4 outbound rule 6.2.1 Click the "+" to add a new rule 6.2.2 Interface: IntAirVPNDE (the interface created in 4.4) 6.2.3 TCP/IP Version: IPv4 6.2.4 Protocol: Any 6.2.5 Source address: LAN net 6.2.6 Source port: Any 6.2.7 Destination address: Any 6.2.8 Destination port: Any 6.2.9 Translation / target: Interface address 6.2.10 Pool Options: Default 6.2.11 Description: LAN to AirVPN-DE IPv4 6.3 Add IPv6 outbound rule 6.3.1 Click the "+" to add a new rule 6.3.2 Interface: IntAirVPNDE (the interface created in 4.4) 6.3.3 TCP/IP Version: IPv6 6.3.4 Protocol: Any 6.3.5 Source address: LAN net 6.3.6 Source port: Any 6.3.7 Destination address: Any 6.3.8 Destination port: Any 6.3.9 Translation / target: Interface address 6.3.10 Pool Options: Default 6.3.11 Description: LAN to AirVPN-DE IPv6 7. LAN to VPN firewall rule With this rule, we point all LAN clients through the VPN. 7.1 IPv4 LAN to VPN rule 7.1.1 Go to Firewall → Rules → LAN and click on the "+" to add a new rule 7.1.2 Action: Pass 7.1.3 Quick: Apply the action immediately on match. (make sure it's enabled, as shown in the screenshot) 7.1.4 Interface: LAN 7.1.5 Direction: In 7.1.6 TCP/IP Version: IPv4 7.1.7 Protocol: Any 7.1.8 Source: LAN net 7.1.9 Destination: Any 7.1.10 Description: LAN to VPN IPv4 7.1.11 Gateway: GW-AirVPNDE-v4 - 10.128.0.1 (Created in 4.6) 7.2 IPv6 LAN to VPN rule 7.2.1 Go to Firewall → Rules → LAN and click on the "+" to add a new rule 7.2.2 Action: Pass 7.2.3 Quick: Apply the action immediately on match. (make sure it's enabled, as shown in the screenshot) 7.2.4 Interface: LAN 7.2.5 Direction: In 7.2.6 TCP/IP Version: IPv6 7.2.7 Protocol: Any 7.2.8 Source: LAN net 7.2.9 Destination: Any 7.2.10 Description: LAN to VPN IPv6 7.2.11 Gateway: GW-AirVPNDE-v6 - fd7d:76ee:e68f:a993::1 (Created in 4.7) 7.3 Block all other traffic rule This ensures that all other traffic is blocked. It's not really needed but gives me a better feeling. It will collide if you got clients on your LAN which do not run through the VPN. 7.3.1 Go to Firewall → Rules → LAN and click on the “+” to add a new rule 7.3.2 Action: Block 7.3.3 Quick: Apply the action immediately on match. (make sure it's enabled, as shown in the screenshot) 7.3.4 Interface: LAN 7.3.5 Direction: In 7.3.6 TCP/IP Version: IPv4 + IPv6 7.3.7 Protocol: Any 7.3.8 Source: LAN net 7.3.9 Destination: Any 7.3.10 Description: Block all other traffic LAN to VPN IPv6 7.3.11 Gateway: default Make sure these new rules are on top of the LAN firewall rules. If they are not, traffic might go through other rules and not through the VPN. 8. Port Forwarding for applications like BitTorrent If you want to make one or more clients reachable from the internet, like you need to do when you are doing file-sharing, follow the below to make it work for Pv4 and IPv6. Please note that this is confirmed to working with IPv4, but I'm not 100% sure how to make this fully work with IPv6. You can use an IPv6 port testing tool to confirm that the port is indeed open, but not many IPv6 clients really manage to connect to me. There must be something else I'm missing here. Please help me to get this right so we can complete this guide. So far, this functionality is limited. Ensure that you got the Port Forwarding properly configured in the AirVPN Member section. You need a port from the :1 pool and this port needs to be forwarded to the device configured in 2.3 8.1 Setup IPv4 Firewall rule for incoming connections 8.1.1 Go to Firewall → Rules → IntAirVPNDE 8.1.2 Action: Pass 8.1.3 Quick: Apply the action immediately on match. (make sure it's enabled, as shown in the screenshot) 8.1.4 Interface: IntAirVPNDE 8.1.5 Direction: In 8.1.6 TCP/IP Version: IPv4 8.1.7 Protocol: TCP/UDP 8.1.8 Destination: *the IPv4 address of your client*/32 8.1.9 Destination port range: *your port* 8.1.10 Description: YourRule IPv4 8.1.11 Advanced features: Enabled 8.1.12 reply-to: GW-AirVPN-DE-v4 10.128.0.1 8.2 Setup IPv6 Firewall rule for incoming connections This is equal to the 8.1 setup. Differences are marked bold: 8.2.1 Go to Firewall → Rules → IntAirVPNDE 8.2.2 Action: Pass 8.2.3 Quick: Apply the action immediately on match. (make sure it's enabled, as shown in the screenshot) 8.2.4 Interface: IntAirVPNDE 8.2.5 Direction: In 8.2.6 TCP/IP Version: IPv6 8.2.7 Protocol: TCP/UDP 8.2.8 Destination: *the IPv6 address of your client*/128 8.2.9 Destination port range: *your port* 8.2.10 Description: YourRule IPv6 8.2.11 Advanced features: Enabled 8.2.12 reply-to: GW-AirVPN-DE-v6 fd7d:76ee:e68f:a993::1 8.3 Port Forwarding IPv4 8.3.1 Go to Firewall → NAT → Port Forward, click “*” to create a new rule 8.3.2 Interface: IntAirVPNDE 8.3.3 TCP/IP Version: IPv4 8.3.4 Protocol: TCP/UDP 8.3.5 Destination: This Firewall 8.3.6 Destination port range: The port range from 8.1.9 and the Member section 8.3.7 Redirect target IP: Same as 8.1.8 8.3.8 Redirect target port: same as 8.3.6 8.3.9 Description: YourPortForward 8.3.10 NAT reflection: Disabled 8.3.11 Filter rule association: None 8.4 Port Forwarding IPv6 same as 8.3 just with the IPv6 adjustments 8.4.1 Go to Firewall → NAT → Port Forward, click “*” to create a new rule 8.4.2 Interface: IntAirVPNDE 8.4.3 TCP/IP Version: IPv6 8.4.4 Protocol: TCP/UDP 8.4.5 Destination: This Firewall 8.4.6 Destination port range: The port range from 8.2.9 and the Member section 8.4.7 Redirect target IP: Same as 8.2.8 8.4.8 Redirect target port: same as 8.4.6 8.4.9 Description: YourPortForward 8.4.10 NAT reflection: Disabled 8.4.11 Filter rule association: None That should be it. Please tell me if you got any issue.
-
SUPERSEDED BY: THIS THREAD WILL BE REMOVED - SUPERSEDED BY This HOWTO describes how to connect to AirVPN with a Wireguard VPN tunnel from OPNsense. This is the first draft of this howto, i might add (more) screenshots later on. Version: 0.1 Date: 20231029 What we are going to achieve We'll create a single Wireguard VPN Tunnel, IPv4 Only. Traffic to the tunnel will be NATted Requirements OPNsense firewall is up-and-running and updated. This howto is based on version 23.7.7_1 You have basic knowledge on using OPNsense i.e. firewall rules, NAT, routing, gateways and aliases. AirVPN Premium Access Step 1. Information gathering We'll grab some info that we need to configure the Wireguard Tunnel. Go to the Client Area. Got to VPN Devices. Add a device or edit your existing device. Note your Public Key and IPv4 under the heading "Wireguard" Go back to the Client Aerea. Go to Config Generator Select "router" under "Choose your OS" Select "Wireguard under "Choose protocols" Select your country under "By Countries". I selected Netherlands Scroll way down and download your config. This is an example of a Wireguard config: (the keys and IP are random and will not work, use your own) [Interface] Address = 10.45.95.123/32 PrivateKey = X72xgdx23XDomnSXmcy#S4Jc#9Y5G*vU$wg^n499yn6 MTU = 1320 DNS = 10.128.0.1 [Peer] PublicKey = VTSQ77Uk4^&RY4h%S$#9h8PR2T&xyya&yPTtk6oD^m$ PresharedKey = b7&&7bntmCS5q%&4J*mSKBAUvV4XEqHerwscvbappXQ Endpoint = nl3.vpn.airdns.org:1637 AllowedIPs = 0.0.0.0/0 PersistentKeepalive = 15 Step 2. Create the Tunnel configuration Peer configuration: in OPNsense go to VPN|Wireguard|Settings|Peers. Create a peer with the following information: Name: wg_airvpn_<country code>. mine is called wg_airvpn_nl Public key: <PublicKey under heading [Peer] of your generated WG Config> Pre-shared key <presharedKey under heading [Peer] of your generated WG Config> Allowed IP's: 0.0.0.0/0 Endpoint Address: <Endpoint under heading [Peer] of your generated WG Config> Endpoint port: 1637 (default port) Keepalive interval: 15 (default interval) Instance configuration: in OPNsense go to VPN|Wireguard|Settings|Instances Create an instance with the following information: Enable Advanced Mode. Name: <Endpoint Name i.e. nl.vpn.airdns.org> Public Key: <Public Key as noted with step 1.4> Private Key: <PrivateKey under heading [Interface] of your generated WG Config> Listen Port: 1637 MTU: 1320 Tunnel Address: <Address including /32 under harding [Interface] of your generated WG Config> Peers: <select peer that you created with step 2.2> Disable routes: Enabled. Step 3. Make an exception on your WAN interface in OPNsense go to Firewall|Rules Select your WAN interface, mine is called WAN_PPPOE Create a Pass rule for IPv4/UDP port 1647 to your WAN-address. Step 4. Assign Wireguard Interface in OPNsense go to Interfaces|Assignments You'll find a "wg1(Wireguard - nl.vpn.airdns.org)" (or similiar) interface. bind it to an interface with a name of your choice. mine is called WAN_WG1 as is is the first site-to-site Wireguard tunnel on my WAN interface. Step 5. Create a gateway. Remember we disabled the routes for the WG instance configuration? Because of that we need to create a gateway. In OPNsense go to System|Gateways|Single Add a Gateway with the following information: Name: WAN_WG_GW Description: Interface WAN_WG1 Gateway Interface: Select WAN_WG1 as created in step 4. Address Family: IPv4 IP address: Dynamic (leave empty) Far Gateway: Enabled (this i am not sure of but for now i'm happy it works) Disable Gateway Monitoring: enabled Step 6. Aliases We set up some aliases. This will make it more easy to redirect some hosts or networks to the Wireguard tunnel. in OPNsense, go to Firewall|Aliases Create host entries for the specific hosts you'll redirect Create network entries for the specific network(s) you'll redirect. Create a Network Group Entry with the host and network entries to group them together. My alias is called networkgroup_wireguard Step 7. Create Outbound NAT for Wireguard. (In my setup, i use Manual Outbound Rule Generation because i like to have control) In OPNsense go to Firewall|NAT|Outbound Create a new Outbound NAT rule with the following information: Interface: WAN_WG1 TCP/IP version: IPv4 Protocol: Any Source Address: <alias networkgroup_wireguard from step 6> Translation /target WAN_WG1 address Description: Wireguard VPN Outbound NAT rule Step 8. Create Outbound Redirect rule. In this example we create 2 rules on our LAN interface, one for redirecting to WG, the other to prevent leaks. In OPNsense go to Firewall|Rules Select your LAN interface add an outbound Pass rule: Action: Pass Source: Networkgroup_wireguard Destination: Any (in my case i use an inverted network group called networkgroup_local where all my local vlans are grouped together) Gateway: WAN_WG1_GW (the gateway you created in step 5.) Add an outbound block rule below that: Action: Block Source: Networkgroup_wireguard Destination: Any Gateway: default Your WG VPN tunnel should now work. Test with https://ipleak.net The following steps are more advanced and i'm still finetuning/experimenting with the settings. your experience may vary. Step 9. Prevent VPN leakage I'm new to OPNsense and i am not sure what the default setting is, but from my pfSense experience i know the following setting is important when you want to make sure your VPN does not leak when for instance the tunnel is down. In OPNsense go to Firewall|Settings|Advanced Under "Gateway Monitoring" enable "Skip Rules when gateway is down" Step 10. MTU/MSS optimization For now i have set thte MTU according to the default setting of AirVPN. I want it to be higher but for now i'm just happy it works. My settings are as follows: In the properties of the WAN_WG1 interface i set the MTU to 1320 and the MSS to 1280. I created a normalize rule (Firewall|Settings|Normalization) with the following settings. this should enable me to clamp the MSS to 1280 for the wireguard group but leave the MSS to the desired setting (1452) as defined on my LAN interface for the rest of the hosts on my LAN; Interface: LAN Direction, Protocol: Any Source: networkgroup_wireguard Max MSS: 1280
-
How to prevent VPN leakage with OPNsense In this topic I want to share with you what i've learned regarding the prevention of VPN leakage using OPNsense. This guide assumes you're familiar with OPNsense and you have already a working configuration. What this howto is about This howto results in the following; 1. DNS requests are forced to go to the Unbound Service on OPNsense and will be TLS encrypted to prevent your ISP logging your DNS traffic. 2. Traffic destined for your AIRVPN tunnel is tagged and any leakage on your normal WAN blocks that traffic. 3. Traffic destined to your WAN interface is kept local. About my configuration I run OPNSense as a firewall and NAT router. I have multiple VLANs for specific purposes (LAN, DMZ, IOT, Management, GUEST and dedicated VPN segments). I run multiple OpenVPN instances to several countries, some are set up load balanced or failover with gateway groups. Some of my VM's or containers reside in a VPN network and this is in my opinion the best way to ensure traffic is enforced through VPN. This is one of the reasons i make heavily use of FLOATing rules to minimize the amount of rules needed (which cost CPU time). Most LAN hosts are normally routed through WAN but specific ones i route through VPN by grouping them in aliases. What is VPN leakage? All AirVPN configurations are of a full tunnel type. This means that all traffic is supposed to be routed through that tunnel to the other side. But sometimes this is not the case for all types of traffic. For instance, most VPN clients support local traffic alongside the tunnel, or you have a custom VPN setup on your router to direct some, but not all traffic to your VPN tunnel. VPN or firewall misconfigurations can lead to traffic leaking outside of the tunnel. Some examples are: 1. The tunnel is down on your router, your endpoint is unaware and all traffic is suddenly unencrypted 2. You have a running VPN tunnel but allow local DNS and all your DNS resolves are being sent in clear text outside the tunnel Endpoint and application configuration (out of scope of this topic) can also leak information, be aware of the following; 3. Dual stack machines and IPv6 can leak information about your location. (use ipv4 and NAT exclusively) 4. Browser misconfigurations can also leak information of your whereabouts. (webrtc, locale settings) Preventing DNS leakage with Port NAT and Unbound Unbound configuration Where i live ISPs are obligated to log traffic. To prevent this i have setup Unbound to use DNS-over-TLS (DoT) to make sure my resolves are encrypted. I don't route my DNS through VPN as i need it to work when my VPNs are down. These are the changes i made to the configuration to Unbound. 1. in Unbound DNS|General|Advanced Mode staat de "outgoing network interfaces" op WAN_PPOE 2. In Unbound|DNS over TLS i have configured several DoT forwarders An example for dns.adguard.com: I do have configured quad9 and cloudflare but only for fallback as i don't trust them for privacy reasons. Also, consider the following; When you have configured your own local zone ie. myhouse.com set the "Local Zone Type" to "static" in the general settings of unbound. I think the default is "transparent" which results in forwarding unknown hosts to outside DNS servers and you should not want that to happen. PortNAT configuration I have several hosts with docker containers which have hardcoded DNS configurations to google, cloudflare etc. I make sure they resolve to my unbound through portnat; 1. Create a network group alias "networkgroup_local". In here, you put all your local network segments like __lan_network and all __opt*_networks; 2. Create a port NAT rule like this; This results in all traffic from several local network segments, destined to any host NOT local (see destination/invert) to port 53 being rerouted to my LAN interface. I have "Firewall Rule Assocation" turned off as i like to have full control over my own firewall rules. 3. Create a floating rule like this; This portNAT and rule combination results in the following; 1. All traffic with destination other than local segments to port 53 will be portNATted to my LAN interface where Unbound is servicing DNS. 2. one floating rule allows traffic to port 53 flow from their respective VLANS to my LAN interface to port 53. I also block DOH as again, several docker containers are hard-coded to external DNS-over-HTTPS servers. To prevent this from happening i subscribe to a blocklist and block traffic. This is just me being paranoid and outside the scope of this topic ;-) You can make use of external lists by creating an alias which you can use in firewall rules like this; The list i use is: https://raw.githubusercontent.com/dibdot/DoH-IP-blocklists/master/doh-ipv4.txt Use this alias to create an interface or floating rule that blocks traffic destined to the alias on port 443. Preventing traffic leakage with tagging OPNsense has a feature where you can tag traffic and pass or block traffic based on these tags. With this we can block traffic on the WAN interface that should've been routed through the VPN tunnel. Tagging of Outbound NAT traffic Outbound NAT rules for your tunnel traffic MUST be above any NAT rules for normal WAN! Find your AIRVPN outbound NAT rule and make the following adjustment; This example will NAT any traffic to my WAN_AIRVPN1 interface coming from my VPN VLAN destined to any host not local and tags it with "NO_VPN_LEAK" Next, change the matching outbound firewall rule; This rule, added to my VPN VLAN routes all traffic through VPN (with the gateway setting) and tags it with "NO_VPN_LEAK" Block tagged traffic on the WAN interface Next, we block outbound traffic tagged with "NO_VPN_LEAK" on the WAN interface. Create a FLOATING rule. Make sure this is high up the list: This rule is active on the normal WAN interface and screens outbound traffic matching "NO_VPN_LEAK tags and blocks it. Prevent WAN Callback leakage WAN Callback leakage can assist ISP's or three letter agencies in detecting which outbound VPN IP address you're using when you access your own services you may have active on your WAN interface. I have several web services running on OPNsense behind HAProxy. Traffic from hosts behind VPN should route locally. For this i have created an outbound NAT like this; (make sure this is the TOP NAT rule) Add a FLOATing firewalle rule to match this traffic; Also, make sure this rule is somewhere at the top of your FLOATing rule list. I like to make use of floating rules as i can match traffic from several interfaces with one rule but it can also be an interface rule if you have only one LAN interface.
-
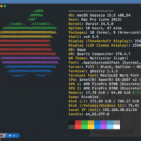
Hi everyone, I did follow the guide posted here: [link] as good as I could. I ran ins some minor issues, but that should not be the root cause really. Furthermore, I documented my setup and posted a reply to the original author this time with screenshots so it could be used as help for everyone, like me, who is struggling with this. So as said, basically it's not working for me. I can't access anything from LAN. To me (noob) it looks like the tunnel is up, but I can't reach it. Looking at the gateway shows "defunct". To me, this does not sound good. In the WireGuard log, I get the following when I disable WireGuard and enable it again: I am a complete starter on OPNsense and WireGuard, before I was using pfSense and OpenVPN, but this is a bit different. So any help is much appreciated.
-
So I am running opnsense and for some reason can't get airvpn to tell me I have properly opened my port for qbitorrent. I've successfully done so with mullvad in the past, but that was also with another torrent program I think. I'm using the same port as recommended for qbitorrent though opnsense into airvpn. The only hiccup might be that I have my torrent client on a separate vlan. I seem to recall opnsense having an issue with the rules for port forwarding not properly generating when adding a port forward to a non-lan interface. Anyone know anything? Thanks!
-
Hi, I'm trying to connect my newly OpenSense installed device to AirVPN. I'm stuck with configuring the connection properly. First, I tried entering all lines manually, where possible. My generated ovpn file is as follows: client dev tun remote nl4.vpn.airdns.org 41185 resolv-retry infinite nobind persist-key persist-tun auth-nocache verb 3 remote-cert-tls server comp-lzo no data-ciphers CHACHA20-POLY1305:AES-256-GCM:AES-256-CBC:AES-192-GCM:AES-192-CBC:AES-128-GCM:AES-128-CBC data-ciphers-fallback AES-256-CBC proto tcp auth SHA512 <ca> -----BEGIN CERTIFICATE----- AAAAAAA -----END CERTIFICATE----- </ca> <cert> -----BEGIN CERTIFICATE----- BBBBBBB -----END CERTIFICATE----- </cert> <key> -----BEGIN PRIVATE KEY----- CCCCCCC -----END PRIVATE KEY----- </key> <tls-crypt> -----BEGIN OpenVPN Static key V1----- DDDDDDD -----END OpenVPN Static key V1----- </tls-crypt> I couldn't connect to AirVPN properly. Tried removing nobind as there is an incompatibility with local, which I didn't know exactly. 2022-11-22T10:06:35 Warning openvpn Use --help for more information. 2022-11-22T10:06:35 Error openvpn Options error: --local and --nobind don't make sense when used together 2022-11-22T10:06:24 Warning openvpn Use --help for more information. 2022-11-22T10:06:24 Error openvpn Options error: --local and --nobind don't make sense when used together 2022-11-22T09:38:15 Warning openvpn Use --help for more information. 2022-11-22T09:38:15 Error openvpn Options error: --local and --nobind don't make sense when used together 2022-11-22T09:38:05 Warning openvpn Use --help for more information. 2022-11-22T09:38:05 Error openvpn Options error: --local and --nobind don't make sense when used together 2022-11-22T09:37:53 Warning openvpn Use --help for more information. 2022-11-22T09:37:53 Error openvpn Options error: --local and --nobind don't make sense when used together 2022-11-22T09:35:47 Notice openvpn Exiting due to fatal error 2022-11-22T09:35:47 Error openvpn Error: private key password verification failed 2022-11-22T09:35:47 Warning openvpn Cannot load private key file /var/etc/openvpn/client1.key 2022-11-22T09:35:47 Warning openvpn OpenSSL: error:0B080074:x509 certificate routines:X509_check_private_key:key values mismatch 2022-11-22T09:35:47 Warning openvpn NOTE: the current --script-security setting may allow this configuration to call user-defined scripts 2022-11-22T09:35:47 Notice openvpn MANAGEMENT: unix domain socket listening on /var/etc/openvpn/client1.sock 2022-11-22T09:35:47 Notice openvpn library versions: OpenSSL 1.1.1s 1 Nov 2022, LZO 2.10 2022-11-22T09:35:47 Notice openvpn OpenVPN 2.5.8 amd64-portbld-freebsd13.1 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Nov 16 2022 2022-11-22T09:35:47 Warning openvpn WARNING: file '/var/etc/openvpn/client1.up' is group or others accessible Advanced settings contents: nobind persist-key persist-tun auth-nocache verb 3 remote-cert-tls server comp-lzo no data-ciphers CHACHA20-POLY1305:AES-256-GCM:AES-256-CBC:AES-192-GCM:AES-192-CBC:AES-128-GCM:AES-128-CBC data-ciphers-fallback AES-256-CBC proto tcp auth SHA512 While removing some lines, nobind persist-key persist-tun auth-nocache verb 3 remote-cert-tls server the result is similar. After removing nobind: 2022-11-22T10:51:11 Notice openvpn Exiting due to fatal error 2022-11-22T10:51:11 Error openvpn Error: private key password verification failed 2022-11-22T10:51:11 Warning openvpn Cannot load private key file /var/etc/openvpn/client1.key 2022-11-22T10:51:11 Warning openvpn OpenSSL: error:0B080074:x509 certificate routines:X509_check_private_key:key values mismatch 2022-11-22T10:51:11 Warning openvpn NOTE: the current --script-security setting may allow this configuration to call user-defined scripts 2022-11-22T10:51:11 Notice openvpn MANAGEMENT: unix domain socket listening on /var/etc/openvpn/client1.sock 2022-11-22T10:51:11 Notice openvpn library versions: OpenSSL 1.1.1s 1 Nov 2022, LZO 2.10 2022-11-22T10:51:11 Notice openvpn OpenVPN 2.5.8 amd64-portbld-freebsd13.1 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Nov 16 2022 2022-11-22T10:51:11 Warning openvpn WARNING: file '/var/etc/openvpn/client1.up' is group or others accessible Tried several things here, without luck: - Using IP address instead of host. - Disabling TLS auth and putting all the lines into Advanced section. Can you help?
-
I got Airvpn wireguard working on OPNsense using this link. It works fine except I can't access the sites in the title. They time out. I imagine there are others but these are the only three I have found so far after approximately one week of usage. I have tried different servers and for duckduckgo I tried the ip address but no results. I am currently using the northamerican server. I have tried canada and a particular Toronto server with the same result. Any help or suggestions would be much appreciated. Thanks. Bill Dika SOLVED: I got this working using a detailed rule for MSS clamping by setting the it to 1300. Firewall --> Settings --> Normalization --> Disable Interface Scrub --> Create Detailed Settings Rule --> Set max mss to 1300.
-
I have the following set up: ISP Modem --> Protectli(OPNsense-AirVPN Wireguard) --> Netgear R7000 Access Point(Fresh Tomato) --> My Lan (of which there is one hardwired computer running an apache webserver) I have a nextcloud instance running on the apache webserver. I want to be able to access the nextcloud instance remotely. OPNsense has an option available for various Dynamic DNS (DDNS) services. I had the DDNS service for duckdns working and I could access my nextcloud server remotely before I changed to AirVPN as my VPN (I was using Mulvad). Now I want to accomplish the same thing with AirVPN without using duckdns but by using AirVPN's DDNS. The problem is that I cannot even get started. When I go to the AirVPN ports page, click on "Request a new port" and then click on "Test open". The connection times out (110) for TCP but seems to work for UDP (at least I don't see any error for UDP). This happens regardless of whether I leave the local port empty, fill in the local port with the same port number as the assigned port or use port 80 for the local port. Also it doesn't matter if I fill in the xxxx.airdns,org or not. "CanYouSeeMe" reports the ports as closed for for all my attempts. I have tried this on my local internet as well as on my cell phone data plan without any difference. I feel like I am missing something fundamental but have no idea what it is. Any help would be much appreciated. Thanks. bdika
-
Hi I am trying to connect to AirVPN from an OPNSense Firewall. I have tried many different configs and the status of my openvpn tunnel is always "connecting". The log file shows no errors, there is just a entry state all and client disconnected. Is there any working guide for the current OPNSense version. I do not have any problems to connect to AirVPN from any Windows Client in my network. I looked at my firewall log and did a tcpdump, but i can not see any incoming traffic. I do not have a private ip address, because i use a 5G router. could this be the problem? why is it working on other clients (Android, Windows Workstation)? thank you for your help
-
Hi, I´ve tried to configure Airvpn on my Firewall with this tutorial (https://airvpn.org/topic/17444-how-to-set-up-pfsense-23-for-airvpn/). Unfortunately the tutorial is written for pfsense and there are to many differences in the web gui to use it with OPNsense. So I couldn´t get it running with this tutorial. I want to route my whole traffic through Airvpn. Does anybody has a hint or an how to do? Please consider that Im a beginner at opnsense, so the options and steps are not self-explanatory to me. I also speak german
-
I am trying to get airvpn running on my new opnsense install but no success so far. This is the guide i followed and quite some options in the setup menu are not in the guide. Maybe because this was written for an older opnsense version. I did exactly what was in the guide and nothing more. Maybe the point is that i`m behind a non-bridged modemrouter? I forwarded port 443 udp and tcp to the opnsense wan (192.168.0.20). Everything after the modemrouter is 192.168.0.x and the lan behind the opnsense system gets 192.168.1.x The guide says, at step 5 the status should be up. This is the log i get: Feb 25 02:40:45 openvpn[86654]: MANAGEMENT: Client disconnected Feb 25 02:40:45 openvpn[86654]: MANAGEMENT: CMD 'state 1' Feb 25 02:40:45 openvpn[86654]: MANAGEMENT: Client connected from /var/etc/openvpn/client1.sock Feb 25 02:40:15 openvpn[86654]: MANAGEMENT: Client disconnected Feb 25 02:40:15 openvpn[86654]: MANAGEMENT: CMD 'state 1' Feb 25 02:40:15 openvpn[86654]: MANAGEMENT: Client connected from /var/etc/openvpn/client1.sock Feb 25 02:40:14 openvpn[86654]: VERIFY OK: depth=0, C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=server, emailAddress=info@airvpn.org Feb 25 02:40:14 openvpn[86654]: VERIFY EKU OK Feb 25 02:40:14 openvpn[86654]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication Feb 25 02:40:14 openvpn[86654]: Validating certificate extended key usage Feb 25 02:40:14 openvpn[86654]: VERIFY KU OK Feb 25 02:40:14 openvpn[86654]: VERIFY OK: depth=1, C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=airvpn.org CA, emailAddress=info@airvpn.org Feb 25 02:40:14 openvpn[86654]: TLS: Initial packet from [AF_INET]194.187.251.154:443, sid=c0b00d21 453258cb Feb 25 02:40:14 openvpn[86654]: UDP link remote: [AF_INET]194.187.251.154:443 Feb 25 02:40:14 openvpn[86654]: UDP link local (bound): [AF_INET]192.168.0.20:0 Feb 25 02:40:14 openvpn[86654]: Socket Buffers: R=[42080->42080] S=[57344->57344] Feb 25 02:40:14 openvpn[86654]: TCP/UDP: Preserving recently used remote address: [AF_INET]194.187.251.154:443 Feb 25 02:40:14 openvpn[86654]: Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication Feb 25 02:40:14 openvpn[86654]: Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication Feb 25 02:40:14 openvpn[86654]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Feb 25 02:40:14 openvpn[86654]: MANAGEMENT: unix domain socket listening on /var/etc/openvpn/client1.sock Feb 25 02:40:14 openvpn[86616]: library versions: OpenSSL 1.0.2n 7 Dec 2017, LZO 2.10 Feb 25 02:40:14 openvpn[86616]: OpenVPN 2.4.4 amd64-portbld-freebsd11.1 [sSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Jan 22 2018 Feb 25 02:38:49 openvpn[68218]: SIGTERM[hard,] received, process exiting Feb 25 02:38:49 openvpn[68218]: event_wait : Interrupted system call (code=4) Feb 25 02:38:47 openvpn[68218]: MANAGEMENT: Client disconnected Feb 25 02:38:47 openvpn[68218]: MANAGEMENT: CMD 'state 1' Feb 25 02:38:47 openvpn[68218]: MANAGEMENT: Client connected from /var/etc/openvpn/client1.sock Feb 25 02:37:59 openvpn[68218]: VERIFY OK: depth=0, C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=server, emailAddress=info@airvpn.org Feb 25 02:37:59 openvpn[68218]: VERIFY EKU OK Feb 25 02:37:59 openvpn[68218]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication Feb 25 02:37:59 openvpn[68218]: Validating certificate extended key usage Feb 25 02:37:59 openvpn[68218]: VERIFY KU OK Feb 25 02:37:59 openvpn[68218]: VERIFY OK: depth=1, C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=airvpn.org CA, emailAddress=info@airvpn.org Feb 25 02:37:59 openvpn[68218]: TLS: Initial packet from [AF_INET]194.187.251.154:443, sid=37214535 dc5a7495 Feb 25 02:37:59 openvpn[68218]: UDP link remote: [AF_INET]194.187.251.154:443 Feb 25 02:37:59 openvpn[68218]: UDP link local (bound): [AF_INET]192.168.0.20:0 Feb 25 02:37:59 openvpn[68218]: Socket Buffers: R=[42080->42080] S=[57344->57344] Feb 25 02:37:59 openvpn[68218]: TCP/UDP: Preserving recently used remote address: [AF_INET]194.187.251.154:443 Feb 25 02:37:59 openvpn[68218]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Feb 25 02:37:49 openvpn[68218]: Restart pause, 10 second(s) Feb 25 02:37:49 openvpn[68218]: SIGUSR1[soft,tls-error] received, process restarting Feb 25 02:37:49 openvpn[68218]: TLS Error: TLS handshake failed Feb 25 02:37:49 openvpn[68218]: TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) Feb 25 02:37:35 openvpn[68218]: MANAGEMENT: Client disconnected Feb 25 02:37:35 openvpn[68218]: MANAGEMENT: CMD 'state 1' Feb 25 02:37:35 openvpn[68218]: MANAGEMENT: Client connected from /var/etc/openvpn/client1.sock Feb 25 02:36:49 openvpn[68218]: VERIFY OK: depth=0, C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=server, emailAddress=info@airvpn.org Feb 25 02:36:49 openvpn[68218]: VERIFY EKU OK Feb 25 02:36:49 openvpn[68218]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication Little later: Feb 25 03:00:12 openvpn[86654]: MANAGEMENT: Client disconnected Feb 25 03:00:12 openvpn[86654]: MANAGEMENT: CMD 'state 1' Feb 25 03:00:12 openvpn[86654]: MANAGEMENT: Client connected from /var/etc/openvpn/client1.sock Feb 25 02:55:44 openvpn[86654]: Restart pause, 300 second(s) Feb 25 02:55:44 openvpn[86654]: SIGUSR1[soft,ping-restart] received, process restarting Feb 25 02:55:44 openvpn[86654]: [server] Inactivity timeout (--ping-restart), restarting Feb 25 02:54:44 openvpn[86654]: VERIFY OK: depth=0, C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=server, emailAddress=info@airvpn.org Feb 25 02:54:44 openvpn[86654]: VERIFY EKU OK Feb 25 02:54:44 openvpn[86654]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication Feb 25 02:54:44 openvpn[86654]: Validating certificate extended key usage Feb 25 02:54:44 openvpn[86654]: VERIFY KU OK Feb 25 02:54:44 openvpn[86654]: VERIFY OK: depth=1, C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=airvpn.org CA, emailAddress=info@airvpn.org Feb 25 02:54:44 openvpn[86654]: TLS: Initial packet from [AF_INET]194.187.251.154:443, sid=263f3cd0 cd08c14b Feb 25 02:54:44 openvpn[86654]: UDP link remote: [AF_INET]194.187.251.154:443 Feb 25 02:54:44 openvpn[86654]: UDP link local (bound): [AF_INET]192.168.0.20:0 Feb 25 02:54:44 openvpn[86654]: Socket Buffers: R=[42080->42080] S=[57344->57344] Feb 25 02:54:44 openvpn[86654]: TCP/UDP: Preserving recently used remote address: [AF_INET]194.187.251.154:443 Feb 25 02:54:44 openvpn[86654]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Feb 25 02:52:04 openvpn[86654]: Restart pause, 160 second(s) Feb 25 02:52:04 openvpn[86654]: SIGUSR1[soft,ping-restart] received, process restarting Feb 25 02:52:04 openvpn[86654]: [server] Inactivity timeout (--ping-restart), restarting Feb 25 02:51:04 openvpn[86654]: VERIFY OK: depth=0, C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=server, emailAddress=info@airvpn.org Feb 25 02:51:04 openvpn[86654]: VERIFY EKU OK Feb 25 02:51:04 openvpn[86654]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication Feb 25 02:51:04 openvpn[86654]: Validating certificate extended key usage Feb 25 02:51:04 openvpn[86654]: VERIFY KU OK Feb 25 02:51:04 openvpn[86654]: VERIFY OK: depth=1, C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=airvpn.org CA, emailAddress=info@airvpn.org Feb 25 02:51:04 openvpn[86654]: TLS: Initial packet from [AF_INET]194.187.251.154:443, sid=c6a2dfeb 08c736d9 Feb 25 02:51:04 openvpn[86654]: UDP link remote: [AF_INET]194.187.251.154:443 Feb 25 02:51:04 openvpn[86654]: UDP link local (bound): [AF_INET]192.168.0.20:0 Feb 25 02:51:04 openvpn[86654]: Socket Buffers: R=[42080->42080] S=[57344->57344] Feb 25 02:51:04 openvpn[86654]: TCP/UDP: Preserving recently used remote address: [AF_INET]194.187.251.154:443 Feb 25 02:51:04 openvpn[86654]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Feb 25 02:49:44 openvpn[86654]: Restart pause, 80 second(s) Feb 25 02:49:44 openvpn[86654]: SIGUSR1[soft,ping-restart] received, process restarting Feb 25 02:49:44 openvpn[86654]: [server] Inactivity timeout (--ping-restart), restarting Feb 25 02:48:44 openvpn[86654]: VERIFY OK: depth=0, C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=server, emailAddress=info@airvpn.org Feb 25 02:48:44 openvpn[86654]: VERIFY EKU OK Feb 25 02:48:44 openvpn[86654]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication Feb 25 02:48:44 openvpn[86654]: Validating certificate extended key usage Feb 25 02:48:44 openvpn[86654]: VERIFY KU OK Feb 25 02:48:44 openvpn[86654]: VERIFY OK: depth=1, C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=airvpn.org CA, emailAddress=info@airvpn.org Feb 25 02:48:44 openvpn[86654]: TLS: Initial packet from [AF_INET]194.187.251.154:443, sid=7f656fd8 bb527714 Feb 25 02:48:44 openvpn[86654]: UDP link remote: [AF_INET]194.187.251.154:443 Feb 25 02:48:44 openvpn[86654]: UDP link local (bound): [AF_INET]192.168.0.20:0 Feb 25 02:48:44 openvpn[86654]: Socket Buffers: R=[42080->42080] S=[57344->57344] Feb 25 02:48:44 openvpn[86654]: TCP/UDP: Preserving recently used remote address: [AF_INET]194.187.251.154:443 Feb 25 02:48:44 openvpn[86654]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Feb 25 02:48:04 openvpn[86654]: Restart pause, 40 second(s) Feb 25 02:48:04 openvpn[86654]: SIGUSR1[soft,ping-restart] received, process restarting
-
I have not had a chance to setup my pfsense box to connect strickly to airVpn. I have been trolling the pfSense forums and read the wiki and seen where a few developers split from pfSense because it was becoming too commercial. I downloaded the image and installed in a VM but have not done much to it. Just wanted to know how many here would move to this version of firewall in leu of pfSense. Dont get me wrong im sticking with pfsense since pfSense_fan did one heck of a job on the guide, i was just wondering.