
go558a83nk
-
Content Count
2093 -
Joined
... -
Last visited
... -
Days Won
37
Posts posted by go558a83nk
-
-
Looks like things were only out for about 6 minutes assuming the outage I see was the fix. Thanks.
nevermind, now the fix is happening. -
https://www.asuswrt-merlin.net/about
I strongly encourage you to use Merlin firmware on an Asus router. With that you'll get actual options in your openvpn client setup, including an option to use the VPN DNS exclusively. That should prevent leaks. Even better is the policy routing capability. -
3 hours ago, kbps said:But Air have said that they will not increase the use of M247
It is always good to have diversity on a network.
They did not say they wouldn't add more M247. They said they had no plans to. That was some time ago and plans change. -
no way. then they couldn't truthfully say to law they don't know who did what from a server IP because they know it belongs to you.
Air4141841 reacted to this -
I'm already running wireguard client on my pfsense box to another VPN provider. If you need anybody to be testing from that environment give me a shout.
-
On 7/25/2021 at 8:25 PM, singh124 said:After playing around in the settings more, I have gotten my upload speed to reach 50mbps, but the download speed is only 10mbps? If the upload speed is high, that must mean that the speed is not being limited by the CPU? I'm not 100% sure I have everything set up correctly because since the DD-WRT guide was written it has been updated to add a lot more options that I had to try and figure the correct settings for.
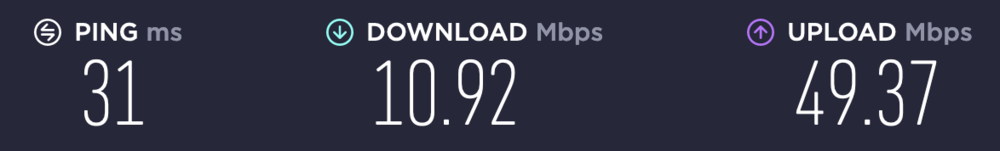
It's a good chance your ISP is traffic shaping when your upload is faster than download. Try TCP for transport protocol (not UDP) and see if that helps. -
AirVPN uses the same CA for their whole network same as Windscribe did and does.
Windscribe have updated theirs now due to this incident and now nobody would be in danger from this incident unless they haven't updated their manual configs...and in that case they wouldn't be able to connect to Windscribe's network
Individual server certs are different and my understanding is that those are unique to each server for AirVPN and Windscribe.
P.S. what did Windscribe omit in the current damage control? -
If in the openvpn config page you are selecting exclusive or preferred to the option to use VPN DNS then while connected to VPN the router automatically obeys the push message from the VPN server as to what DNS to use. That'll override the DNS settings you enter in the WAN setup page.
-
Yes, as the others have suggested a pfsense machine will do the job. But the reason i suggest the AC86 is because it and a few others routers have a CPU that has AES-NI for fast openvpn. So you have a little more user friendly way to get pretty good speeds.
-
The AC86 (eightysix) would be the choice, with Merlin Asus firmware.
-
What data cipher is being used now? Which one was being used?
I mean, look in the system log to see what actually happened.
It sounds like you have an ac86 or one of the asus routers with AES-NI. So, you maybe need to make sure to use an AES encryption though chacha20 (available with openvpn 2.5) may be fast too.
Is it possible that AES-NI acceleration has been disabled? Have you asked this in Merlin support forum? -
Use the network lock in Eddie also.
What do you mean the option to bind to TAP adapter isn't available to you? The adapter isn't there or the option doesn't exist at all? -
You're not artificially being throttled by Air. That's just the way things are with openvpn with limitations by CPU, network, internet, etc. A client on the usual 1gbit/s server will see only about 500mbit/s download max because the server throughput limit is 1gbit/s inbound and outbound combined.
Air does have at least 1 server that's 10gbit/s. Try it to see if it's any better for you.superuser1970 reacted to this -
You can get around this limitation by creating a new device, one device for each device you connect. I do think you'll have to log out and log back into eddie for it to see the new device options. https://airvpn.org/devices/
-
5 minutes ago, salacronix said:
Well then that would point to a problem with the AirVPN config generator. In the config it specifically shows the remote as "nl.vpn.airdns.org". Will that return the wrong list of servers?
No, the problem is with you unable to follow directions.
In the tutorial, the first directive in the "generate AirVPN certificates" section is to enable advanced mode. Have you turned on advanced mode in the config generator? -
5 minutes ago, salacronix said:I appreciate you chiming in, but I was referencing the guide at https://nguvu.org/pfsense/pfsense-baseline-setup/
In the setup for the VPN the screen shot shows "TLS Encryption and Authentication". That does not work. Only "TLS Authentication" works.
Additionally for Auth digest algorithm he shows SHA512 , that does not work. Auth digest algorithm only works with SHA1 (160 bit).
If you find this not to be the case, then there is something definitely wrong with PFsense 2.5. and I should probably look for another firewall.
The guide is for a tls-crypt setup where those settings are what work. What you're missing is that you need to connect to an entry IP 3 or 4. The guide actually says " please double check you select an appropriate ‘tls-crypt, tls1.2’ end point. This is a common source of problems." -
Also, now that pfsense has openvpn 2.5 you might try a switch to chacha20 as "data encryption algorithm" as it might be faster for you than what you were using.
Even on my system that was fast with AES-256-GCM because of AES-NI, chacha20 is for some reason faster. I think it has more to do with networking and not CPU ease. -
Remove anything that isn't actually needed in the custom options, or anything that you didn't actually put there. I had the same problem and there were lines in custom options that I were not something I put in.
-
Your web server is back to TLS 1.2 again.

https://www.ssllabs.com/ssltest/analyze.html?d=airvpn.org&s=5.196.64.52&hideResults=on -
On 1/27/2021 at 2:44 AM, Umpa said:
Can you post documentation on how to do this - this sounds like something I need to do.On 2/17/2020 at 2:24 PM, go558a83nk said:For plex remote access you either need to forward the port through the VPN or you need to setup, in eddie, plex.tv to go outside the VPN tunnel.
in the settings of Eddie there should be a section for adding routes...in the VPN tunnel or outside the VPN tunnel. -
10 minutes ago, rob77 said:Would you mind telling me what Data Encryption Algorithms and Auth digest algorithm yours is set at? I have mine on AES-256-GMC but cannot set it to anything above SHA1. It just will not connect.
Cheers
sha1 is what you use with entry IP 1 and 2. sha512 (and tls encryption and authorization) is used for entry IP 3 and 4 configs. -
I'd say that your stunnel isn't actually running or your openvpn setup is not pointing to the port at which stunnel is listening.
-
There's no need to manually set 10.4.0.1. Just tell set your VPN client settings to use the pushed DNS exclusively. It'll change it automatically upon connect. Use OpenNIC for the DNS settings in the WAN section. That'll allow you to resolve domains when the VPN isn't connected and for devices that don't go through the VPN if you use the policy routing option.
-
3 hours ago, Staff said:@NLVPN
Hello!
Also consider that you can have robust load balancing with a pfSense (and in general *BSD) box and AirVPN:
https://nguvu.org/pfsense/pfsense-multi-vpn-wan/
Kind regards
Yes, this is what I do for downloading big files. It's rare that I'm able to hit that 500+ mark from a single connection both because my ISP and intermediate networks just aren't "allowing" it, or because the VPN server isn't up to it. But when spread out it's much easier. That said, some endpoint servers won't allow you to multi wan and it won't help with bittorrent either.



upload 70Mbps on a 200Mbps fiberspeed, downloadspeed is ok.
in Troubleshooting and Problems
Posted ...
You may have a typo if I'm understanding your intent correctly.