
InactiveUser
-
Content Count
214 -
Joined
... -
Last visited
... -
Days Won
28
Posts posted by InactiveUser
-
-
I don't understand the concept of the "Using AirVPN with Tor" section.
The AirVPN guide says "Does APP use Tor directly?" ..like the Tor browser. In the "Yes" direction it points away from the AirVPN server.
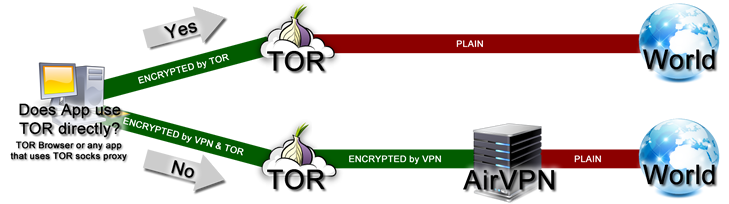
This graphic for "Using AirVPN with Tor" describes the following situation:
- you run a Tor client - let's say via Tor Browser. Tor will be listening on local port 9150
- you want to use AirVPN through Tor (meaning your traffic first goes through Tor, then exits through through AirVPN). To achieve that, you configure AirVPN to use Tor via port 9150.
Now the question is, what happens if some application connects to the internet? What "path" does the connection take?
That's the question the "arrows" try to answer.
"Does App use Tor directly" simply means: Has the app been configured to proxy through local port 9150?
Example A: Chromium browser. Does this app use Tor directly? No, that browser is not configured to use any proxies.
So, we have to follow the "No" arrow: Any of Chromium's connections will use the AirVPN connection, which in turn is tunneled through Tor. That's why that path is annotated "ENCRYPTED by VPN & Tor".
Example B: Tor Browser. Does this app use Tor directly? Yes, it does, because it's configured to use SOCKS5 proxy 127.0.0.1:9150. Local connections won't get tunneled through the VPN, which is why the arrow is annotated "(only) ENCRYPTED by Tor".
All this really means is: If you tunnel AirVPN through Tor Browser's Tor client, but then use that Tor Browser to browse the web, your request will still only go through Tor, but not through the VPN.
If an APP does not use Tor directly does this refer to an APP that uses Tor indirectly? What would an example of such an APP?
This would be my example A: If you tunnel AirVPN through Tor, most applications would make their connections through AirVPN, without knowing anything about AirVPN being tunneled through Tor first - thus, they would be using Tor indirectly.
Does this mean I can't use AirVPN with the Tor browser??
Not at all. You can hook up Tor and AirVPN in both directions; either tunneling AirVPN through Tor or tunneling Tor through AirVPN.
There's just that little "gotcha" that you can't tunnel AirVPN through Tor Browser and then expect your browsing in Tor Browser to also go through AirVPN.
This does not apply at all if you connect to AirVPN directly and then use Tor Browser on top (tunneling Tor through AirVPN).
Slightly off-topic but I'd claim that it usually makes more sense to tunnel Tor through AirVPN instead of the other way 'round, but that's entirely up to you.
spinmaster reacted to this -
2Girls1CPU, you're right, I should have worded it more precisely:
If you forward port X through AirVPN, don't forward that same port X on your router.
Or, to use a practical example: You have two applications that need a forwarded port:- a P2P application
- a game server
To keep your P2P usage private, you should only forward that port through AirVPN. If you also forwarded the P2P port on your router, you would allow people to connect to your P2P application directly, which would obviously go against the whole idea of tunneling your P2P application through a VPN.
At the same time, it's totally okay to open other ports on your router, say for a game server that you don't need or don't want to be tunneled through AirVPN. -
-
ATTENTION: This tutorial is out of date, incomplete and deprecated.A new and improved version of this tutorial can be found here: https://airvpn.org/topic/24349-how-to-airvpn-via-sslstunnel-on-android-678/
This thread is only kept online for historical reference.
Goal and obstacles
We want to use AirVPN's SSL tunneling mode on Android. SSL tunneling can be very useful, especially to defeat firewalls that block OpenVPN or SSH on a protocol level. On Android, a few obstacles have to be worked around:
a. there is no AirVPN Eddie client for Android.
Solution: We will use OpenVPN and stunnel directly.
b. there is no stunnel app in any Android appstore.
Solution: we will download the stunnel Android binary (provided by the stunnel project itself) and run it from the commandline.
c. Android does not allow us to execute any programs from the sdcard.
Solution: we will move stunnel to a special location (owned by the Terminal app), which will allow the Terminal app to execute stunnel.
d. stunnel wants to write to /tmp/, but there's no /tmp/ on Android.
Solution: we will modify the .ssl config file to change the pidfile location to a writable directory.
Software Requirements- Android 4.0 or newer (device does not have to be rooted)
- stunnel compiled for Android (FOSS), via project website
- OpenVPN for Android (FOSS), via F-Droid or Play Store
- Jack Palevich's Terminal Emulator for Android (FOSS), via F-Droid or Play Store
- a separate computer to download/edit the necessary config files and binaries (entirely optional, but easier than doing everything on the Android device itself)
Setup instructions
1. Generate config files with AirVPN's config generator- choose Linux
- pick one single server of your choice. I will use Nunki for this tutorial!
- for Connection Mode, choose SSL Tunnel, port 443 (visible after enabling Advanced Mode)
- enable Resolved hosts in .ovpn file
- leave all the other settings at their default values
- download and unzip the generated zip file
- this should result in an AirVPN folder, containing three files
2. Open the ssl config file (AirVPN_GB-Manchester_Nunki_SSL-443.ssl) in a text editor.
Find the line:pid = /tmp/stunnel4.pid
Change it to:
pid = /data/data/jackpal.androidterm/app_HOME/stunnel4.pid
Save and close the file.
3. In a text editor, create a new file with the following contents:
#!/system/bin/shcd /data/data/jackpal.androidterm/app_HOME./stunnel AirVPN_GB-Manchester_Nunki_SSL-443.ssl
Save it to a file named nunki (no file extension).
Put the file into the AirVPN folder, next to our other config files.
4. Download and unzip stunnel for Android from the stunnel website (stunnel-X.XX-android.zip)
Put the stunnel file (only the file, not the folder) into the AirVPN folder.
5. Make sure your AirVPN folder now contains the following files:AirVPN_GB-Manchester_Nunki_SSL-443.ovpnAirVPN_GB-Manchester_Nunki_SSL-443.sslnunkistunnelstunnel.crt
6. Copy the whole AirVPN folder to your Android's SD card.
The path should be:/sdcard/AirVPN/
7. Install OpenVPN for Android via F-Droid or Play Store and import the .ovpn config file located at
/sdcard/AirVPN/AirVPN_GB-Manchester_Nunki_SSL-443.ovpn
Don't try to connect just yet.
8. Install Terminal Emulator for Android, via F-Droid or Play Store
9. Open Terminal Emulator and successively run the following commands:cd
The simple cd command should take you to the app's home directory (/data/data/jackpal.androidterm/app_HOME).
This is where we need to put our config files and the stunnel binary. Let's move them over by running:mv /sdcard/AirVPN/* .
It's important to type every character correctly (commandline is case sensitive); the "*" is a wildcard expanding to all files in the AirVPN folder, and the "." is a placeholder for the current directory /data/data/jackpal.androidterm/app_HOME. Typing commands on Android is a big pain, so I try to keep them as short as possible!
Finally, we need to modify permissions for the binary and the script, allowing us to execute them:chmod 555 stunnel nunki
We should be ready to go!
Usage instructions
I. Open Terminal Emulator and run the following two commands:
cd
./nunki
A log message should appear: Configuration successful
Great! Keep the Terminal app running, but use the Home button to get out.
II. Open OpenVPN for Android and connect to the profile AirVPN_GB_Manchester_Nunki_SSL-443
Unless something went wrong, you should get Initialization Sequence Completed - great!
I recommend performing the usual leak tests and perhaps diving into OpenVPN's profile settings before relying on your configuration to work as you expect it to.
III. To disconnect:- Disconnect VPN in OpenVPN
- open Terminal Emulator, press VOLUME_DOWN + C to kill stunnel
- press the X button to close the terminal session
IV. If stunnel isn't shutdown properly, you may see an error if you try to run stunnel again:
[!] Error binding service [openvpn] to 127.0.0.1:1413[!] bind: Address already in use (98)[ ] Closing service [openvpn][ ] Service [openvpn] closed
This means stunnel is still running in the background. You can kill it by running:
killall stunnel
Footnotes
I successfully followed my own tutorial using:CyanogenMod 12.1 nightly (≈ Android 5.1)stunnel 5.23OpenVPN for Android 0.6.35 (F-Droid)Terminal Emulator 1.0.70 (F-Droid)
Testers welcome, especially if you're using different Android and software versions.
Credits:- Kevin Boone for the clever binary execution workaround.
-
I think there are two scenarios here:
1. the AP blocks on a protocol basis (anything other than HTTP/TLS/DNS on 80/443/53)
2. the AP blocks AirVPN entry IPs. This is certainly possible, but somewhat unlikely IMHO
Unless #2 is the case, you should be able to use OpenVPN over SSL. Are you able to do so on platforms other than Android?
I have successfully tinkered with stunnel on Android: it's a bit fiddly to set up but definitely doable. I'll provide a tutorial soon (later this day ortomorrow). edit: see below -
One thing that confused me was under the port forwarding rules on AirVPN client area, it says "Forwarded to 10.x.x.x". Why is this being forwarded to an IP with a 10. ip range? Should it not be forwarded to my internal IP? Or how exactly does that work?
The 10.x.x.x address you see in the client area is in fact your VPN-internal IP, assigned to you be the VPN server - much like your home router assigns you your internal LAN IP address.
Before we get into AirVPN port forwarding, let's consider this example to better understand how port forwarding works in general:
- your router has an internal IP 192.168.1.1 (internal means it's only reachable from within in your LAN)
- your router has an external IP 234.123.111.222 (assigned by your ISP. external means it's reachable from the internet)
- your PC has an internal IP 192.168.1.43
- there's an application running on your PC, it's listening on port 27364, on all available IPs (192.168.1.43)
If you want to access this application from the internet:
- your router will have to accept incoming connections on port 27364 on its external IP
- your router will have to forward those connections to internal IP 192.168.1.43, port 27364
- your PC will have to accept incoming connections on port 27364 on its internal IP
If these conditions are met, you can access 234.123.111.222:27364 from anywhere in the world and be forwarded to your PC at port 27364.
Now let's try to do that through AirVPN:
- the AirVPN server has an external IP 123.234.123.123 (reachable from the internet)
- your PC has an internal IP 192.168.1.43 (only reachable from within in your LAN)
- your PC has an internal VPN IP 10.x.x.x (only reachable from within the VPN, or more specifically, by you and by the AirVPN server)
- there's an application running on your PC, it's listening on port 27364, on all available IPs (both 192.168.1.43 and 10.x.x.x)
If you want to access this application from the internet:
- AirVPN's server will have to accept incoming connections on port 27364 on its external IP
- AirVPN's server will have to forward those connections to your internal VPN IP 10.x.x.x, port 27364
- your PC will have to accept incoming connections on that IP/port
Step 3 is taken care by configuring your PC's firewall accordingly, whereas both step 1 and step 2 are taken care by using AirVPN's forwarding in the client area.
It's very important to keep in mind: Do not ever open/forward any ports on your router if you're forwarding through AirVPN. It's not at all necessary and might potentially leak your IP through correlation attacks.
how safe is it to have a port forwarded like I am attempting while using AirVPN? Is there any potential for leaks?
Unless you also forward the same ports in your router, there shouldn't be any IP leakage concerns when forwarding ports through AirVPN.
That said, opening a port to the internet - with or without a VPN - is only as safe as the application that's listening on that port.
Guest and 2Girls1CPU reacted to this -
Answering your questions in reverse order:
3.) Finally, what does it mean to "open a port on your router?" Is that simply the same as port-forwarding, or is it a different situation?
It's a bit of both. Let's say you want to access your home server from the internet: You configure your server to listen for incoming connections on some port. But, by default, most routers will not accept incoming connections on any port. Opening a port refers to adding an exception to the router's firewall, allowing incoming connections on a specific port. But, the router will also need to forward connections to the actual recipient - your home server. Then, it's possible to contact YOUR_ROUTER'S_EXTERNAL_IP:open_port, and your router will forward the incoming connection to YOUR_HOMESERVER'S_INTERNAL_IP:open_port.
If we take that example and apply it to AirVPN forwarding: By forwarding a port in AirVPN's webinterface, you open that port in AirVPN's firewall (on the AirVPN exit server) and also forward it to your VPN-internal IP.
2.) Port-Forwarding: In what scenario would this be a good idea to use? ... Should I stop port--forwarding to become more anonymous?
People forward ports to be reachable from the outside - some want their P2P application to perform better, others might want to access their NAS from the internet. In any case, doing so over a VPN will improve your privacy - it is preferable to run a P2P application on a VPN port rather than directly on your home connection. If you have a good reason to be reachable from the outside, I don't see why you should stop port forwarding altogether.
However, there are security implications: The internet gets port-scanned around the clock. Whether you accept incoming connections on your home connection (router) or on your VPN connection does not make a difference - in both cases, the port will be exposed to the internet and thus discovered pretty much immediately. As a consequence, you want to make sure that you don't use weak authentication (bruteforceable passwords) on any ports exposed to the internet. For example, if you expose a local SSH server to the internet, you probably want to disable password authentication in favor of public key authentication.
Another worry would be "remote code execution" vulnerabilities. This basically means that a piece of software exposed to the internet may react unexpectedly to malformed (malicious) input, potentially causing information leakage or even full system compromise. For this reason, it's usually considered good practice to physically separate "sensitive" machines" from machines that are reachable from the internet.
For example, a bank would (so I hope) not run their webserver on the same machine that controls the security cameras or the vault's locks, knowing that their webserver might get compromised. In the same vein, you probably want to avoid exposing to the internet some outdated, vulnerable WordPress installation on a machine that also holds your private photos.1.) Say Joe Schmoe mistakenly logged into his personal email while connected to the VPN server and also while using Popcorn Time ... the question is whether or not this should be cause for true concern?
Your particular example doesn't warrant any true concern. Using VPNs means using a shared connection, which helps to prevent personal attribution or correlation. In all actuality, it is much more complicated, depending on how malicious your VPN provider is, who your adversary is and what parts of the internet they have access to.
In a similar vein, using a VPN for privacy reasons doesn't magically eradicate tracking - for example, Facebook doesn't care whether you use a VPN, they will happily track you regardless, so you still have to prevent that by practicing good browsing hygiene.
-
With a fast internet connection and tools like Masscan, it only takes anywhere from a few minutes to a few hours to scan the entire internet for open ports.
This means that you can expect every port that's open to the internet to see some unexpected traffic rather sooner than later. That, in itself, is nothing to worry about unless you're running vulnerable services or weak authentication.
You might have picked a port especially interesting to some scanners, which may explain why you haven't seen such activity on your other ports (yet).
The connection attempt you saw is not related to APNIC, they are just the registry for that block of IPs.
Here's the actual whois info for your IP:
netname: UNICOM-BJ
descr: China Unicom Beijing province network
Some trivia: Besides the private bulletin board on port 443 (~ 20.000 registered users), the Linux server at IP 221.220.155.170 runs a number of other services: SSH, FTP, VNC, Telnet, and a Synology web interface. Looks like someone's personal server to me, or perhaps a server shared by a number of people. The FTP server greets you with a somewhat amusing message:
220 PLS DISCONNECT IF U HAVE NO IDEA WHERE U R AT!
go558a83nk reacted to this -
Somewhat comparable to ufw, firewalld is just an interface to iptables. It allows for convenient higher-level rule constructs ("rich rules" and zones) but also allows direct iptables manipulation (so called "direct rules"). The actual rule syntax for direct rules is virtually identical to iptables.
There are two ways to manage firewalld - graphically (firewall-config) or on the commandline (firewall-cmd).
I compiled some notes and screenshots on firewalld usage in this post. Written last year, so some parts of my post concerning Air's config generator are no longer accurate or useful. Anything concerning firewalld and Fedora is still valid.More importantly though, read the man page for firewall-cmd and also understand the different between the runtime and permanent ruleset.
This is how I would "translate" your UFW rules:
(All systemctl and firewall-cmd commands need root privileges! drop to a root shell or use sudo)
1. First, make sure that the firewalld service is enabled and started:
systemctl enable firewalld systemctl start firewalld
2. Now configure your permanent rules:
firewall-cmd --direct --permanent --add-rule ipv4 filter FORWARD 0 -o tun+ -j ACCEPT firewall-cmd --direct --permanent --add-rule ipv4 filter FORWARD 0 -i tun+ -j ACCEPT firewall-cmd --direct --permanent --add-rule ipv6 filter INPUT 0 -j DROP firewall-cmd --direct --permanent --add-rule ipv4 filter INPUT 0 -i lo -j ACCEPT firewall-cmd --direct --permanent --add-rule ipv4 filter INPUT 1 -i tun+ -p tcp --dport 60002 -j ACCEPT firewall-cmd --direct --permanent --add-rule ipv4 filter INPUT 1 -i tun+ -p udp --dport 60002 -j ACCEPT firewall-cmd --direct --permanent --add-rule ipv4 filter INPUT 999 -j DROP firewall-cmd --direct --permanent --add-rule ipv6 filter OUTPUT 0 -j DROP firewall-cmd --direct --permanent --add-rule ipv4 filter OUTPUT 0 -o lo -j ACCEPT firewall-cmd --direct --permanent --add-rule ipv4 filter OUTPUT 0 -o tun+ -j ACCEPT firewall-cmd --direct --permanent --add-rule ipv4 filter OUTPUT 1 -p udp -m udp --dport 443 -d 178.162.198.40 -j ACCEPT firewall-cmd --direct --permanent --add-rule ipv4 filter OUTPUT 999 -j DROP
3. Runtime rules (omitting the --permanent switch) take effect immediately (but don't survive reboots etc.). Permanent rules, however, only take effect after restarting or reloading firewalld:
firewall-cmd --reload
4. To review your current runtime ruleset:
firewall-cmd --direct --get-all-rules
And your permanent ruleset:
firewall-cmd --direct --permanent --get-all-rules
5. One final task: Thoroughly test your ruleset to make sure it actually accomplishes what you had in mind.
rickjames and rainmakerraw reacted to this -
SoftEther is an interesting project, but it has quite a few factors working against it:
1. Considering that SoftEther is a crypto project, their websites do not inspire confidence:- F-rated SSL/TLS configuration on their main site
- no SSL/TLS at all on their download site
2. It hasn't been around long enough (~ 2014) - smaller user base, in flux, no code audits
3. SoftEther seemingly tries to support every protocol and feature under the sun, which is nice from a usability standpoint, but horrible from a security and code maintenance perspective. It goes against the current trend in secure software development (compare, for example, LibreSSL's approach)
4. AirVPN encourages exclusive use of FOSS on both servers and clients, whereas SoftEther encourages use of proprietary clients by supporting IPsec and MS-SSTP. I don't see much common ground. -
Well, looks like the corporate firewall doesn't like outbound UDP/443. Try TCP on 443, or SSL Tunneling.
And - don't get fired
-
don1234, a manual iptables/ufw setup only makes sense for people who don't use AirVPN's "Eddie" client software:
The lock symbol in the upper right corner indicates that you're using Eddie's network lock feature. The network lock will temporarily replace your iptables ruleset, which is why your ufw rules won't have any effect while Eddie is running with network lock enabled.
I think you have two options:- stop using ufw altogether
- keep using ufw with "Default Deny" Incoming & Outgoing
The latter would offer some additional protection for the times that the Eddie is not running / has not been started yet. There shouldn't be any complications as long you don't reload / re-enable ufw while Eddie is running. Just understand that once Eddie's network lock takes over, none of your ufw rules matter.
You can read more about Eddie's network lock here.
By the way, it looks like you're using Linux Mint Cinnamon - pressing the "print" key on your keyboard should put a screenshot in your "Pictures" folder! Alternatively, there's gnome-screenshot (which I'm pretty sure comes pre-installed) or shutter which offers more functionality.
-
The VPN connection seems fine, here's the actual problem:
I 2015.08.13 07:40:59 - Checking DNS
W 2015.08.13 07:41:02 - Error: NameResolutionFailure
The AirVPN client "tries to resolve domain names that are resolved only by our DNS server, to ensure that system is correctly querying our DNS server."
This check fails for some reason. Multiple users have recently reported similar problems so there might be a problem on Air's end.
Here's a quick workaround:
Go into Preferences, Advanced, DNS.- uncheck the box "Check if the tunnel uses AirVPN DNS"
- establish a VPN connection
- to check DNS manually, run this in a terminal window: cat /etc/resolv.conf
The file /etc/resolv.conf lists all your system's DNS servers and should only contain one of Air's DNS (10.X.0.1).
You should also check that file to see if your default (non-Air) DNS servers are restored after disconnecting from AirVPN.
rainmakerraw, Guest and rickjames reacted to this -
I agree with you about Purism, there are a lot of question marks and unfulfilled promises. I chose to include it in my (non-exhaustive) list because supporting any alternative vendor helps in the sense that it shows demand for alternatives. None of the projects I listed are truly free: the Novena comes closest, but even they had to reverse-engineer the 3d/video drivers.
Once we show demand in the millions, we can push hardware companies to build stuff that doesn't require reverse engineering. If Purism and all their publicity helps us get to such numbers - even if Purism are mostly hype with little substance - I'm fine with that.
-
Lenovo is now using rootkit-like techniques to install their software on clean Windows installs, by having the BIOS overwrite windows system files on bootup.
(from https://news.ycombinator.com/item?id=10039306)
Starting with Windows 8, Microsoft even facilitates this process:
in Windows 8+ any PC vendor can include an .EXE in Firmware/BIOS, and Windows will look for this on each boot, and run it right before you log in. This is called "Windows Platform Binary Table". This is something Windows does, and there is no way to turn this off. To me, this is the bigger story, because vendors may now start to use this method to install anything, making a clean windows install impossible.
(from https://news.ycombinator.com/item?id=10046957. More info on Windows Platform Binary Table)
My thoughts on this:
Proprietary software makes free and secure computing impossible.
"Just install Linux" doesn't fix anything: Your BIOS/UEFI still runs proprietary code, doing stuff behind your back and against your will.
"Just install a free BIOS (coreboot)" doesn't fix anything either: Recent intel CPUs are managed by a "separate CPU within the CPU". That separate CPU (Intel Management Engine) has its own, proprietary, irreplacable firmware.
It has DMA (= direct memory) access to the entire system memory and can access the networking adapters in a way transparent to the OS.
(from http://www.coreboot.org/Binary_situation)
Under the guise of providing new feautures for "convenience" and even "security" (see Secure Boot), hardware companies turn free computers into proprietary appliances.
What can we do?
- Support alternative vendors such as System76, ThinkPenguin and Purism
- Support "open hardware" projects such as Novena, with the hope of carving out a niche for truly free, open source and secure computing
- Support organizations such as FSF and EFF
- Engage politically! Lobby against freedom-inhibiting developments such as compulsory non-free routers
-
Actually, the AirVPN button we're used to in the Linux version (the one in the main application window) does not seem to be active in the OS X version. At least it did nothing when I tried it. You have to either press "cmd + ," or use the menu bar icon. Good tip though, regarding "start visible".
rainmakerraw reacted to this -
It's indeed a little confusing:
After launching the AirVPN client and entering your Mac user password, the AirVPN client does start - but it's minimized! Not even clicking on the dock icon will bring it up.
However, you will notice a new icon in your menu bar (right upper edge of your screen, next to the clock).
Click on the Air-themed icon (looks like a cloud in a circle). Select "Show Main Window" to bring up the main application window. Also notice that you can get to the separate "Preferences" pane by clicking on the menu bar icon. -
I'd argue the contrary: There's no such thing as some freedom of speech - you either have free speech or you don't. However, to touch on your bomb threat example, that doesn't mean that your exercise of free speech is without consequence. If your free speech causes direct damage, those you have damaged might rightfully take action against you. You can't use bomb threats as an argument against free speech.
Actually though, "censorship vs freedom of speech" is not the main issue at hand - at least in the western world.
What we're actually fighting against are total surveillance police states; the idea that we can't have any confidential or private means of communication. The idea that we have to abolish any rights to privacy and individual freedom, just for a wee bit of perceived security.
Not only is that an ideologically abhorrent idea, it has also proven to be an extremely ineffective strategy against crime and terror. Governments know that of course, they aren't stupid. They abuse the public's fear of terror to broaden their power over the plebs.
Absurd UK footnote: Huge budgets for GCHQ and CCTV, yet no money for actual police work.FromtheWalls reacted to this -
-
I probed all servers a few weeks ago: All servers added to AirVPN since 19 Jun 2015 use TLSv1.2. All other servers use TLSv1.
I don't think it makes much of a difference but it'd still be interesting to hear from staff what they changed in their infrastructure and whether they plan to upgrade the older servers as well.
-
I've had my fair share of battles with GNOME Dash and other docks like Plank.
Usually, all you have to do is right-click the icon and "Add to favorites" / "Keep in dock".
This option is missing for many "non-native" (Java, Mono) applications.
You can add Eddie to Dash if you do it like this:
But it doesn't work properly, you're going to end up with two separate icons:
It appears that docks have a hard time figuring out which Java/Mono windows belong to what application.
This often happens if the "WM_CLASS" property is different from the application's name.
I'll use the application "Android Studio" as an example.
Using the xprop tool, I find out:
WM_CLASS(STRING) = "sun-awt-X11-XFramePeer", "jetbrains-studio"
If I add the following line to the Android Studio's .desktop file ...
StartupWMClass=jetbrains-studio
... the GNOME window manager / dock will be able to correctly detect running instances and map them to the app's icon.
When I try this workaround with Eddie, "xprop" is unable to find the "WM_CLASS" property for the running Eddie instance. It is missing!
This is a common issue for Mono applications and would require Air's coders to write some C# to set the WM_CLASS.Probably something along those lines. I've opened an issue on Github to let them know.
-
To get a menu item for your compiled portable version, create a text file called AirVPN.desktop and place it in
~/.local/share/applications/
or:
/usr/share/applications/
Here are the contents of AirVPN.desktop as it is found in the Git repo (resources/debian/usr/share/applications/AirVPN.desktop)
[Desktop Entry]
Name=AirVPN
Comment=AirVPN
Exec=/usr/bin/airvpn
Icon=/usr/share/pixmaps/AirVPN.png
Terminal=false
Type=Application
Categories=GNOME;Network
You would only need to change Exec= and Icon= to your custom paths.
The icon AirVPN.png can also be found in your cloned Git repo, resources/debian/usr/share/pixmaps/AirVPN.png
-
I think your installer ("Yum Extender") is unable to install programs from a path that includes Japanese characters (ダウンロード).
Possible solution:
Move the rpm file into /home/eu/ and try the installation from there!
-
I'm a bit surprised to see Win10 discussed at all in this forum.
I understand that some people might not be in a position to abandon Windows but why the rush towards Windows 10? I mean, have you read their new privacy policies?
Before you say, "yeah, all those new features suck, I'll just turn them all off" - well, you can't:
Unless you have the "Enterprise" edition, you can't opt out of "diagnostic and usage data" collection.
https://i.imgur.com/iHge6RJ.jpghttps://twitter.com/adrianchm/status/626734160032477184
Before you say, "oh, but you can run tweak-tool XYZ or change this registry value, that'll turn it off completely" - how do you know? It's proprietary software. You're not in control whatsoever. Also, it only takes a small Windows update - that you can no longer opt out of either - to revert your manual changes. Why would they want to do that? Well, to quote Microsoft, data collection is now "vital to the operation of Windows", so you really have no reason to believe that your manual changes will stick.
I'm not sure what else Microsoft would have to do to make Windows look more like spyware than it already does. I really don't.


reserved ports
in Troubleshooting and Problems
Posted ...
Use the "Local port" option.
If you set the local port to 1337 and click "Add", you will get a random remote port XXXXX. AirVPN servers will then be listening on port XXXXX and forward incoming connections to your local port 1337.
In other words, if you connect to AirVPNServerIP:XXXXX, you will end up at YourLocalServer:1337.
This should work for all applications, only potential exception being P2P applications.